Policy Manager Overview
EPICenter Concepts and Solutions Guide
166
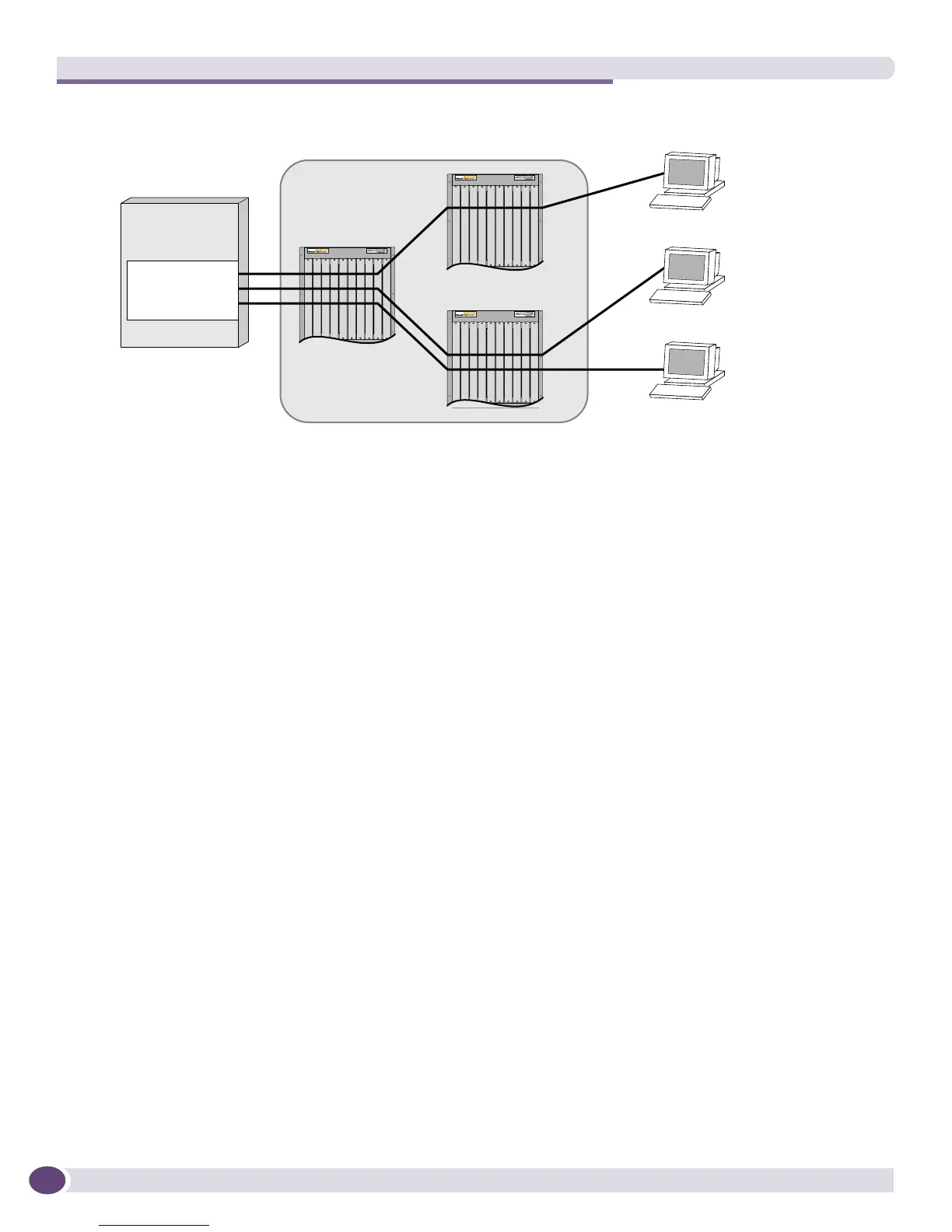
Figure 73: IP QoS policy
Unlike the VLAN and source port policy types, Security and IP policies specifies a traffic flow between
two endpoints, and that traffic may travel through multiple network devices between those two
endpoints. Thus, to protect the specified traffic along the entire route, the policy should be implemented
on all the devices between the two endpoints. This is done by including these devices in the policy
scope. On each device along the route, the traffic is identified based on the endpoint definitions (the IP
address, protocols, and L4 ports), and is assigned to the specified QoS profile on that device.
The diagrams shown in Figure 74 illustrate how the traffic flows are generated for the example shown
in Figure 73.
The EPICenter Policy Manager lets you specify the policy traffic flow in terms of named components.
Therefore, you can specify server “Iceberg” as the server endpoint, and clients “A,” “B,” and “C” as
client endpoints. In addition, you can indicate that the traffic from the server should be filtered only to
include traffic generated by the Baan application, which translates to TCP traffic originating from L4
port 512. Ports are not specified for the clients.
Because they were defined through the EPICenter Grouping Manager, the Policy Manager can translate
these high-level server and client names to IP addresses. Based on this information as well as the
specified traffic direction, the Policy Manager generates the set of traffic flows shown in the table at the
bottom of Figure 74. The diagram shows the steps involved in translating from the high-level objects
(host name and service) to IP addresses and L4 ports and protocols, to a set of traffic flows used in
policy rules.
XM_016
Application:
Baan
(TCP, L4 port 512)
Server
Iceberg
Policy scope
Client C
Client B
Client A

 Loading...
Loading...