1-4
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring the Transparent or Routed Firewall
Information About the Firewall Mode
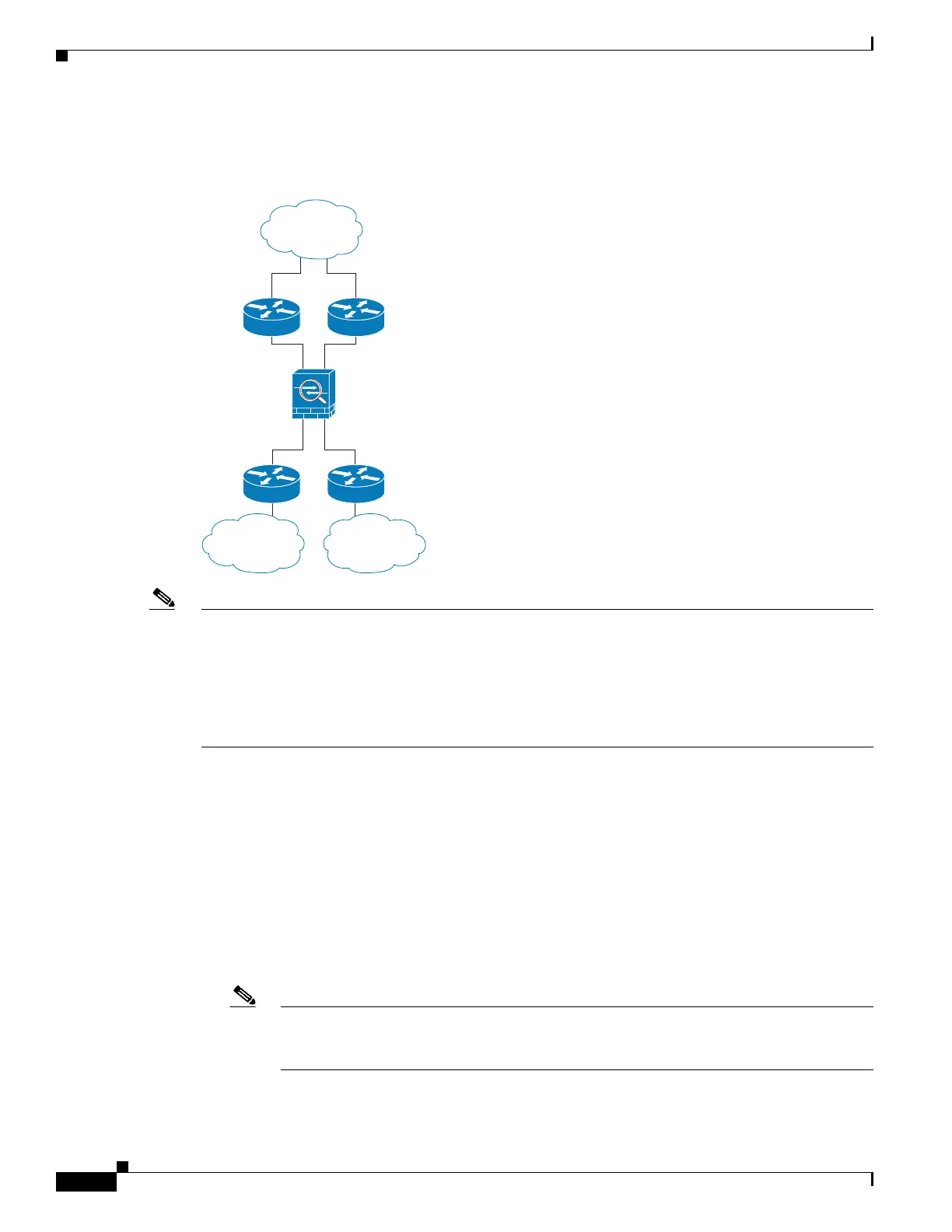
Figure 1-2 shows two networks connected to the ASA, which has two bridge groups.
Figure 1-2 Transparent Firewall Network with Two Bridge Groups
Note Each bridge group requires a management IP address. The ASA uses this IP address as the source address
for packets originating from the bridge group. The management IP address must be on the same subnet
as the connected network. For another method of management, see the “Management Interface (ASA
5510 and Higher)” section on page 1-4.
The ASA does not support traffic on secondary networks; only traffic on the same network as the
management IP address is supported.
Management Interface (ASA 5510 and Higher)
In addition to each bridge group management IP address, you can add a separate Management slot/port
interface that is not part of any bridge group, and that allows only management traffic to the ASA. For
more information, see the “Management Interface” section on page 11-2.
Allowing Layer 3 Traffic
• Unicast IPv4 and IPv6 traffic is allowed through the transparent firewall automatically from a higher
security interface to a lower security interface, without an ACL.
Note Broadcast and multicast traffic can be passed using access rules. See the “Allowing
Broadcast and Multicast Traffic through the Transparent Firewall Using Access Rules”
section on page 7-6 for more information.
10.2.1.110.1.1.1
BVI 2
10.2.1.2
BVI 1
10.1.1.2
10.2.1.310.1.1.3
254279

 Loading...
Loading...











