364 MDS Orbit MCR/ECR Technical Manual MDS 05-6632A01, Rev. F
3.9 Public Key and Certificates
Certificate Management and 802.1X Authentication 3.9.1
Understanding
A RADIUS server can be configured for 802.1X device authentication on the on the Orbit MCR;
WPA/WPA2-Enterprise privacy mode on the Wi-Fi or EAP security mode on the NX915 and LNxxx
radio interfaces.
The device uses x509 public certificates and private keys for the following services:
Secure Reprogramming
Syslog over TLS
IPsec VPN/IMA (when using pub-key, EAP-TLS or EAP-TTLS based authentication)
WiFi (when doing EAP-TLS authentication in station mode)
NxRadio (when security-mode is set to EAP on Remote units)
Certificates can be imported into the device using one of two methods: manually or via SCEP. Note that
certificates for secure reprogramming can only be imported using the manual method.
The device can import certificates that are in DER, PEM, or encrypted PEM format. The device can
import private keys that are in DER, PEM or encrypted PEM.
Private Keys 3.9.2
The device can manually import private keys, or can generate a new private key of a specified length.
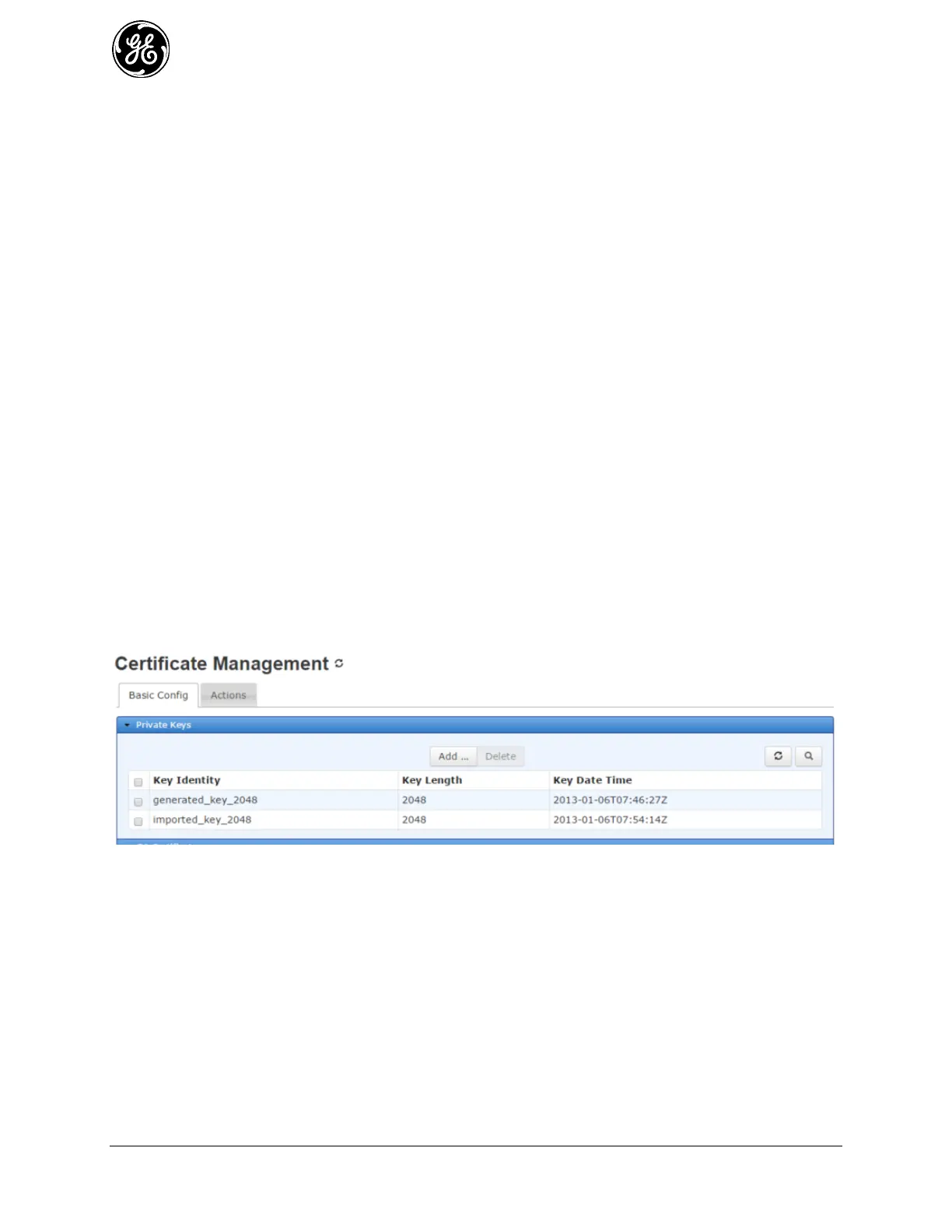
From the WebUI, navigate to Certificate Management / Basic Config. The Private Keys section shows
the private keys currently loaded into the device.
Figure 3-229. Private Keys
Ensure the CLI is in operational mode and follow the example below to view installed private keys:
> show pki private-keys show-all
KEY
KEY IDENTITY LENGTH KEY DATE TIME
---------------------------------------------------------------------------------------------------
generated_key_2048 2048 2013-01-06T07:46:27Z
imported_key_2048 2048 2013-01-06T07:54:14Z
Deleting
The device may delete a private key by clicking the Delete button on the web user interface or using the
CLI in operational mode. See the following example for deleting private keys via the CLI:
> request pki private-keys delete key-identity generated_key_2048

 Loading...
Loading...