291
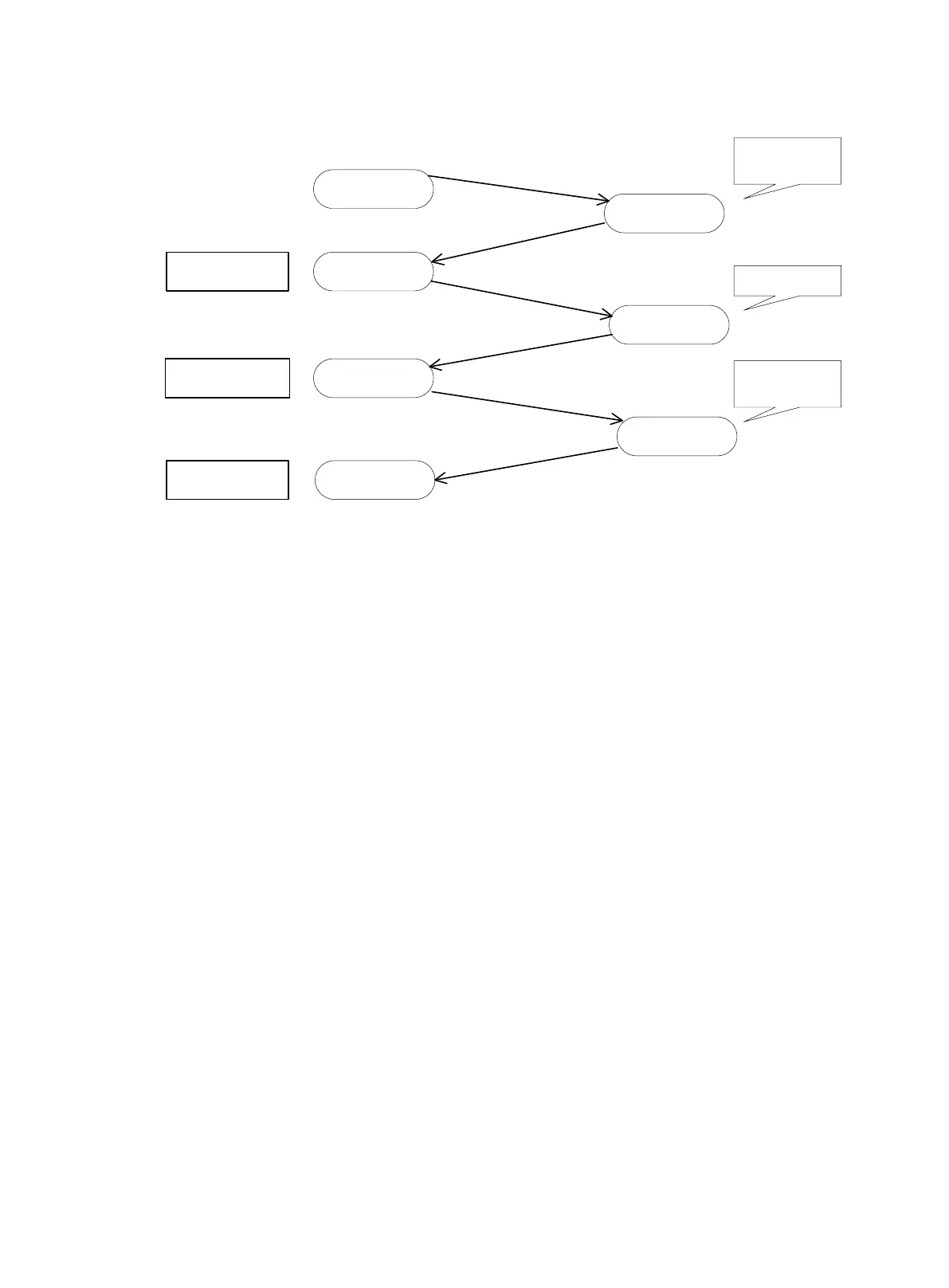
Figure 90 IKE exchange process in main mode
As shown in Figure 90, the main mode of IKE negotiation in phase 1 involves three pairs of
messages:
• SA exchange—Used for negotiating the IKE security policy.
• Key exchange—Used for exchanging the DH public value and other values, such as the
random number. The two peers use the exchanged data to generate key data and use the
encryption key and authentication key to ensure the security of IP packets.
• ID and authentication data exchange—Used for identity authentication.
The main difference between the main mode and the aggressive mode is that the aggressive mode
does not provide identity information protection and exchanges only three messages, rather than
three pairs. The main mode provides identity information protection but is slower.
IKE security mechanism
IKE has a series of self-protection mechanisms and supports secure identity authentication, key
distribution, and IPsec SA establishment on insecure networks.
Identity authentication
The IKE identity authentication mechanism is used to authenticate the identity of the communicating
peers. The device supports the following identity authentication methods:
• Pre-shared key authentication—Two communicating peers use the pre-configured shared
key for identity authentication.
• RSA signature authentication and DSA signature authentication—Two communicating
peers use the digital certificates issued by the CA for identity authentication.
The pre-shared key authentication method does not require certificates and is easy to configure. It is
usually deployed in small networks.
The signature authentication methods provide higher security and are usually deployed in networks
with the headquarters and some branches. When deployed in a network with many branches, a
signature authentication method can simplify the configuration because only one PKI domain is
required. If you use the pre-shared key authentication method, you must configure a pre-shared key
for each branch on the Headquarters node.
Algorithm
negotiation
Send local
IKE policy
Search for
matched policy
Receive the
confirmed policy
Generate the key
Perform ID/exchange
authentication
Generate the key
Peer 1 Peer 2
Key generation
SA exchange
Key exchange
ID and authentication
data exchange
Identity
authentication
Initiator’s policy
Confirmed policy
Initiator’s keying data
Receiver’s keying
data
Initiator’s identity and
authentication data
Receiver’s identity and
authentication data
Perform ID/exchange
authentication

 Loading...
Loading...



















