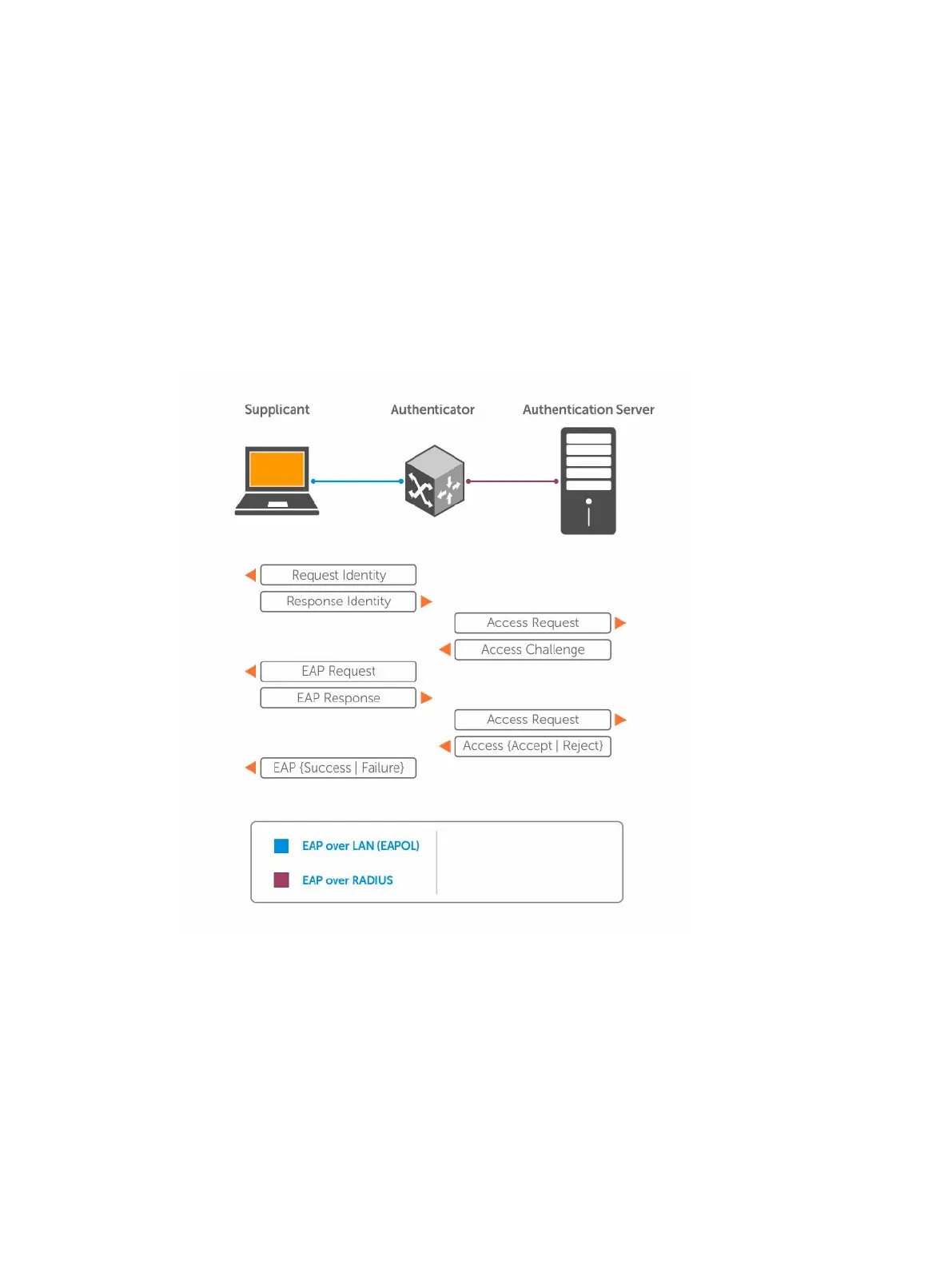
2. The supplicant responds with its identity in an EAP Response Identity frame.
3. The authenticator decapsulates the EAP response from the EAPOL frame, encapsulates it in a
RADIUS Access-Request frame and forwards the frame to the authentication server.
4. The authentication server replies with an Access-Challenge frame. The Access-Challenge frame
requests that the supplicant prove that it is who it claims to be, using a specified method (an EAP-
Method). The challenge is translated and forwarded to the supplicant by the authenticator.
5. The supplicant can negotiate the authentication method, but if it is acceptable, the supplicant
provides the Requested Challenge information in an EAP response, which is translated and
forwarded to the authentication server as another Access-Request frame.
6. If the identity information provided by the supplicant is valid, the authentication server sends an
Access-Accept frame in which network privileges are specified. The authenticator changes the port
state to authorized and forwards an EAP Success frame. If the identity information is invalid, the
server sends an Access-Reject frame. If the port state remains unauthorized, the authenticator
forwards an EAP Failure frame.
Figure 8. EAP Port-Authentication
802.1X
111

 Loading...
Loading...











