423
The following is an example of an ARP attack detection log message:
Detected an inspection occurred on interface GigabitEthernet1/0/1 with IP address
172.18.48.55 (Total 10 packets dropped).
To enable ARP attack detection logging:
1. Enter system view.
system-view
N/A
2.
detection logging.
arp detection log enable
By default, ARP attack detection
logging is disabled.
Displaying and maintaining ARP attack detection
Execute display commands in any view and reset commands in user view.
Display the VLANs enabled with
ARP attack detection.
display arp detection
Display the ARP attack detection
statistics.
display arp detection statistics
[
interface
interface-type
interface-number ]
Clear the ARP attack detection
statistics.
reset arp detection statistics
[
interface
interface-type
interface-number ]
User validity check and ARP packet validity check
configuration example
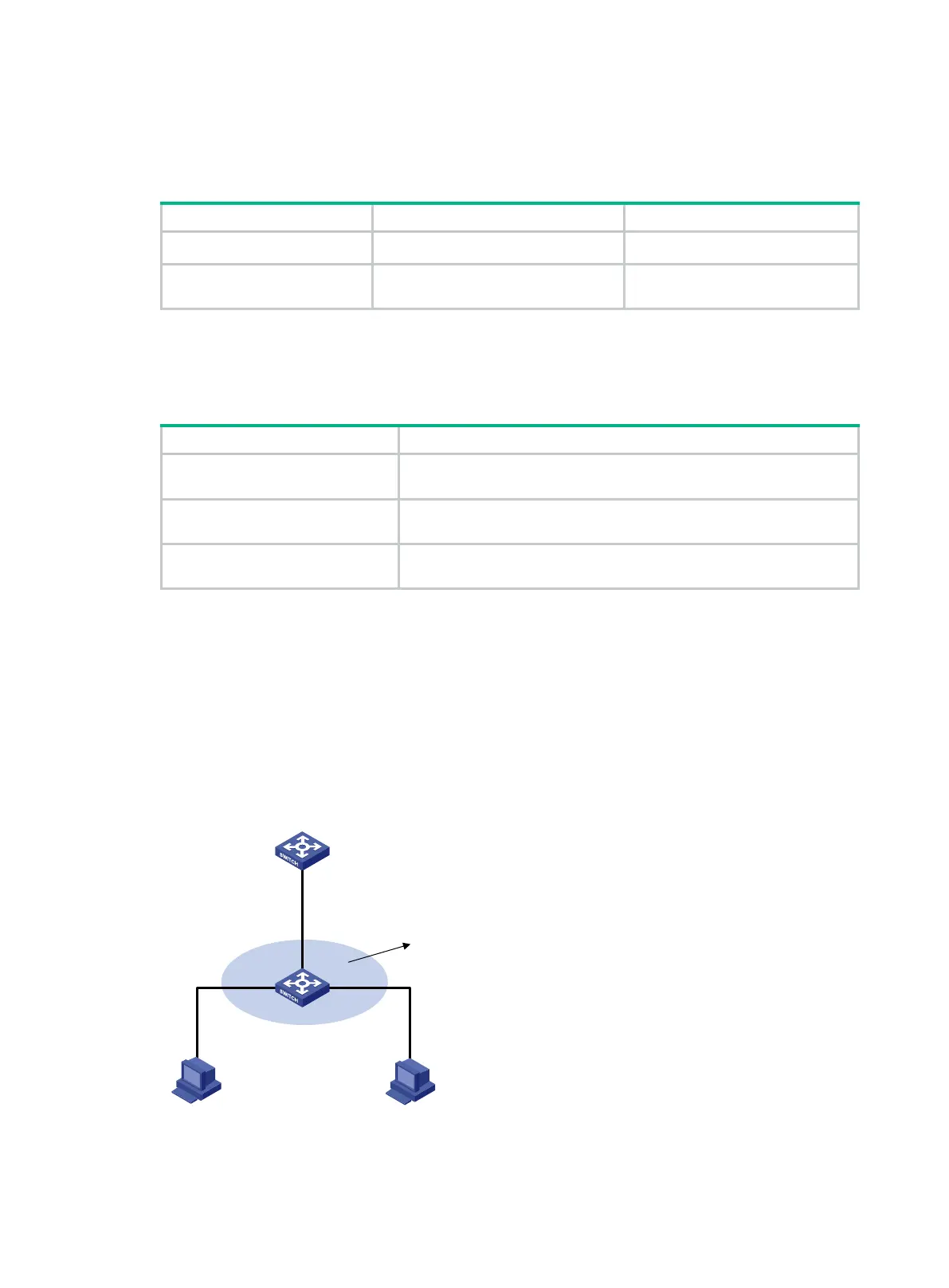
Network requirements
As shown in Figure 126, configure DHCP snooping on Switch B, and enable ARP attack detection in
VLAN 10. Switch B performs ARP packet validity check and user validity check based on static IP
source guard bindings and DHCP snooping entries for connected hosts.
Figure 126 Network diagram
Switch A
Switch B
Host A Host B
GE1/0/3
Vlan-int10
10.1.1.1/24
Gateway
DHCP server
GE1/0/1
GE1/0/3
GE1/0/2
DHCP client
VLAN 10
DHCP snooping
10.1.1.6
0001-0203-0607

 Loading...
Loading...



















