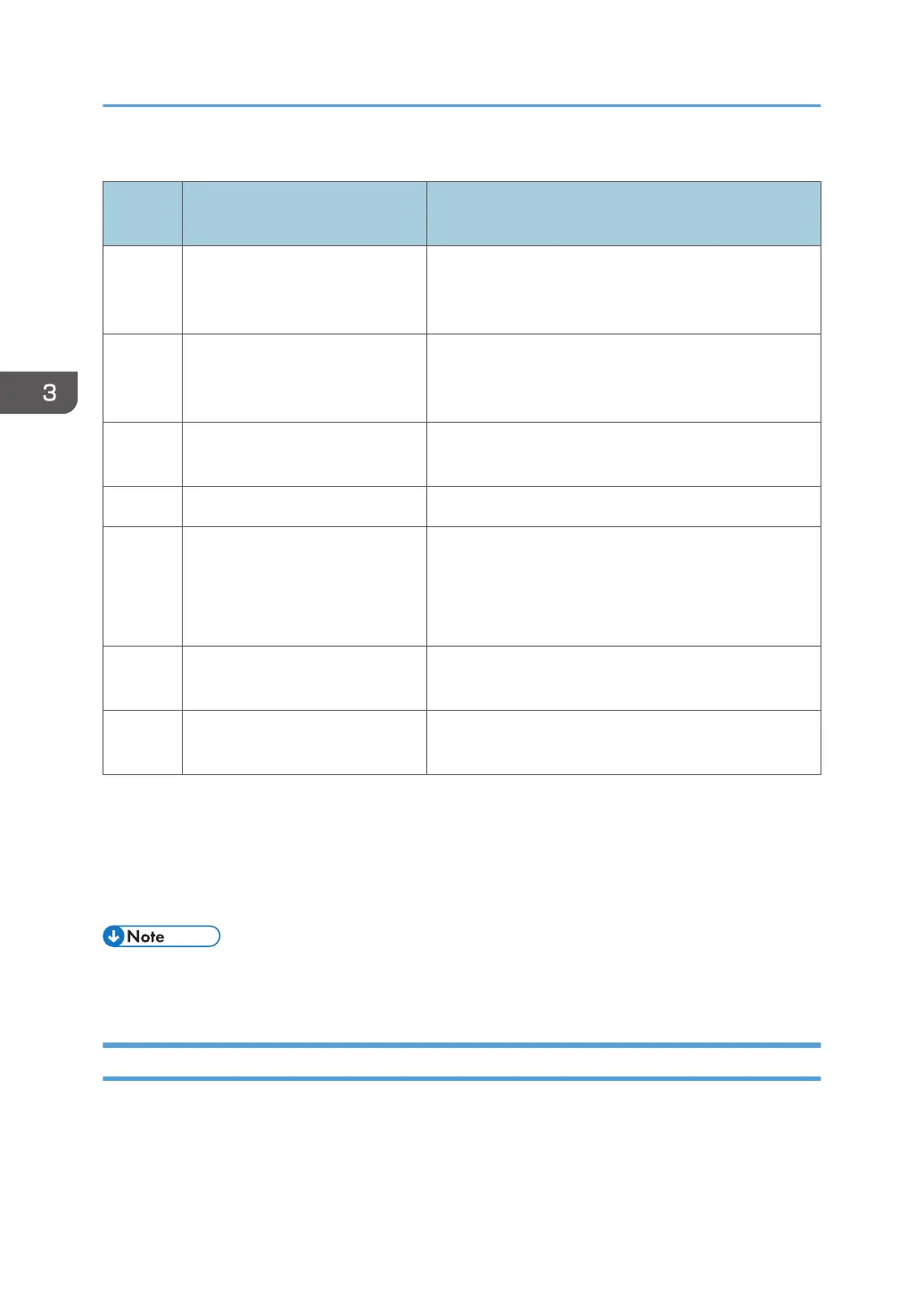
Row names and their corresponding values
Row
number
Row name Value of line five and subsequent lines
A Range Type
Specify the search criteria from "One Host Name",
"One IP Address", "Specify IP Range", and "IPv6
Address".
B IP Start/IP Address/Host Name
Enter the discovery target host name, IP address, IPv6
address or start IP address of the discovery target IP
address range.
C IP End
Enter an end IP address of the discovery target IP
address range.
D Subnet Mask Enter a subnet mask.
E 0=Include/1=Exclude
Specify whether to include or exclude network search
as a search range.
The data is included in the network search if you enter
"0" and excluded if you enter "1".
F Range Name
Enter a discovery range name. Use up to 61
alphanumeric characters.
G Description
Enter a discovery range description. Use 0 to 61
alphanumeric characters.
Rows F and G appear only when writing data using the broadcast setting in [Auto Discovery] in
[@Remote Settings]. Nonetheless, you can also have CSV files including Rows F and G read into the
broadcast setting in [Add Device] or [Network Search] in [Manual Discovery]. Also, you can have CSV
files written from the broadcast setting in [Add Device] or [Network Search] in [Manual Discovery] read
using broadcast setting in [Auto Discovery].
• Do not change the information in lines one through three, as this information is used for
identification.
Format of a Security Log CSV File
Security log CSV file is written out in the format indicated below:
The variables are indicated in bold letters.
3. How to Configure and Check the Device
38
 Loading...
Loading...