477
Configuring ND attack defense
Overview
IPv6 Neighbor Discovery (ND) attack defense is able to identify forged ND messages to prevent ND
attacks.
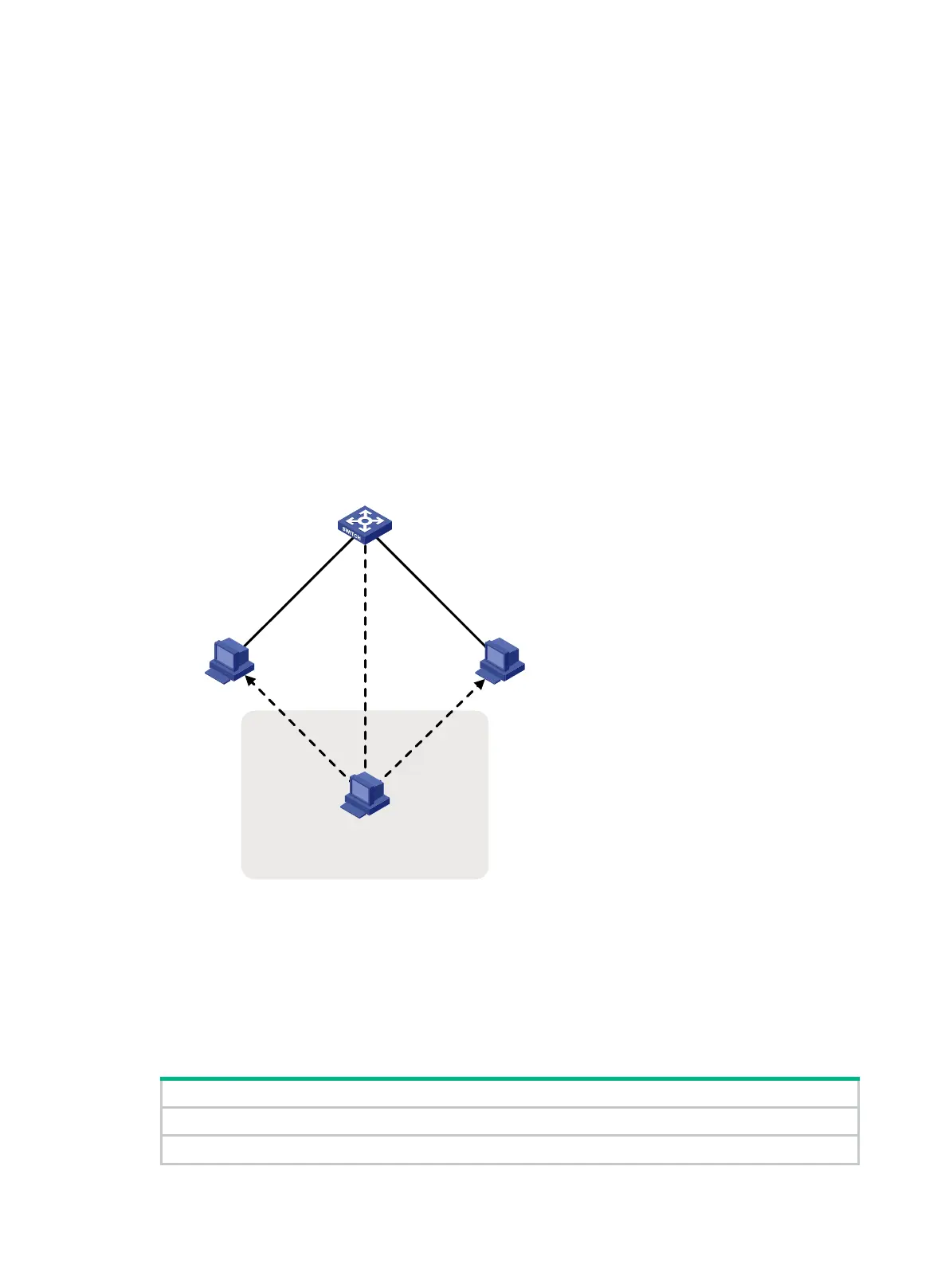
The IPv6 ND protocol does not provide any security mechanisms and is vulnerable to network
attacks. As shown in Figure 144, an attacker can send the following forged ICMPv6 messages to
perform ND attacks:
• Forged NS/NA/RS messages with an IPv6 address of a victim host. The gateway and other
hosts update the ND entry for the victim with incorrect address information. As a result, all
packets intended for the victim are sent to the attacking terminal.
• Forged RA messages with the IPv6 address of a victim gateway. As a result, all hosts attached
to the victim gateway maintain incorrect IPv6 configuration parameters and ND entries.
Figure 144 ND attack diagram
Feature and software version compatibility
The ND attack defense feature is available in Release 1121 and later.
ND attack defense configuration task list
(Optional.) Configuring ND attack detection (applicable to access devices)
(Optional.) Configuring RA guard (applicable to Layer 2 access devices)
Device
Host A
Host B
IP_B
MAC_B
IP_C
MAC_C
Host C
Forged ND
messages
Forged ND
messages

 Loading...
Loading...



















