Access Control Lists (ACLs) for the Series 5300xl Switches
Overview
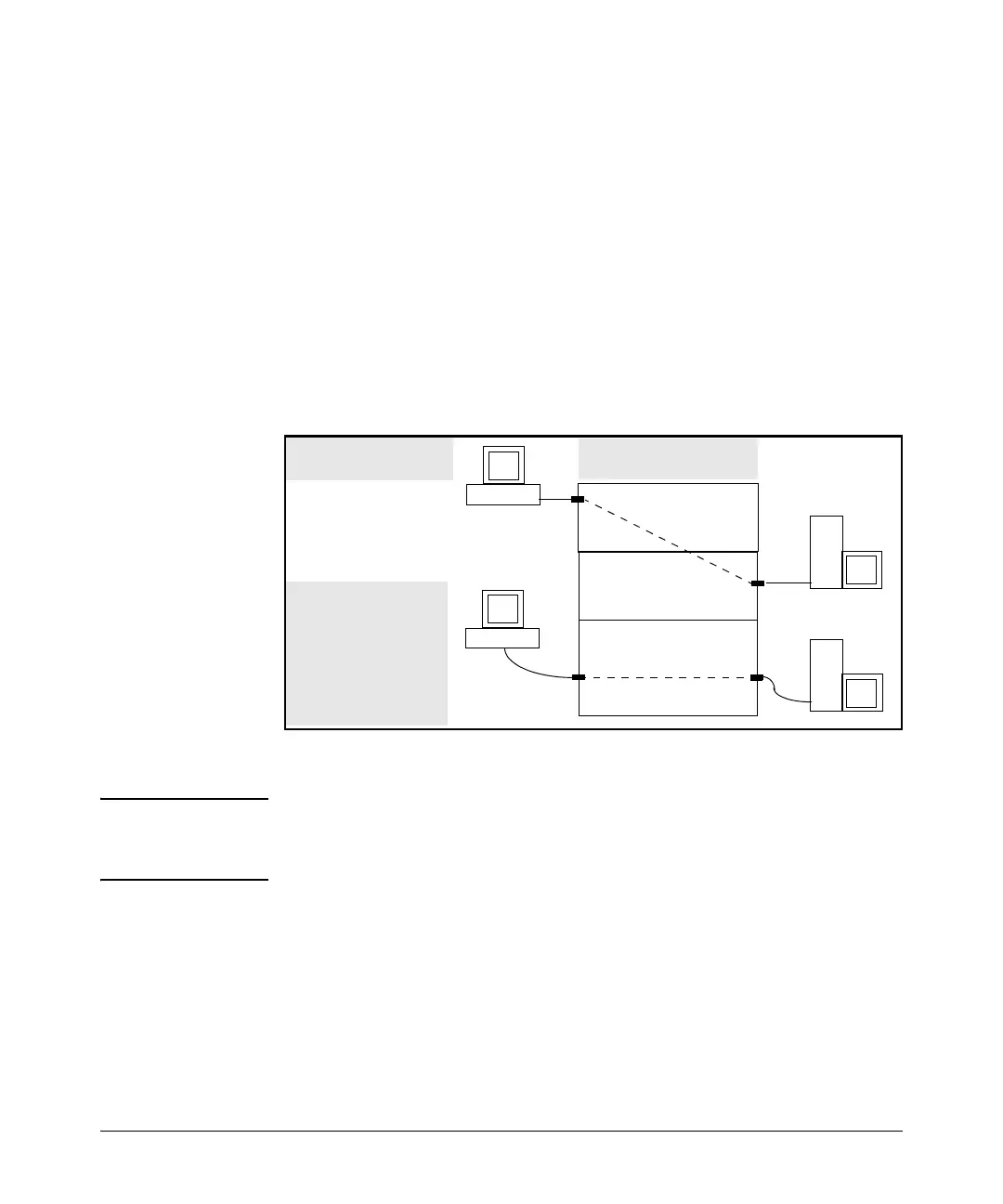
■ You would assign either an inbound ACL on VLAN “A” or an outbound
ACL on VLAN “B” to filter a packet routed between subnets; that is,
from the workstation 18.28.10.5 on VLAN “A” to the server at
18.28.20.99 on VLAN “B”. (An outbound ACL on VLAN “A” or an
inbound ACL on VLAN “B” would not filter the packet.)
■ Where multiple subnets are configured on the same VLAN, if:
• Traffic you want to filter moves between subnets on the same VLAN.
• The traffic source and destination IP addresses are on devices exter-
nal to the switch.
Then you can use either inbound or outbound ACLs to filter the traffic on
the VLAN (because the traffic moves between subnets but enters and
leaves the switch in the same VLAN.)
VLAN A
18.28.10.1
(One Subnet)
VLAN C
18.28.40.1 18.28.30.1
(Multiple Subnets)
VLAN B
18.28.20.1
(One Subnet)
5300XL Switch with IP
Routing Enabled
18.28.10.5
18.28.20.99
18.28.30.33
18.28.40.17
Because of multinetting,
traffic routed from
18.28.40.17 to 18.28.30.33
remains in VLAN C. This
allows you to apply either
an inbound or an
outbound ACL to filter the
same traffic.
The subnet mask for this
example is 255.255.255.0.
Figure 9-1. Example of Filter Applications
Note ACLs do not filter traffic that remains in the same subnet from source to
destination (switched traffic) unless the destination IP address (DA) is on the
switch itself.
Features Common to All ACLs
■ On any VLAN you can apply one ACL to inbound traffic and one ACL
to outbound traffic. You can use the same ACL or different ACLs for
the inbound and outbound traffic.
■ Any ACL can have multiple entries (ACEs).
9-9
 Loading...
Loading...











