Access Control Lists (ACLs) for the Series 3400cl and Series 6400cl Switches
Enable ACL “Deny” Logging
ACL Logging Operation
When the switch detects a packet match with an ACE and the ACE includes
both the deny action and the optional log parameter, an ACL log message is
sent to the designated debug destination. The first time a packet matches an
ACE with deny and log configured, the message is sent immediately to the
destination and the switch starts a wait-period of approximately five minutes.
(The exact duration of the period depends on how the packets are internally
routed.) At the end of the collection period, the switch sends a single-line
summary of any additional “deny” matches for that ACE (and any other “deny”
ACEs for which the switch detected a match). If no further log messages are
generated in the wait-period, the switch suspends the timer and resets itself
to send a message as soon as a new “deny” match occurs. The data in the
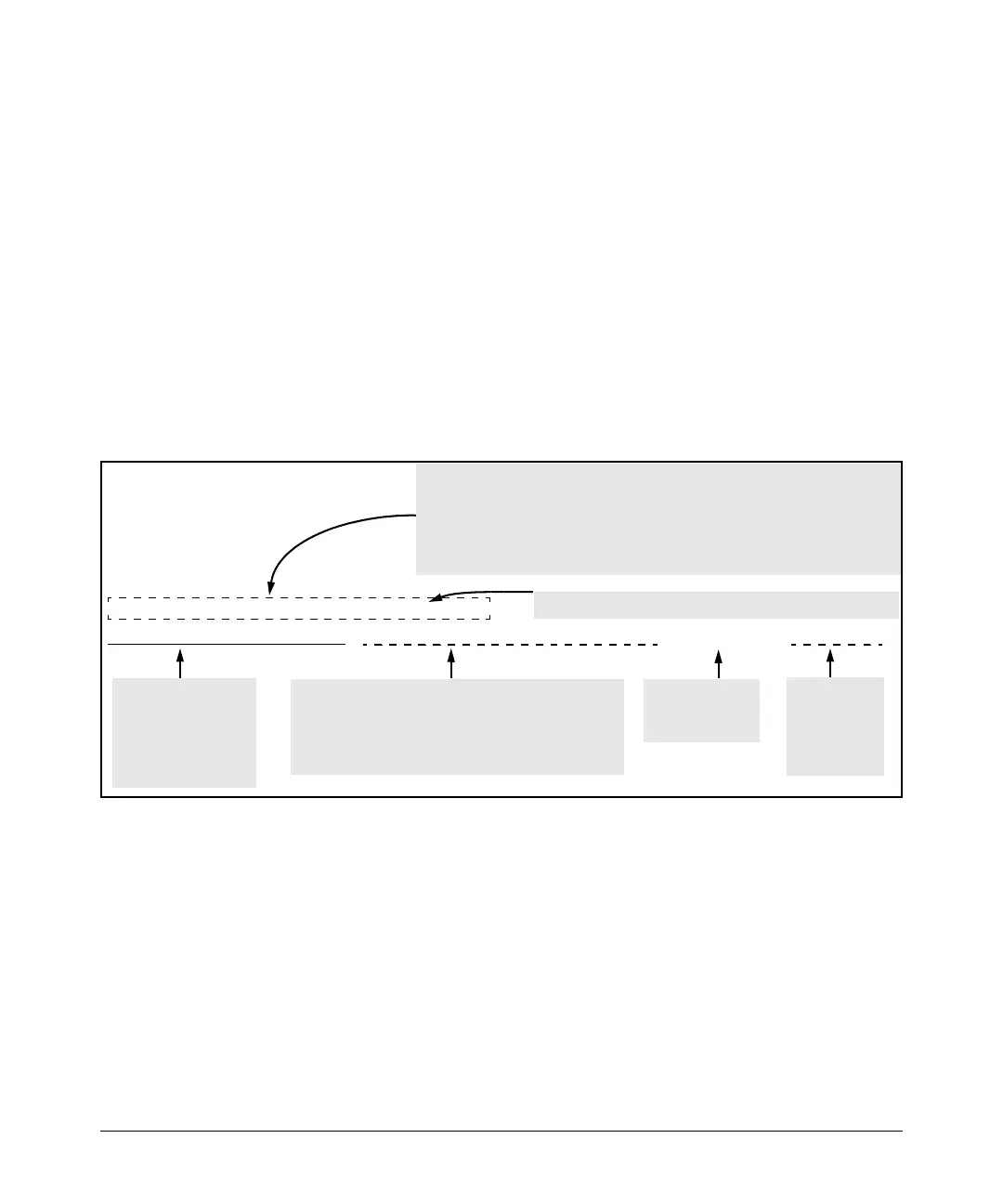
message includes the information illustrated in figure
10-32.
Oct 15 10:04:45 10.28.234.181 ACL:
ACL 10/15/04 10:04:45: denied ip src 10.28.234.183 (PORT 10), 1 packets
Indicates the port
on which the ACL
is assigned.
Begins the actual
message generated
by the ACL itself, and
indicates message
type (ACL), date and
time of generation.
Note: To fit this illustration on the page, the portion of the message generated by
the Syslog server itself is shown in the line above the portion of the message
generated by the switch. Depending on the terminal emulator you use, you may
see information similar to this, which includes the date and time the log message
was received, the IP address of the default VLAN on the sending switch, and the
message type (ACL).
ACL action (denied), protocol type (IP, TCP, or UDP),
source IP address of the denied packet(s) and, if
applicable, the TCP or UDP port number at the source
device. The port number is “0” if the protocol is “IP” or
you did not specify a port number.
Indicates the
number of
packets (deny
instances)
detected.
Indicates the destination IP address of the denied packet.
Figure 10-32. Example of the Content of an ACL-Generated Message
Enabling ACL Logging on the Switch
1. Use the debug command to:
a. Configure one or more log destinations.
b. If you are using a Syslog server, use the logging command to configure
the server’s IP address. (You can configure up to six Syslog servers.)
c. Ensure that the switch can access any Syslog servers you specify.
2. Configure one or more ACLs with the deny action and the log option.
10-72

 Loading...
Loading...











