Security: SSH Client
Protection Methods
Cisco Small Business 200 Series Smart Switch Administration Guide 281
21
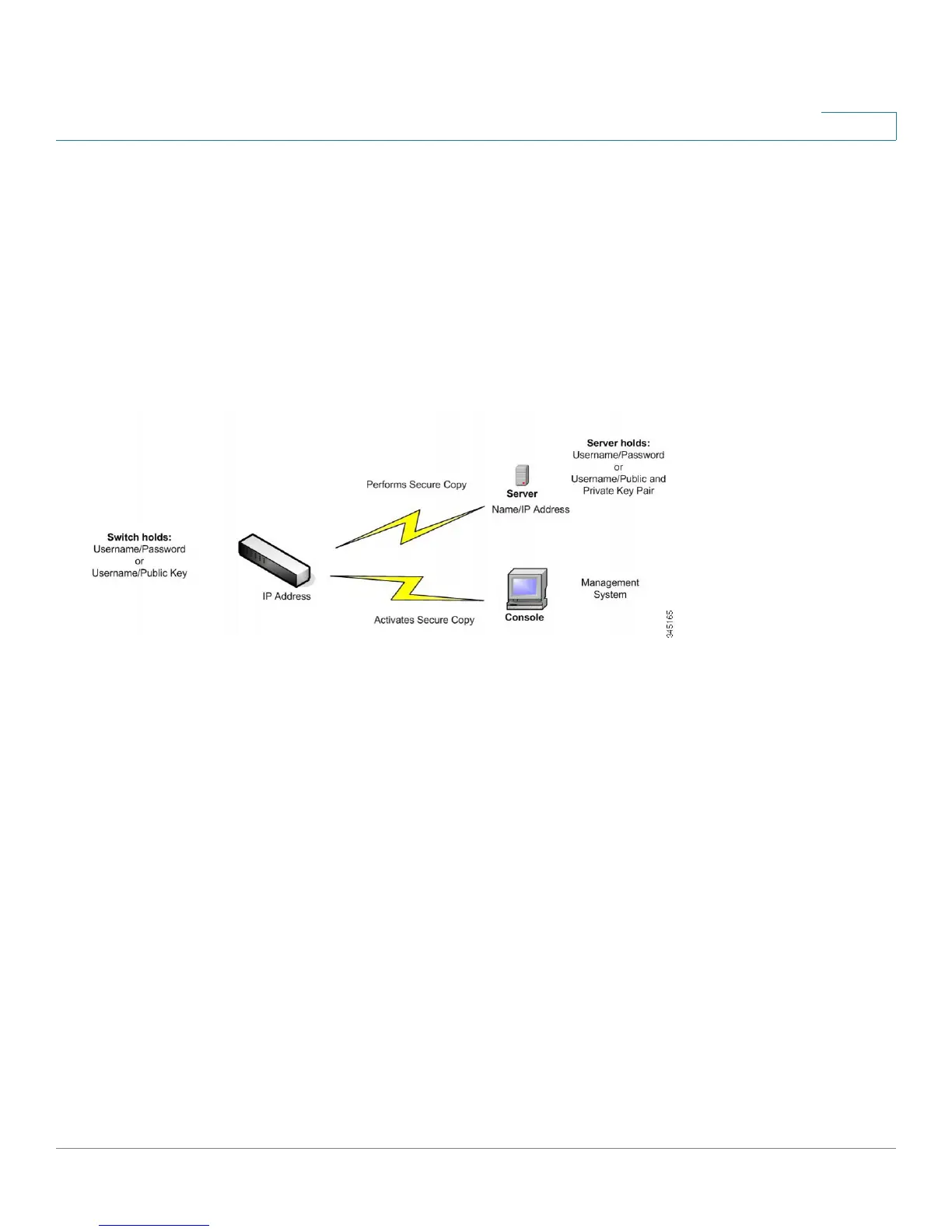
When files are downloaded via SCP, the information is downloaded from the SCP server to the device via a
secure channel. The creation of this secure channel is preceded by authentication, which ensures that the
user is permitted to perform the operation.
Authentication information must be entered by the user, both on the device and on the SSH server, although
this guide does not describe server operations.
The following illustrates a typical network configuration in which the SCP feature might be used.
Typical Network Configuration
Protection Methods
When data is transferred from an SSH server to a device (client), the SSH server uses various methods for
client authentication. These are described below.
Passwords
To use the password method, first ensure that a username/password has been established on the SSH
server. This is not done through the device’s management system, although, after a username has been
established on the server, the server password can be changed through the device’s management system.
The username/password must then be created on the device. When data is transferred from the server to
the device, the username/password supplied by the device must match the username/password on the
server.
Data can be encrypted using a one-time symmetric key negotiated during the session.
Each device being managed must have its own username/password, although the same username/
password can be used for multiple switches.

 Loading...
Loading...











