34-5
Cisco ME 3800X and 3600X Switch Software Configuration Guide
OL-23400-01
Chapter 34 Configuring MPLS, MPLS VPN, MPLS OAM, and EoMPLS
Understanding MPLS VPNs
• Scalability— MPLS-based VPNs use the peer model and Layer 3 connectionless architecture to
leverage a highly scalable solution. The peer model requires a customer site to act as a peer to one
PE router as opposed to all other customer PE or CE devices that are members of the VPN. The PE
routers maintain VPN routes for those VPNs that are members. Routers in the core network do not
maintain any VPN routes.
• Security—MPLS VPNs offer the same level of security as connection-oriented VPNs. Packets from
one VPN do not inadvertently go to another VPN. Security provided at the edge of a provider
network ensures that packets received from a customer are placed on the correct VPN; security
provided at the backbone ensures that VPN traffic is kept separate.
• Easy to create—Because MPLS VPNs are connectionless, no specific point-to-point connection
maps or topologies are required, and you can add sites to intranets and extranets to form closed user
groups.
• Flexible addressing—Customers can continue to use their present address spaces without network
address translation (NAT) because the MPLS VPN provides a public and private view of the address.
A NAT is required only if two VPNs with overlapping address spaces want to communicate.
• Straightforward migration—You can build MPLS VPNs over multiple network architectures.
Migration for the end customer is simplified because the CE router is not required to support MPLS,
so no customer's intranet modifications are needed.
• MPLS VPN also provides increased BGP functionality.
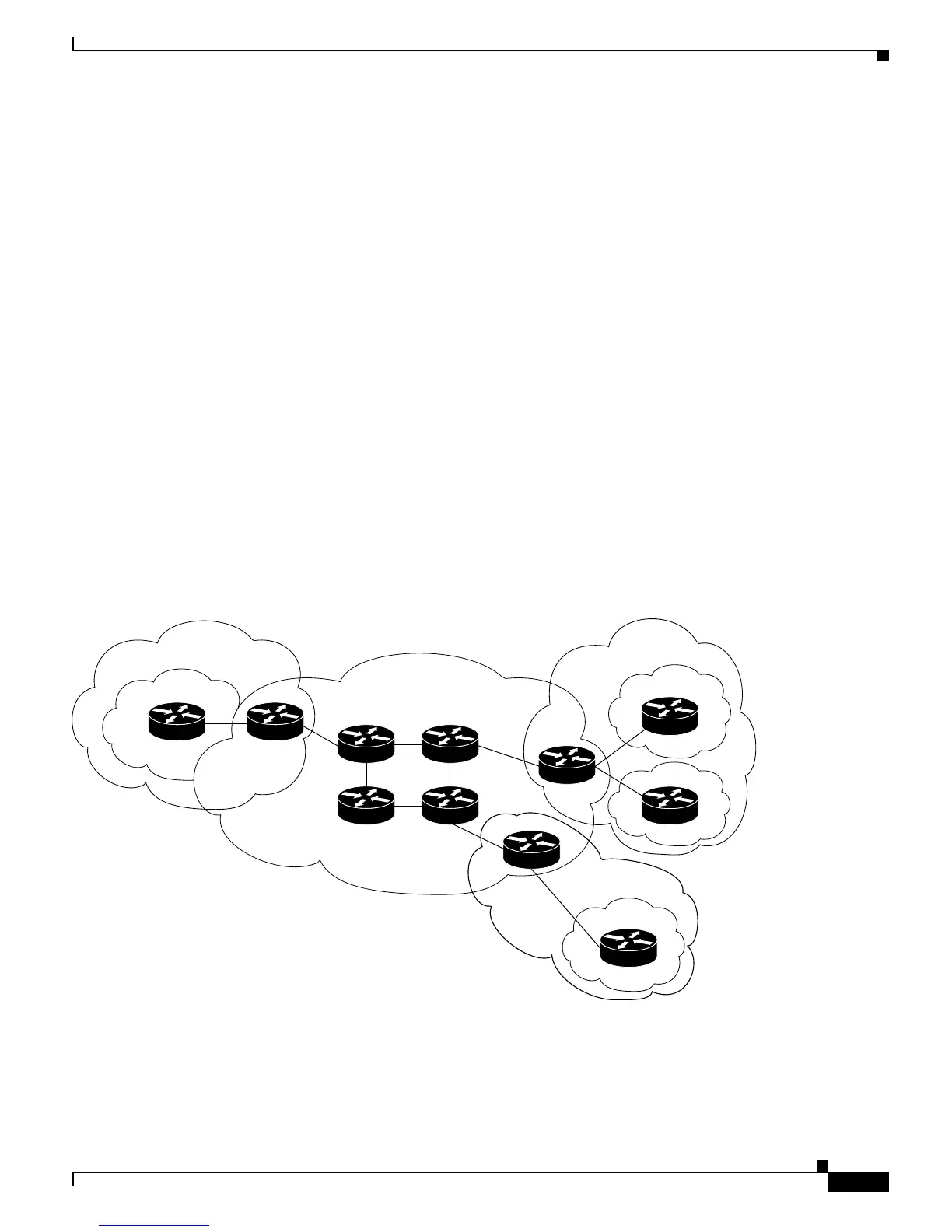
Figure 34-1 shows an example of a VPN with a service-provider backbone network, provider-edge (PE)
and customer leading-edge (CLE) routers and customer-edge (CE) devices.
Figure 34-1 VPNs with a Service-Provider Backbone
Each VPN contains customer devices attached to the customer-edge (CE) devices. The customer devices
use VPNs to exchange information between devices, and the provider routers (P) are not aware of the
VPNs.

 Loading...
Loading...











