© Copyright IBM Corp. 2011 Chapter 17. IPsec with IPv6 207
Setting Up a Key Policy
When configuring IPsec, you must define a key policy. This key policy can be either
manual or dynamic. Either way, configuring a policy involves the following steps:
• Create a transform set—This defines which encryption and authentication algo-
rithms are used.
•
Create a traffic selector—This describes the packets to which the policy applies.
•
Establish an IPsec policy.
•
Apply the policy.
1. To define which encryption and authentication algorithms are used, create a
transform set:
where the following parameters are used:
– transform IDA number from 1-10
– encryption methodOne of the following: esp-des | esp-3des |
esp-aes-cbc | esp-null
– integrity algorithmOne of the following: esp-sha1 | esp-md5 | none
– AH authentication algorithmOne of the following: ah-sha1 | ah-md5 | none
2. Decide whether to use tunnel or transport mode. The default mode is transport.
3. To describe the packets to which this policy applies, create a traffic selector
using the following command:
where the following parameters are used:
– traffic selector numberan integer from 1-10
– permit|denywhether or not to permit IPsec encryption of traffic that meets
the criteria specified in this command
– anyapply the selector to any type of traffic
– icmp <type>|anyonly apply the selector only to ICMP traffic of the
specified type (an integer from 1-255) or to any ICMP traffic
– tcponly apply the selector to TCP traffic
– source IP address|anythe source IP address in IPv6 format or “any” source
– destination IP address|anythe destination IP address in IPv6 format or “any”
destination
– prefix length(Optional) the length of the destination IPv6 prefix; an integer
from 1-128
Permitted traffic that matches the policy in force is encrypted, while denied traffic
that matches the policy in force is dropped. Traffic that does not match the policy
bypasses IPsec and passes through
clear
(unencrypted).
4. Choose whether to use a manual or a dynamic policy.
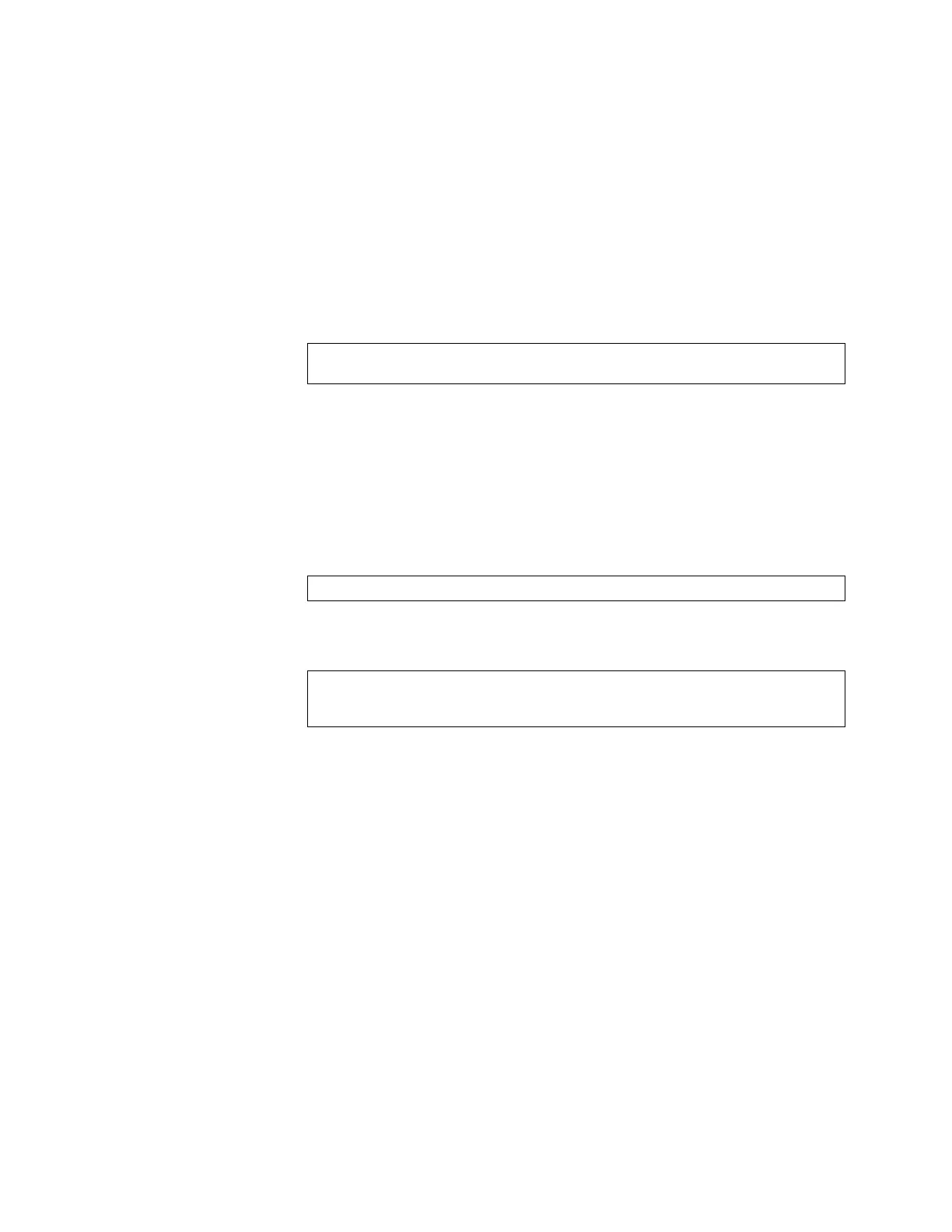
RS G8000(config)# ipsec transform-set <transform ID> <encryption method>
<integrity algorithm> <AH authentication algorithm>
RS G8000(config)# ipsec transform-set tunnel|transport
RS G8000(config)# ipsec traffic-selector <traffic selector number>
permit|deny any|icmp <type|any> |tcp > <source IP address|any> <destination IP
address|any> [<prefix length>]
 Loading...
Loading...