Managing Network Security
EPICenter Concepts and Solutions Guide
120
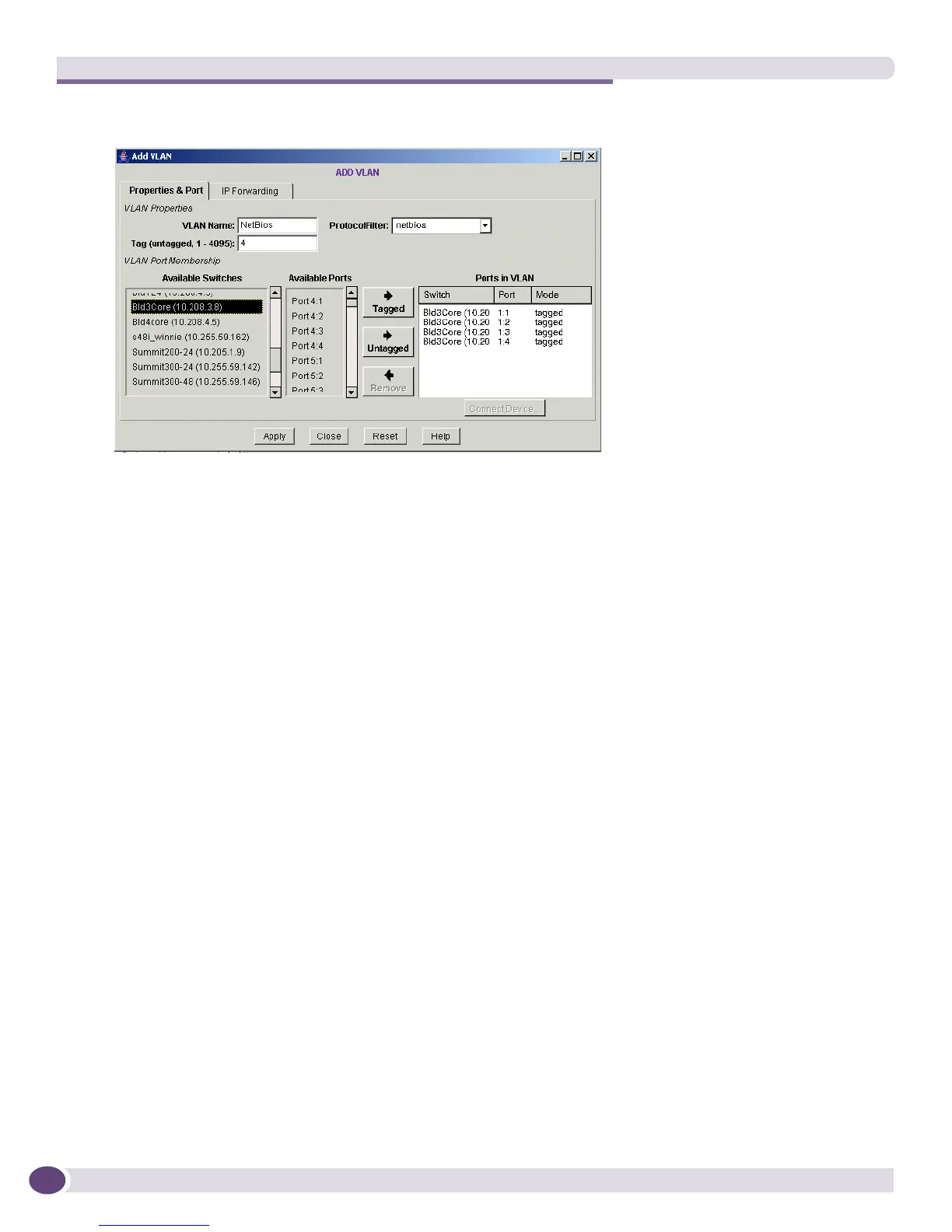
Figure 53: Creating NetBIOS VLAN
See Chapter 5 “Managing VLANs” for more information about how EPICenter can help you manage
the VLANs on your network.
Using IP Access Lists
IP access lists (ACLs) determine what traffic is allowed on your network. ACLs use a set of access rules
you create to determine if each packet received on a switch port is allowed to pass through the switch,
and if so, at what priority and with how much bandwidth, or is denied (dropped) at the ingress port.
ACLs can be use to regulate both the type of traffic, the priority and minimum and maximum
bandwidth (via a QoS profile), and the source or destination of the traffic allowed on your network.
This is done by setting up access lists for the traffic, and determining if the traffic is allowed or denied
on the network, and if allowed, what QoS Profile applies. The access list controls can be set based on
the source or destination addresses. Refer to the ExtremeWare Software User Guide for complete
description and syntax for ACLs.
You should use access lists to provide basic controls on what kind of traffic you will allow on your
network. Without access lists, any traffic from anywhere can traverse your entire network. For example,
you use access lists to allow HTTP traffic across your network, but deny online gaming traffic.
Designing IP Access Lists Through Policies
Access lists are configured based on policies created through EPICenter. Before creating these policies,
you need to translate your security requirements into appropriate IP or security policies. To design your
access list requirements, follow these steps:
1 Determine what traffic types you want to allow and deny on your network. Be sure to include both
protocol types and source or destination addresses you need to allow or block. This should be based
on your corporate security guidelines and the acceptable use guidelines for the hosts on your
network.
2 Set your access control requirements in order of precedence. Traffic will be checked against access
lists in order, using the first matching access list as the control for that traffic pattern.

 Loading...
Loading...