1-11
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring Cisco Mobility Advantage
Configuration Examples for Cisco Mobility Advantage
Configuration Examples for Cisco Mobility Advantage
• Example 1: Cisco UMC/Cisco UMA Architecture – Security Appliance as Firewall with TLS Proxy
and MMP Inspection, page 1-11
• Example 2: Cisco UMC/Cisco UMA Architecture – Security Appliance as TLS Proxy Only,
page 1-12
This section describes sample configurations that apply to two deployment scenarios for the TLS proxy
used by the Cisco Mobility Advantage solution—scenario 1 where the ASA functions as both the
firewall and TLS proxy and scenario 2 where the ASA functions as the TLS proxy only. In both
scenarios, the clients connect from the Internet.
In the samples, you export the Cisco UMA server certificate and key-pair in PKCS-12 format and import
it to the ASA. The certificate will be used during handshake with the Cisco UMA clients.
Installing the Cisco UMA server self-signed certificate in the ASA truststore is necessary for the ASA
to authenticate the Cisco UMA server during handshake between the ASA proxy and Cisco UMA server.
You create a TLS proxy instance for the Cisco UMA clients connecting to the Cisco UMA server. Lastly,
you must enable TLS proxy for MMP inspection.
Example 1: Cisco UMC/Cisco UMA Architecture – Security Appliance as
Firewall with TLS Proxy and MMP Inspection
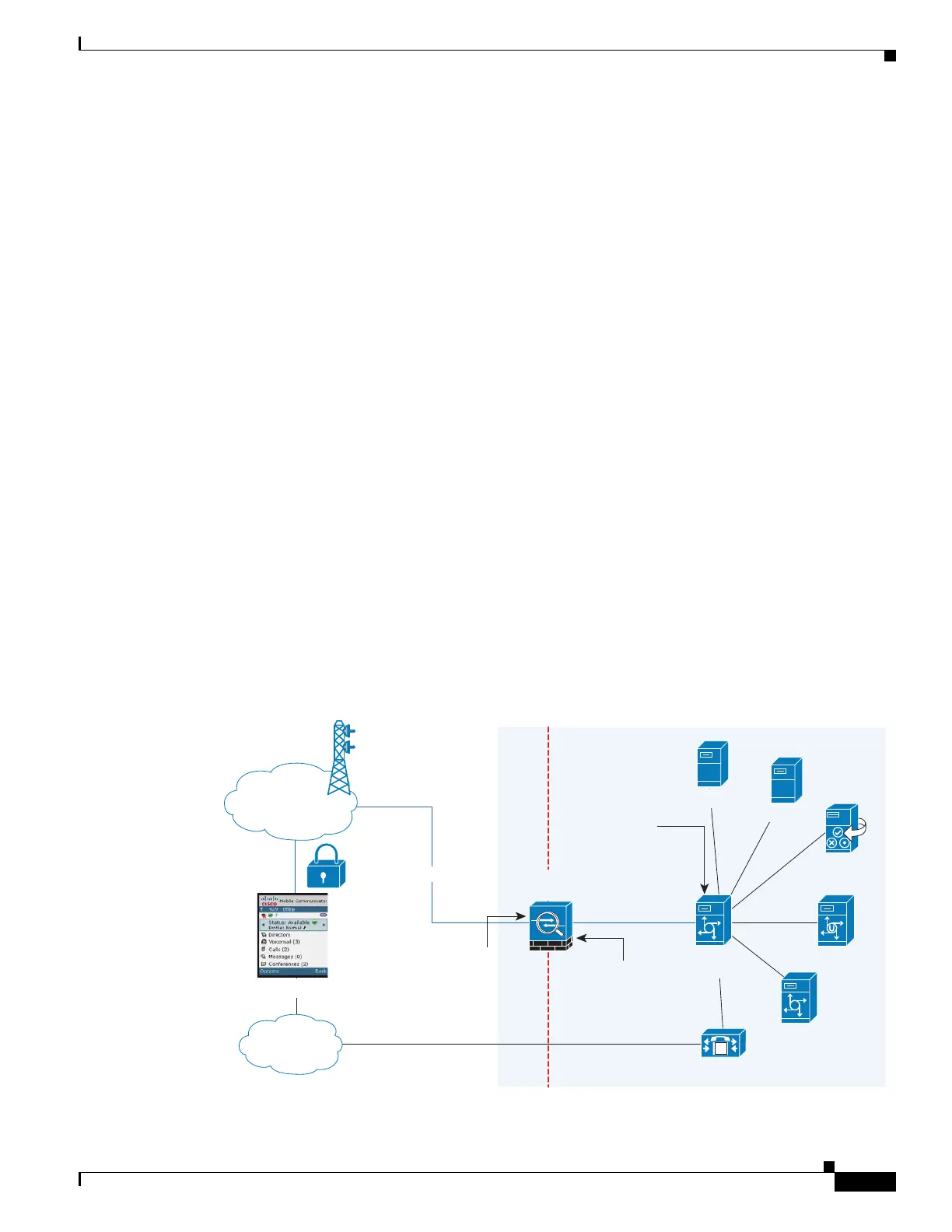
As shown in Figure 1-5 (scenario 1—the recommended architecture), the ASA functions as both the
firewall and TLS proxy. In the scenario 1 deployment, the ASA is between a Cisco UMA client and a
Cisco UMA server. In this scenario, the ASA performs static NAT by translating the Cisco UMA server
10.1.1.2 IP address to 192.0.2.140.
Figure 1-5 Cisco UMC/Cisco UMA Architecture – Scenario 1: Security Appliance as Firewall with TLS Proxy
and MMP Inspection
271641
ASA with
TLS Proxy
Cisco UMA
Server
Mobile Data
Network (GPRS
Data Channel)
PSTN
MP
Conference
Voice mail
Cisco Unified
Presence
M
Cisco UCM
Exchange
Active Directory
Enterprise Services
Firewall
MMP/SSL/TLS
Voice Channel
MMP/SSL/TLS
Cisco UMC Client
Network:
10.1.1.0/24
IP Address:
10.1.1.2
Port: 5443
Network:
10.1.1.0/24
IP Address:
10.1.1.1
Hostname:
cuma.example.com
Network: 192.0.2.0/24
IP Address: 192.0.2.140
Port: 5443

 Loading...
Loading...











