Access Control Lists (ACLs) for the Series 5300xl Switches
Configuring and Assigning an ACL
[log]
Optional; generates an ACL log message if:
• The action is deny. (This option is not configurable for
Permit.)
• There is a match.
• ACL logging is enabled on the switch. (Refer to
“Enabling ACL Logging on the Switch” on page
9-60)
Syntax: vlan < vid > ip access-group < list-# | ascii-str > < in | out >
Assigns an ACL, designated by an ACL list number or ASCII
string (alphanumeric list name), to a VLAN to filter either
inbound or outbound IP traffic on that VLAN. To configure
named ACLs, refer to
“Configuring a Named ACL” on page
9-44.
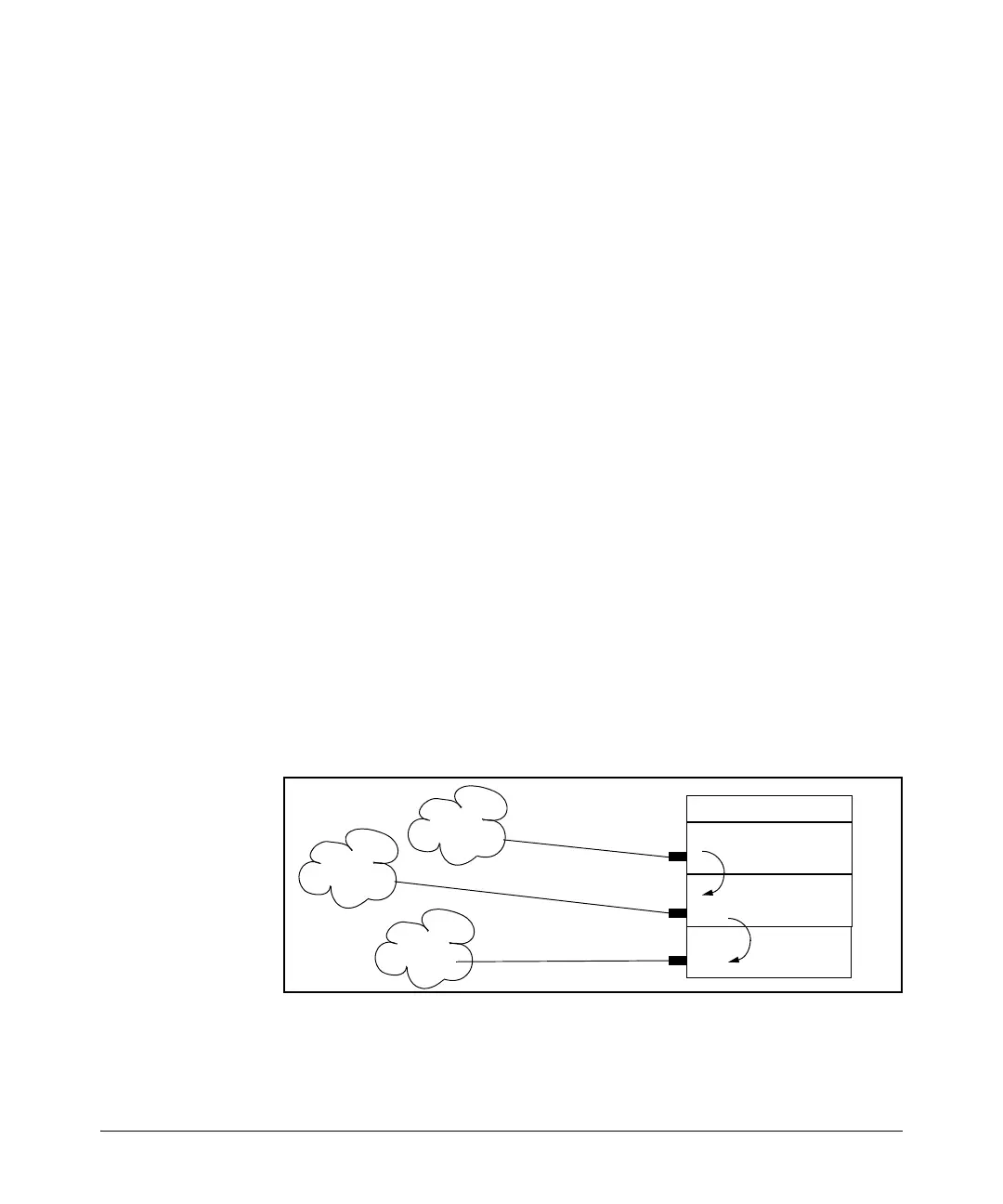
Example of an Extended ACL. Suppose that you want to implement these
policies on a Series 5300XL switch configured for IP routing and membership
in VLANs 10, 20, and 30:
A. Permit Telnet traffic from 10.10.10.44 to 10.10.20.78, deny all other IP
traffic from network 10.10.10.0 (VLAN 10) to 10.10.20.0 (VLAN 20), and
permit all other IP traffic from any source to any destination. (See “A” in
figure
9-13, below.)
B. Permit FTP traffic from IP address 10.10.20.100 (on VLAN 20) to
10.10.30.55 (on VLAN 30). Deny FTP traffic from other hosts on
network10.10.20.0 to any destination, but permit all other traffic.
VLAN 10
10.10.10.1
VLAN 20
10.10.20.1
VLAN 30
10.10.30.1
1
3
2
Series 5300XL Switch
10.10.10.0
10.10.20.0
10.10.30.0
A
B
Figure 9-13. Example of an Extended ACL
9-42
 Loading...
Loading...











