User Interface
R&S
®
GP-E/GP-S
59User Manual v16.2.1 ─ 01
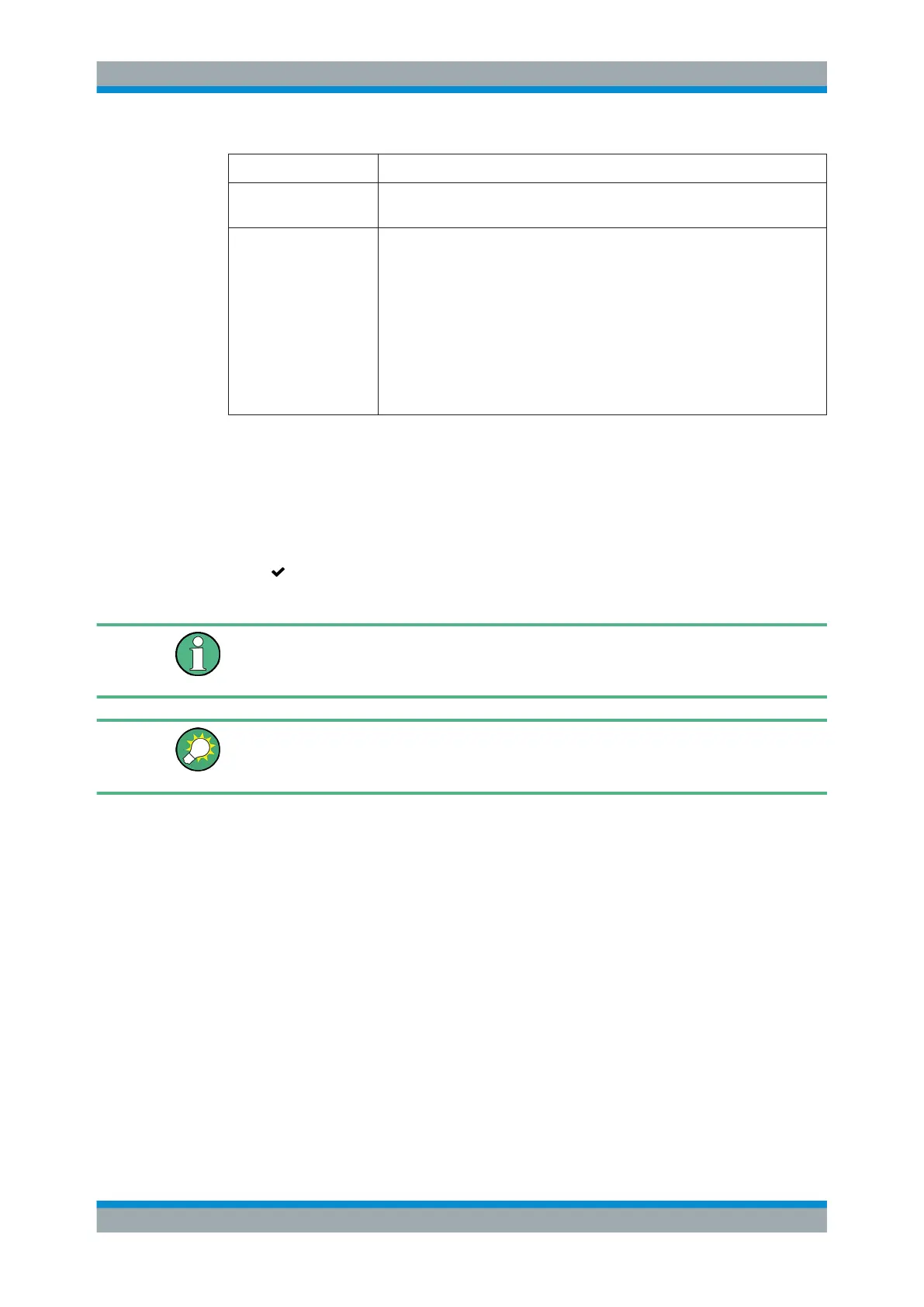
Field Description
"Protocol" Optional: Select the protocol type to be used from the drop-down list. UDP is
pre-selected by default.
"Message Level" From the drop-down list, select the minimum logged severity level of each mes-
sage source that can generate log messages:
●
off – no messages are sent to the syslog server
●
emergency – system is unusable (highest priority)
●
alert – action must be taken immediately
●
critical – critical conditions
●
error – error conditions
●
warning – warning conditions
●
notice – normal but significant conditions
●
info – informational messages
●
debug – debug-level messages (lowest priority)
The buttons at the bottom right of the editor panel depend on whether you add a new
remote syslog server or edit an existing server. For a newly configured server, click
"Create" to add the server to the list of available remote syslog servers or "Cancel" to
discard your changes. To edit an existing server, click "Save" to store the reconfigured
server or "Reset" to discard your changes. You can click "Close" to shut the editor
panel as long as no changes have been made on it.
Click " Activate" in the toolbar at the top of the desktop to apply your configuration
changes.
You can create multiple remote syslog servers within one network zone or for several
zones. If the syslog server is not located within the managed network, an additional
firewall rule may be needed to ensure connectivity.
"IPS/IDS" , "Webfilter" , "NAT Logging" , "Firewall Alert" and "Malware" log messages
sent to the remote syslog servers are based on the Common Event Format (CEF)
standard.
For detailed instructions, see Chapter 4.5, "Setting Up a Syslog Server", on page 146.
3.4.2.4 SSL Proxy
The "SSL Proxy" settings allow you to select the certificate that is used to encrypt
secure sessions and specify what to do when a user visits a site with an invalid certifi-
cate.
A proxy is a program which communicates between a client (an application, for exam-
ple a web browser) and a server (for example a web server). An SSL certificate is a
digital file that authenticates the identity of an object and is used to encrypt information
which is transmitted between client and server. The SSL proxy is used to intercept
these SSL encrypted connections. Thus gateprotect Firewall can evaluate the incom-
ing traffic and apply the configured firewall rules to it.
Navigate to "Network > SSL Proxy" to configure the settings for the SSL proxy.
Menu Reference
 Loading...
Loading...