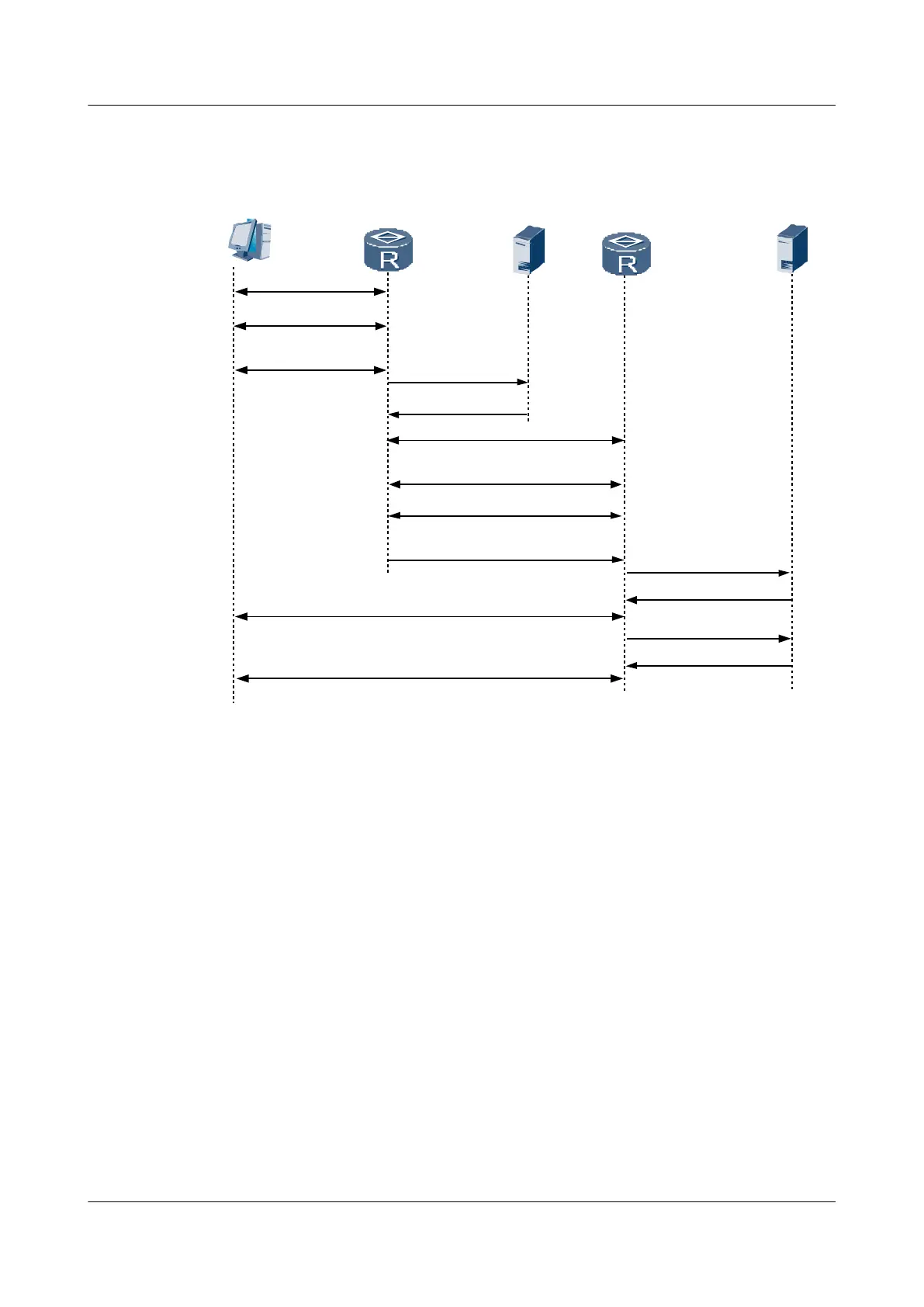
Figure 4-3 Networking diagram of call setup in an L2TP tunnel
LAC
RouterA
LNS
RouterB
(1) call setup
(2) PPP LCP setup
(3) PAP or CHAP
authentication
(4) access request
(5) access accept
(6) tunnel establish
(7) PAP or CHAP authentication
(challenge/response)
(8) authentication passes
(9) user CHAP response,
PPP negotiation parameter
(10) access request
(11) access accept
(12) CHAP authentication twice(challenge/response)
(13) access request
(14) access accept
(15) authentication passes
PC
LAC
RADIUS
Server
LNS
RADIUS
Server
The following steps describe the call setup process in an L2TP tunnel:
1. A PC initiates a call-connecting request.
2. The PC and RouterA (LAC) negotiate PPP LCP parameters.
3. RouterA performs Password Authentication Protocol (PAP) or Challenge Handshake
Authentication Protocol (CHAP) authentication on the user information provided by the
PC.
4. RouterA sends an access request, which contains the user's name and password, to the LAC
RADIUS server for identity authentication.
5. The LAC RADIUS server authenticates this user and replies with an access-accepting
message, such as the LNS address corresponding to the user. After authentication is
successful, RouterA prepares to initiate a tunnel request.
6. RouterA initiates a tunnel request to the RouterB (LNS) specified by the LAC RADIUS
server.
7. RouterA informs RouterB of a CHAP challenge, and RouterB replies with a CHAP
response and its CHAP challenge. The RouterA then replies with a CHAP response.
8. Authentication is performed successfully.
Huawei AR1200 Series Enterprise Routers
Configuration Guide - VPN 4 L2TP Configuration
Issue 01 (2012-04-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
249

 Loading...
Loading...



















