470
Display MACsec information on ports.
display macsec
[
interface
interface-type
interface-number ] [
]
Display MKA session information.
display mka session
[
interface
interface-type
interface-number |
sci-id ] [
]
Display MKA policy information.
display mka
{
default-policy
|
policy
[
name
policy-name ] }
Display MKA statistics on ports.
display mka statistics
[
interface
interface-type
interface-number ]
Reset MKA sessions on ports.
reset mka session
[
interface
interface-type
interface-number ]
Clear MKA statistics on ports.
reset mka statistics
[
interface
interface-type
interface-number ]
MACsec configuration examples
Client-oriented MACsec configuration example
Network requirements
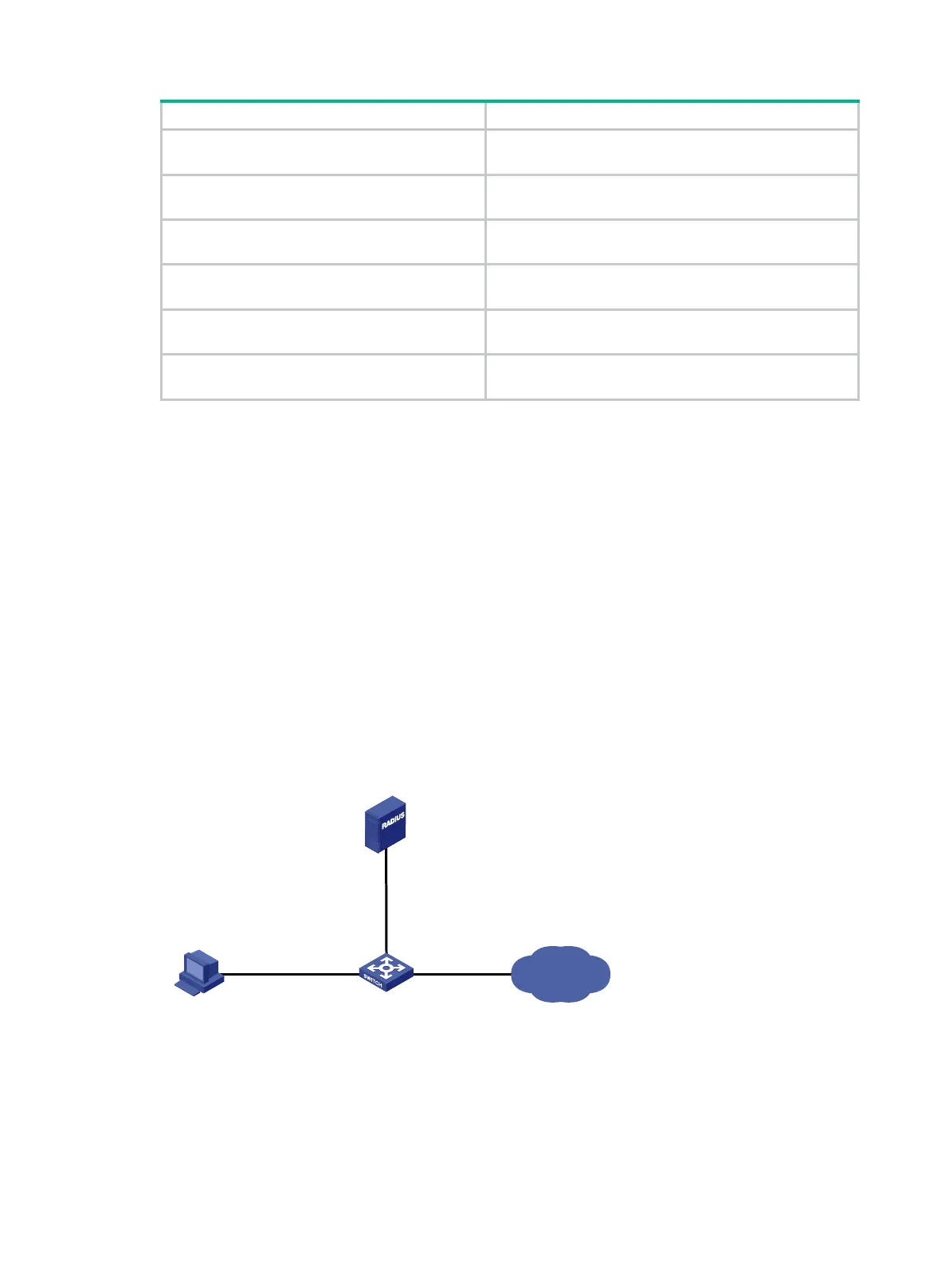
As shown in Figure 142, the host accesses the network through GigabitEthernet 1/0/1. The device
performs RADIUS-based 802.1X authentication for the host to control user access to the Internet.
To ensure secure communication between the host and device, perform the following tasks on the
device:
• Enable MACsec desire, and configure MKA to negotiate SAKs for packet encryption.
• Set the MACsec confidentiality offset to 30 bytes.
• Enable MACsec replay protection, and set the replay protection window size to 100.
• Set the MACsec validation mode to strict.
Figure 142 Network diagram
Configuration procedure
1. Configure the RADIUS server to provide authentication, authorization, and accounting services.
Add a user account for the host. (Details not shown.)
2. Configure IP addresses for the Ethernet ports. (Details not shown.)
3. Configure AAA:
Internet
Device
Host
192.168.1
.2/24
GE1
/0/
1
192.168.
1.1/
24
RADIUS server
10.1
.1.1/24
GE1
/0/
2
10.
1.1.
10/24

 Loading...
Loading...



















