214 MDS Orbit MCR/ECR Technical Manual MDS 05-6632A01, Rev. F
- Stale - The neighbor is not currently unreachable. The unit reevaluates the state of stale
neighbors the next time it attempts to send traffic to them.
- Delay - The neighbor was formerly in a Stale state, and a recent attempt to send traffic to
it failed.
- Probe - The neighbor was formerly in a Delay state, and the unit is currently sending
ARPs/neighbor solicitations in an attempt to reach the neighbor.
Access Control List (Packet Filtering / Firewall) 3.8.8
Understanding
Packet filtering is a component of the firewall service. It can be used to permit or deny incoming or
outgoing traffic on an interface.
Packet filtering allows configuring and applying a packet filter (also called Access Control List, or ACL)
to incoming or outgoing traffic on an interface. A filter is a set of one or more rules. Each rule consists of
two parts:
Matching criteria that a packet must satisfy for the rule to be applied. Matching criteria consists of
various parameters like protocol, source/destination addresses and ports etc.
Actions that specify what to do with the packet when the matching criteria is met, for example, to
drop or accept the packet.
The filter can then be applied to an interface in the incoming or outgoing direction. Typically, different
filters are applied in the incoming and outgoing direction on an interface. For example, a filter applied to
the cellular (WAN) interface of the MCR is typically very restrictive, permitting only a small set of traffic
to enter the unit, whereas outgoing filter might permit all outgoing traffic etc.
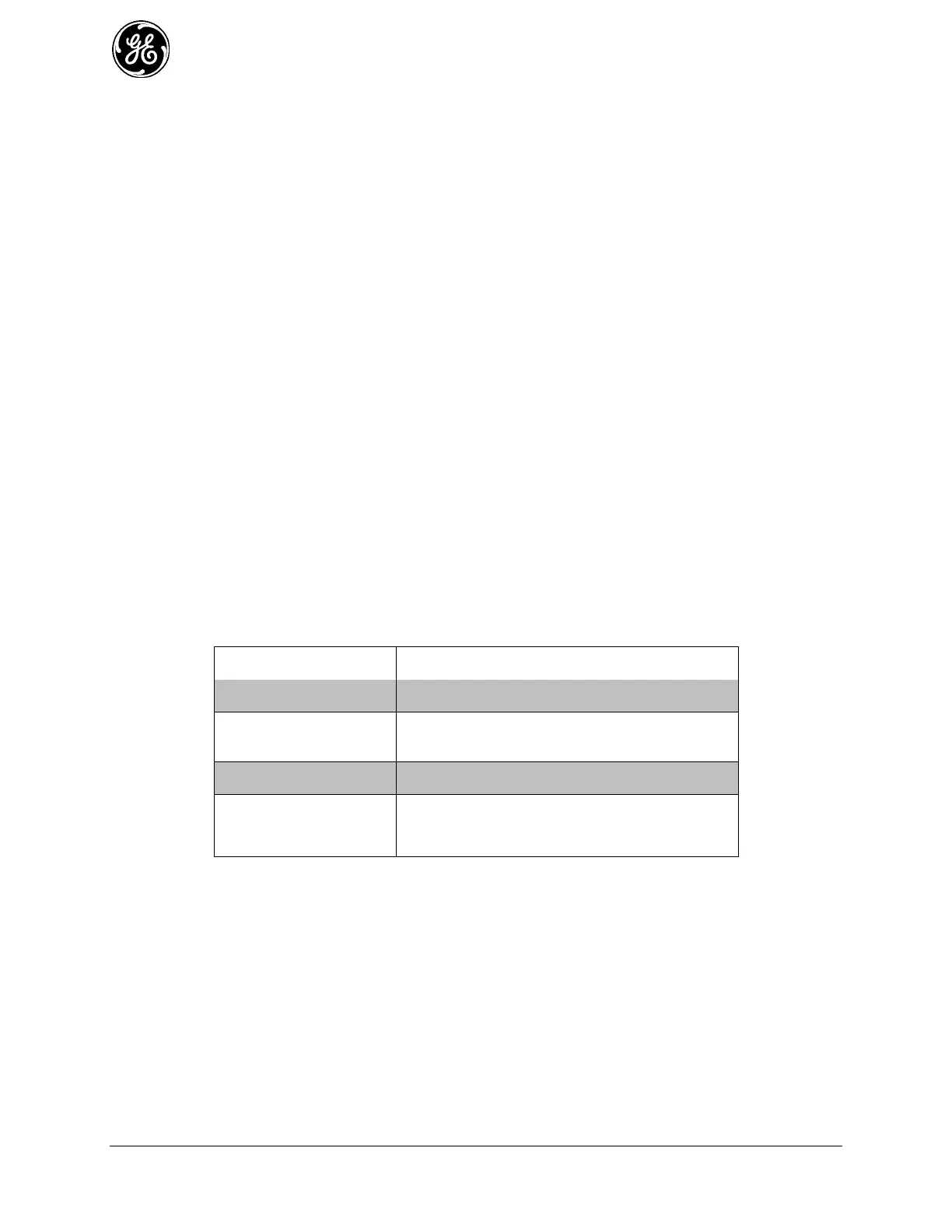
The MCR includes the four pre-configured filters shown below:
Table 3-18. Predefined Filter Names and Default Settings
Allow ingress of all traffic
Allow ingress of ICMP traffic, DNS response traffic,
drop all else
Allow egress of all traffic
Allow traffic originating from the interface to which this
filter has been applied and from addresses specified
in LOCAL-NETS address-set (typically LAN network).
If the Firewall service is enabled, filters specifying ingress and egress rules must be applied to each
network interface on the device. The MCR's network interfaces allow no traffic to pass unless a filter is
applied to each one allowing them to do so. Except for the Cell, each network interface on the MCR is
preconfigured with IN_TRUSTED as an input filter, and OUT_TRUSTED as an output filter. This allows
all traffic to enter and exit the unit.
The diagrams below provide a simplified view of packet flow for various categories of traffic flows going
in and out of the MCR unit when packet filtering is enabled.
Figure 3-120 shows the flow of packets terminating at the unit, such as device management traffic using
SSH or NETCONF protocol terminating at local device management process within the unit.

 Loading...
Loading...