228
1. A PKI entity submits a certificate request to the RA.
2. The RA verifies the identity of the entity and sends a digital signature containing the identity
information and the public key to the CA.
3. The CA verifies the digital signature, approves the request, and issues a certificate.
4. After receiving the certificate from the CA, the RA sends the certificate to the certificate
repositories and notifies the PKI entity that the certificate has been issued.
5. The entity obtains the certificate from the certificate repository.
PKI applications
The PKI technology can meet security requirements of online transactions. As an infrastructure, PKI
has a wide range of applications. Here are some application examples.
• VPN—A VPN is a private data communication network built on the public communication
infrastructure. A VPN can use network layer security protocols (for example, IPsec) in
conjunction with PKI-based encryption and digital signature technologies for confidentiality.
• Secure emails—PKI can address the email requirements for confidentiality, integrity,
authentication, and non-repudiation. A common secure email protocol is Secure/Multipurpose
Internet Mail Extensions (S/MIME), which is based on PKI and allows for transfer of encrypted
mails with signature.
• Web security—PKI can be used in the SSL handshake phase to verify the identities of the
communicating parties by digital certificates.
Support for MPLS L3VPN
An enterprise might have multiple branches in different VPNs. PKI support for MPLS L3VPN is
required if users in different VPNs request certificates from the CA server in the headquarters VPN.
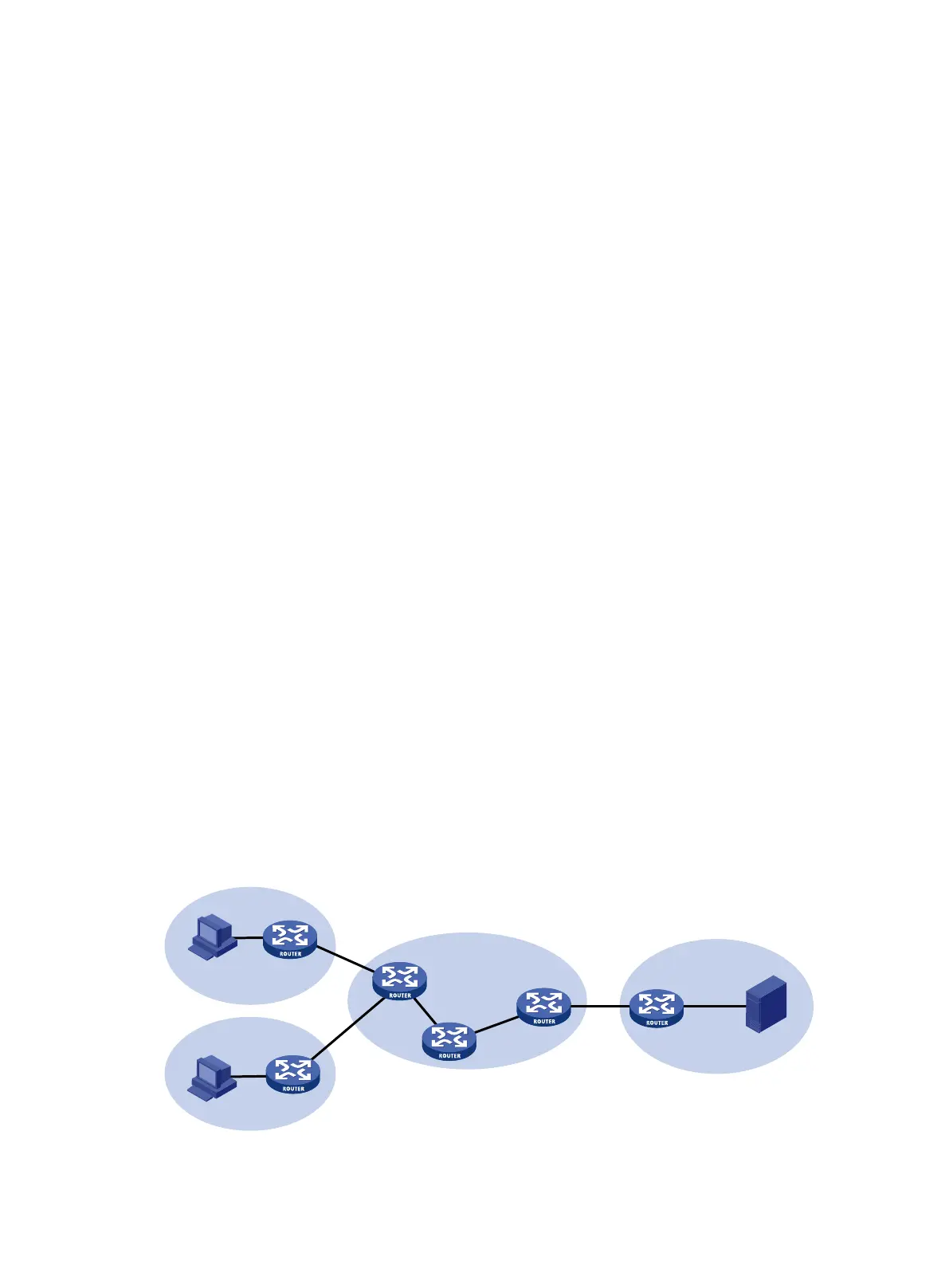
As shown in Figure 78, the PKI entity in VPN 1 requests a certificate from the CA server in VPN 3 in
the following workflow:
1. The PKI entity submits a certificate request to the CA server.
2. The PE device that connects to the PKI entity transmits the request to the CA server through
MPLS L3VPN.
3. The CA server verifies the request and issues the certificate.
4. The PE device that connects to the CA server transmits the certificate to the PKI entity.
For information about MPLS L3VPN, see MPLS Configuration Guide.
Figure 78 PKI support for MPLS L3VPN
P
MPLS backbone
PE
PE
CE
CE
CE
VPN 1
VPN 2
VPN 3
CA server
Host
Host
PKI entity

 Loading...
Loading...



















