Access Control Lists (ACLs) for the Series 3400cl and Series 6400cl Switches
Planning an ACL Application on a Series 3400cl or Series 6400cl Switch
Troubleshooting a Shortage of Per-Port Resources
As noted above, a lack of available per-port rules can be caused by a combi-
nation of ACL, IGMP, QoS, and Rate-Limiting applications. A lack of available
ACL masks is caused by configuring an ACL to oversubscribe the number of
per-port masks available for ACLs. (Also, note that enabling IGMP on a VLAN
consumes one ACL mask per-port for all ports on the switch, leaving seven
available per-port masks for ACL applications.)
Do the following to determine how to change resource usage to allow the ACL
you want to configure:
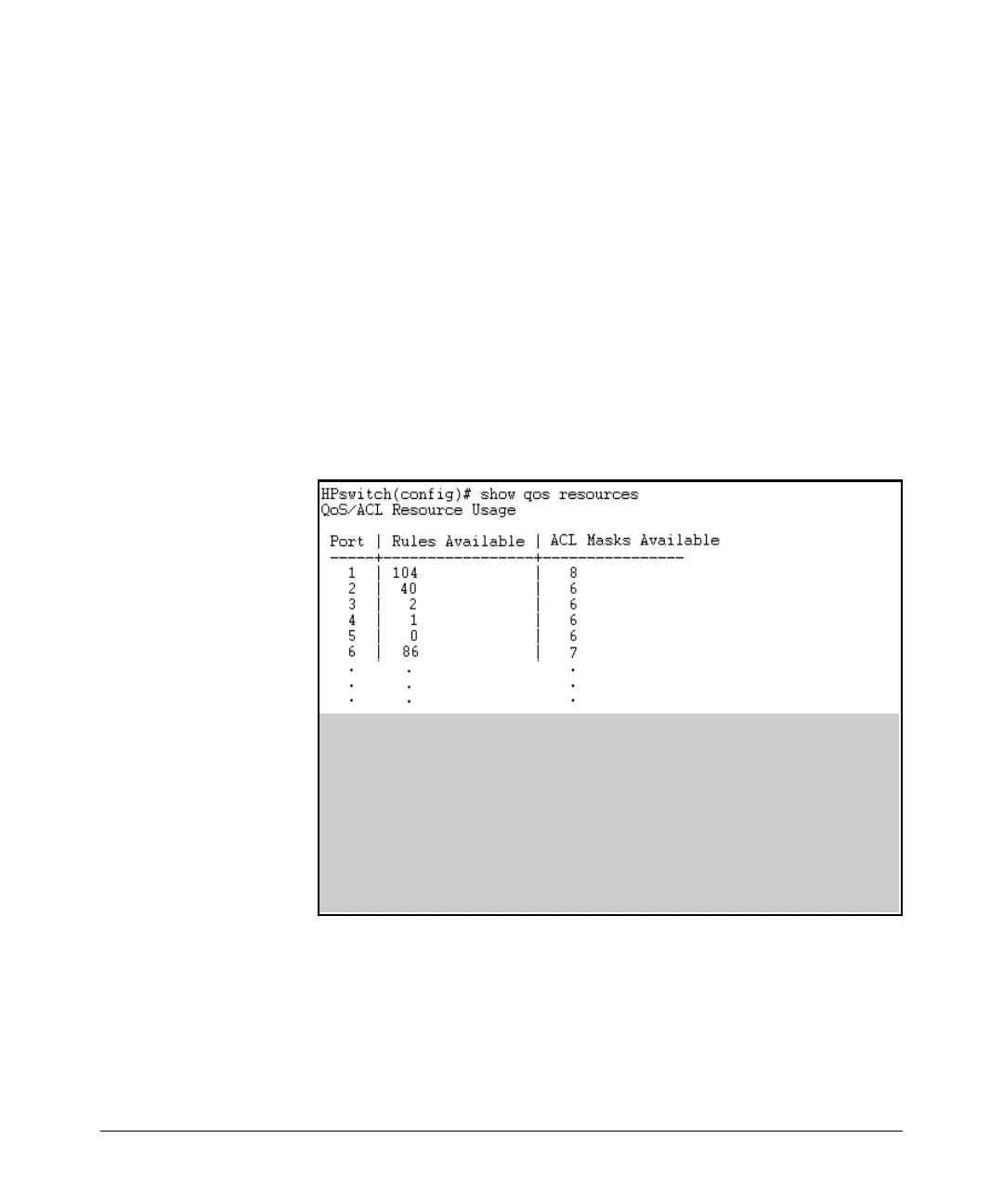
1. Use the show access-list resources command to identify the port(s) on
which there are insufficient rule resources. For example, figure
10-6
includes ports that can be the source of problems due to rule consumption
by policies configured earlier:
In this example, suppose that earlier configuration of QoS policies have depleted the rule
resources on ports 4 and 5 to the point where there are not enough rules remaining for applying
an ACL, and only enough rules on port 3 for a minimal ACL.
At a minimum, the policies previously configured on ports 4 and 5 must be reduced to free up
enough rule resources to allow you to apply an ACL to these ports. Depending on the ACL you
want to apply to port 3, existing QoS policies on port 3 may have to be reduced.
Port 3 has enough rules available to accept an ACL that uses 1 or 2 rules.
Port 4 can accept only an ACL with one entry that has either the same (standard) ACL mask as
deny any or the same (extended) ACL that has the same SA/DA ACL mask and same IP protocol.
Figure 10-6. Example of Inspecting Available Rule (and Mask) Resources
2. Use show commands to identify the currently configured ACL, QoS, and
Rate-Limiting policies, and any per-VLAN IGMP configuration.
3. Determine which of the existing policies you can remove to free up rule
resources for the ACL policy you want to implement. Depending on your
network topology and configuration, you can free up rule resources by
moving some policies to other devices. Another alternative is to inspect
10-21

 Loading...
Loading...











