TG100 User Guide
67/75
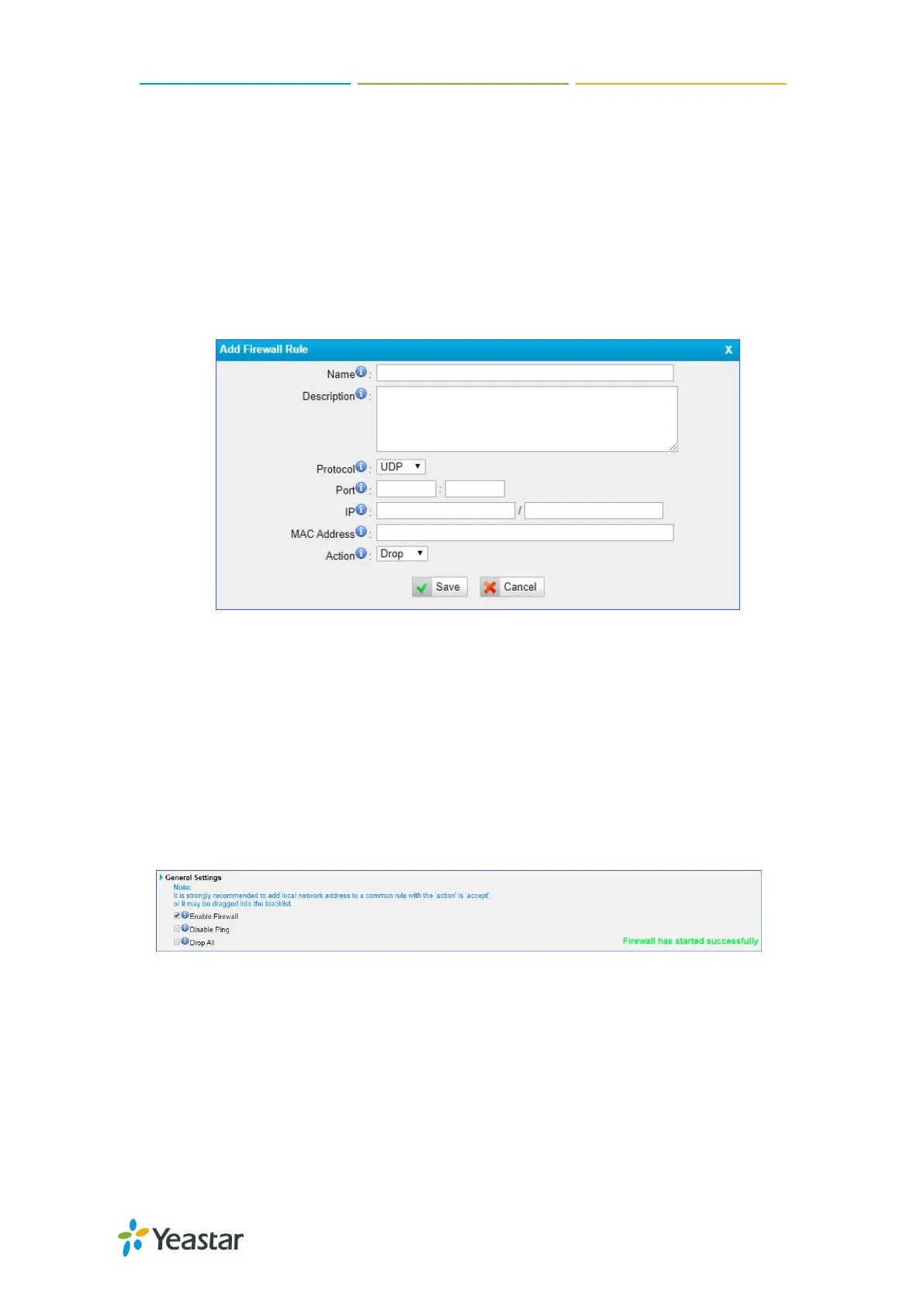
6. Enter the IP address and subnet mask in the IP field. For example, enter
192.168.5.0/255.255.255.0.
7. (Optional) Enter the MAC address of the target device.
The format of the MAC address XX:XX:XX:XX:XX:XX. X means 0-9 or A-F in hex,
the A-F are not case sensitive.
8. Choose the rule Action.
Accept: Accept the access from remote hosts.
Drop: Drop the access from remote hosts.
Ignore: Ignore the access.
9. Click Save and Apply Changes.
Enable Firewall Function
Procedure
1. Navigate to System > Security Center > Firewall Rules, select the checkbox of
Enable Firewall.
2. Click Save and Apply Changes.
The web page will prompt you that the firewall is enabled.
Block Pings through Your TG Gateway
By default, users can use the ping command from other devices to check if the TG
gateway is alive. You can block the pings to place your TG gateway in a more secure
environment.
Procedure
1. Navigate to System > Security Center > Firewall Rules, select the checkbox of

 Loading...
Loading...











