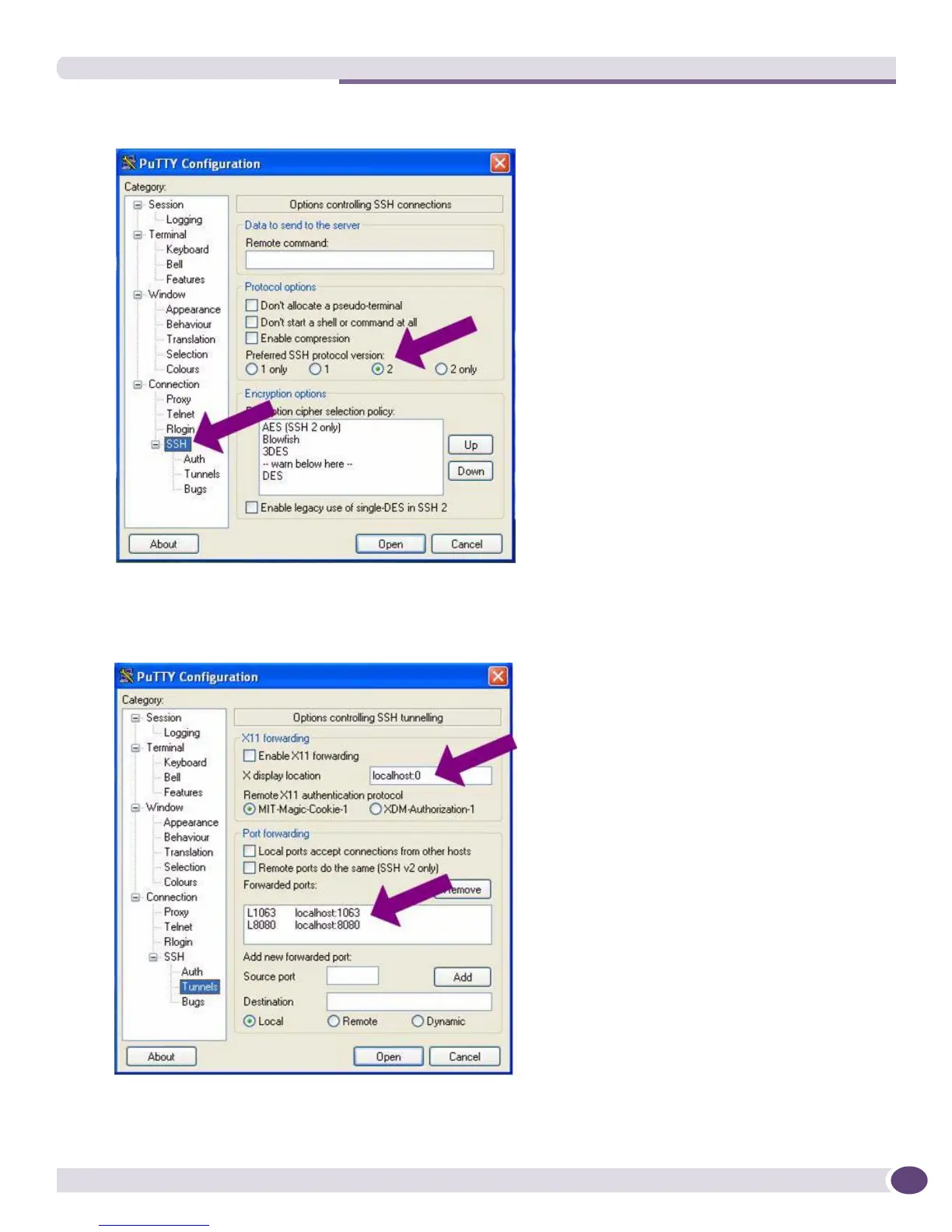
Step 2: Configure the PuTTY Client
EPICenter Concepts and Solutions Guide
207
Figure 80: The basic SSH settings
3 Under SSH, click on Tunnels, as shown in Figure 81.
Figure 81: SSH Tunneling settings
● For X display location type localhost:0.

 Loading...
Loading...