Protection
9.2 Configuring access protection for the CPU
Distributed I/O system
158 System Manual, 09/2019, A5E03576849-AJ
Behavior of functions with different access levels
The STEP 7 online help includes a table which lists the online functions that are available in
the different access levels.
Selecting the access levels
To configure the access levels of a CPU, follow these steps:
1. Open the properties of the CPU in the Inspector window.
2. Open the "Protection" entry in the area navigation.
A table with the possible access levels is available in the Inspector window.
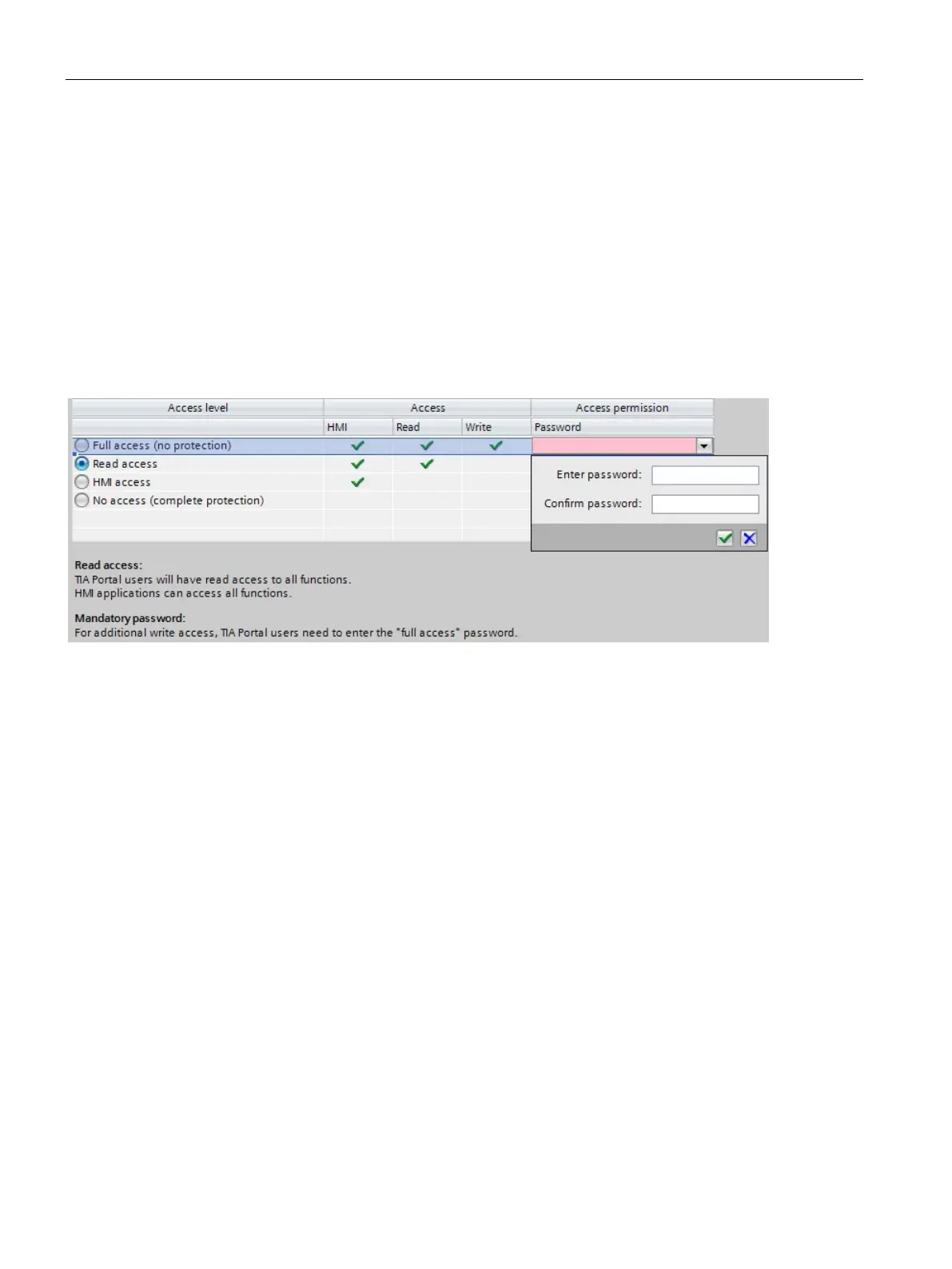
Figure 9-1 Possible access levels
3. Activate the desired protection level in the first column of the table. The green check
marks in the columns to the right of the access level show you which operations are still
available without entering the password. In the example (see above), read access and
HMI access are still possible without a password.
4. In the "Enter password" column, specify a password for the access level "Full access" in
the first row. In the "Confirm password" column, enter the selected password again to
guard against incorrect entries.
5. Assign additional passwords as required for other access levels.
6. Download the hardware configuration for the access level to take effect.
The CPU logs the following actions with an entry in the diagnostic buffer:
● Input of the correct or incorrect password, as the case may be
● Changes in the configuration of access levels

 Loading...
Loading...





















