464
Operating mechanism for device-oriented mode
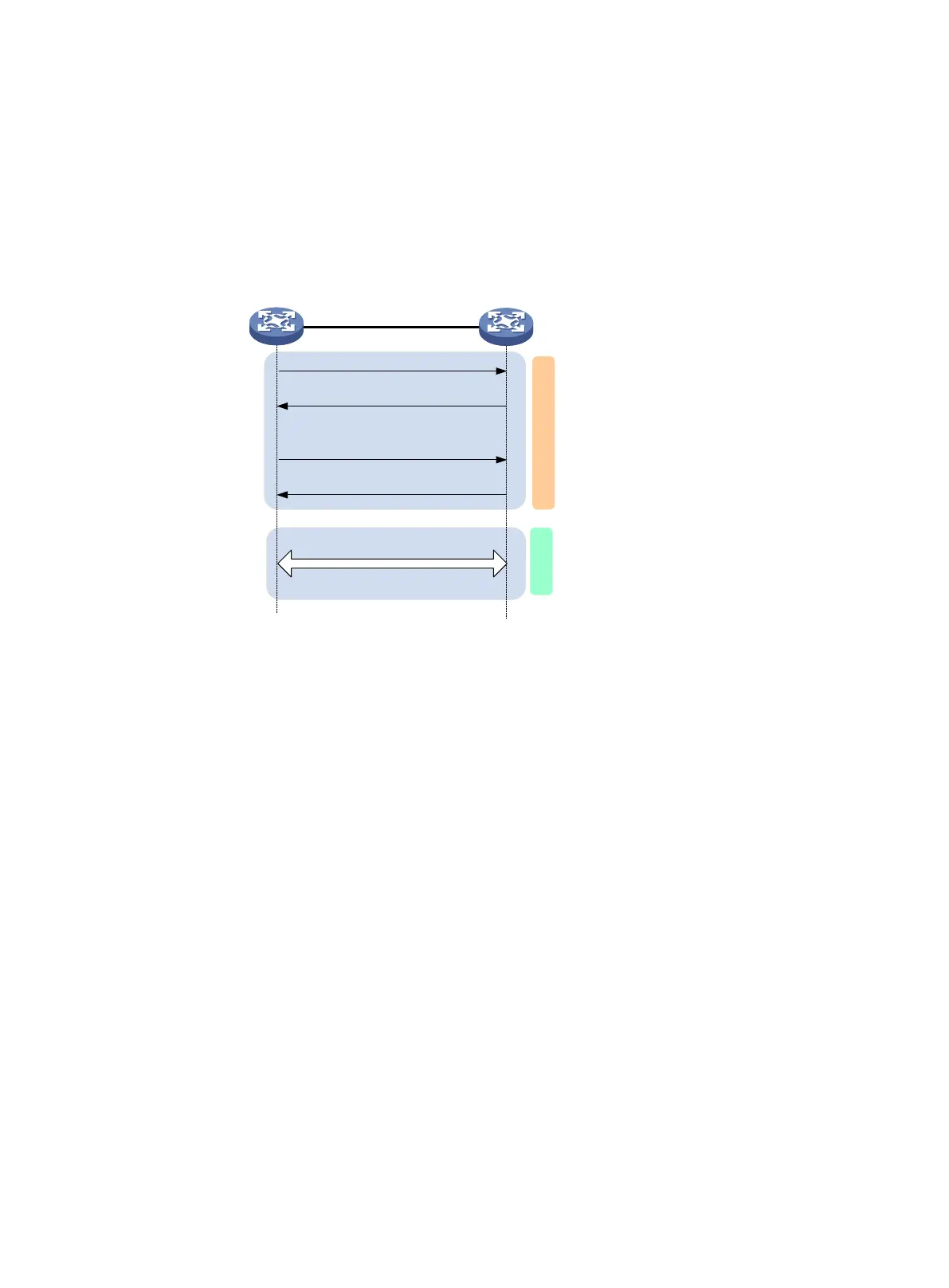
As shown in Figure 141, the devices use the configured preshared keys to start the session
negotiation.
In this mode, the session negotiation, secure communication, and session termination processes are
the same as the processes in client-oriented mode. However, MACsec performs a key server
selection in this mode. The port with higher MKA key server priority becomes the key server, which is
responsible for the generation and distribution of SAKs.
Figure 141 MACsec interactive process in device-oriented mode
Protocols and standards
• IEEE 802.1X-2010, Port-Based Network Access Control
• IEEE 802.1X-2006, Media Access Control (MAC) Security
Compatibility information
Feature and hardware compatibility
MKA cannot be enabled on MACsec-incapable interfaces. In this switch series, the following
interfaces are MACsec-capable:
• The leftmost eight interfaces (GigabitEthernet x/0/1 through GigabitEthernet x/0/8) on each
switch.
• The interfaces on HPE 5130/5510 10GBASE-T 2-port Module(JH156A), HPE 5130/5510
10GbE SFP+ 2-port Module(JH157A) interface modules installed on switch models except
HPE 5510 24G SFP 4SFP+ HI 1-slot Switch(JH149A). The interface modules do not support
hot swapping if MKA is enabled on such interfaces.
Feature and software version compatibility
The MACsec feature is available in Release 1121 and later.
EAPOL
EAPOL-MKA: key server
.......
Device A
EAPOL-MKA: MACsec capable
EAPOL-MKA: key name, SAK
EAPOL-MKA: SAK installed
Session
negotiation
M
K
A
Secure
communication
M
A
C
s
e
c
Secured frames
Device B

 Loading...
Loading...



















