between Switch A and Switch B is untrusted, the ARP packets from Host 1 are dropped by Switch B.
Connectivity between Host 1 and Host 2 is lost.
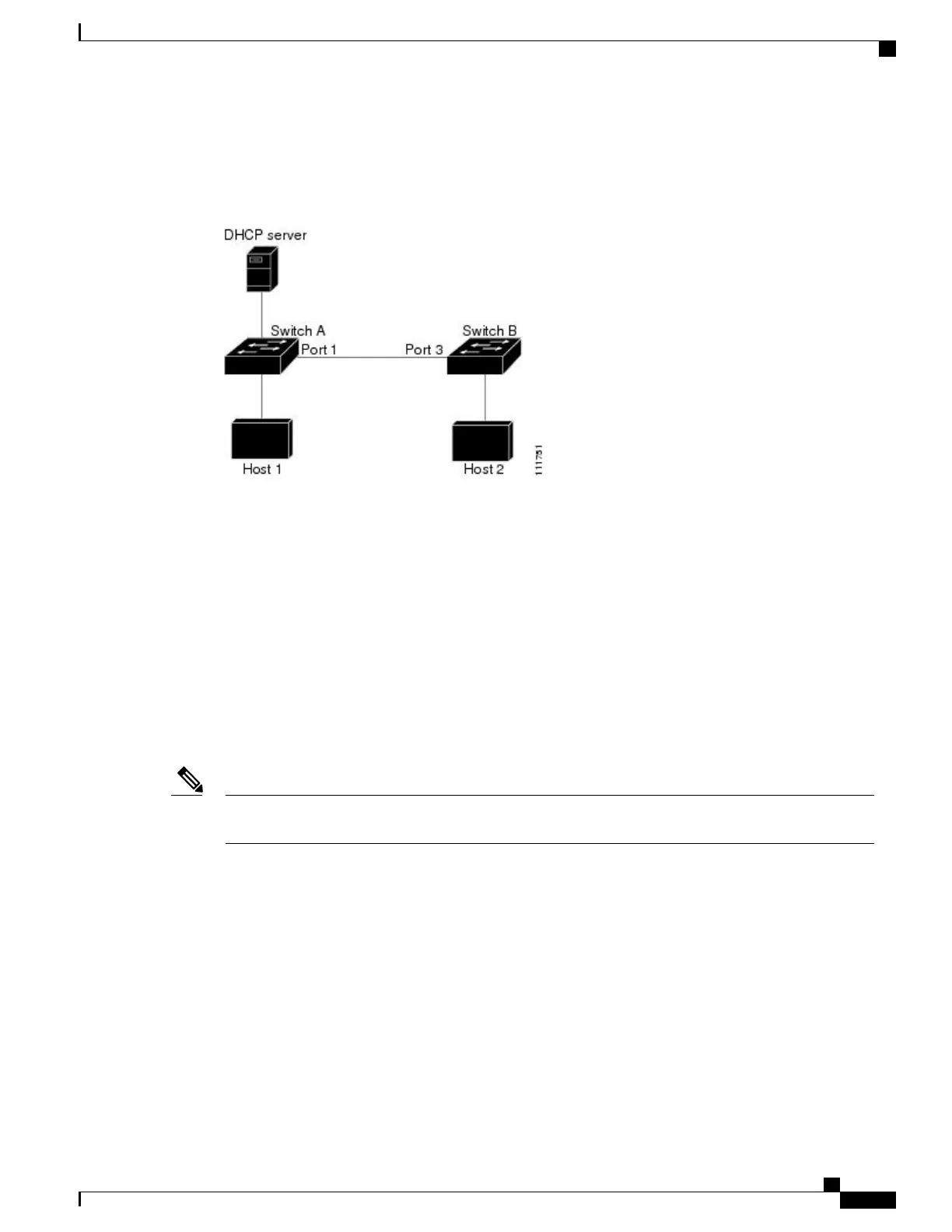
Figure 16: ARP Packet Validation on a VLAN Enabled for Dynamic ARP Inspection
Configuring interfaces to be trusted when they are actually untrusted leaves a security hole in the network. If
Switch A is not running dynamic ARP inspection, Host 1 can easily poison the ARP cache of Switch B (and
Host 2, if the link between the switches is configured as trusted). This condition can occur even though Switch
B is running dynamic ARP inspection.
Dynamic ARP inspection ensures that hosts (on untrusted interfaces) connected to a switch running dynamic
ARP inspection do not poison the ARP caches of other hosts in the network. However, dynamic ARP inspection
does not prevent hosts in other portions of the network from poisoning the caches of the hosts that are connected
to a switch running dynamic ARP inspection.
In cases in which some switches in a VLAN run dynamic ARP inspection and other switches do not, configure
the interfaces connecting such switches as untrusted. However, to validate the bindings of packets from
nondynamic ARP inspection switches, configure the switch running dynamic ARP inspection with ARP
ACLs. When you cannot determine such bindings, at Layer 3, isolate switches running dynamic ARP inspection
from switches not running dynamic ARP inspection switches.
Depending on the setup of the DHCP server and the network, it might not be possible to validate a given
ARP packet on all switches in the VLAN.
Note
Rate Limiting of ARP Packets
The switch CPU performs dynamic ARP inspection validation checks; therefore, the number of incoming
ARP packets is rate-limited to prevent a denial-of-service attack. By default, the rate for untrusted interfaces
is 15 packets per second (pps). Trusted interfaces are not rate-limited. You can change this setting by using
theip arp inspection limitinterface configuration command.
When the rate of incoming ARP packets exceeds the configured limit, the switch places the port in the
error-disabled state. The port remains in that state until you intervene. You can use the errdisable recovery
global configuration command to enable error disable recovery so that ports automatically emerge from this
state after a specified timeout period.
Catalyst 2960-XR Switch Security Configuration Guide, Cisco IOS Release 15.0(2)EX1
OL-29434-01 199
Configuring Dynamic ARP Inspection
Rate Limiting of ARP Packets
 Loading...
Loading...











