Firewall functions: IPTABLES
PACKETS ALTERATION WITH THE MANGLE TABLE
Mangle tables (-t mangle) are used to modify the IP or TCP header of a packet. They are generally
used to change the value of the IP TOS or TCP MSS fields. It contains the following chains:
It modifies incoming packets
It modifies packets before they are sent.
It modifies packets in transit.
It modifies packets received through a network interface before they are routed.
It modifies packets before they are sent through a network interface.
For example, in order to set the maximum throughput for the SSH protocol:
iptables -t mangle -A FORWARD -p tcp --dport 22 -j TOS --set-tos Maximize-Throughput
In order to modify TOS for reducing the latency of DNS packets:
iptables -t mangle -A FORWARD -p udp --dport 53 -j TOS --set-tos Minimize-Delay
In order to set MSS to a value of 1400:
iptables -A FORWARD -p tcp --tcp-flags SYN,RST SYN -j TCPMSS --set-mss 1400
In order to adapt the value of MSS to that of MTU :
iptables -A FORWARD -p TCP --TCP-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
In order to set the DSCP value equal to 32 for packets which cross a GRE tunnel:
iptables –t mangle -A POSTROUTING –p 47 -j DSCP --set-dscp 32
APPLYING RULES ON PACKETS
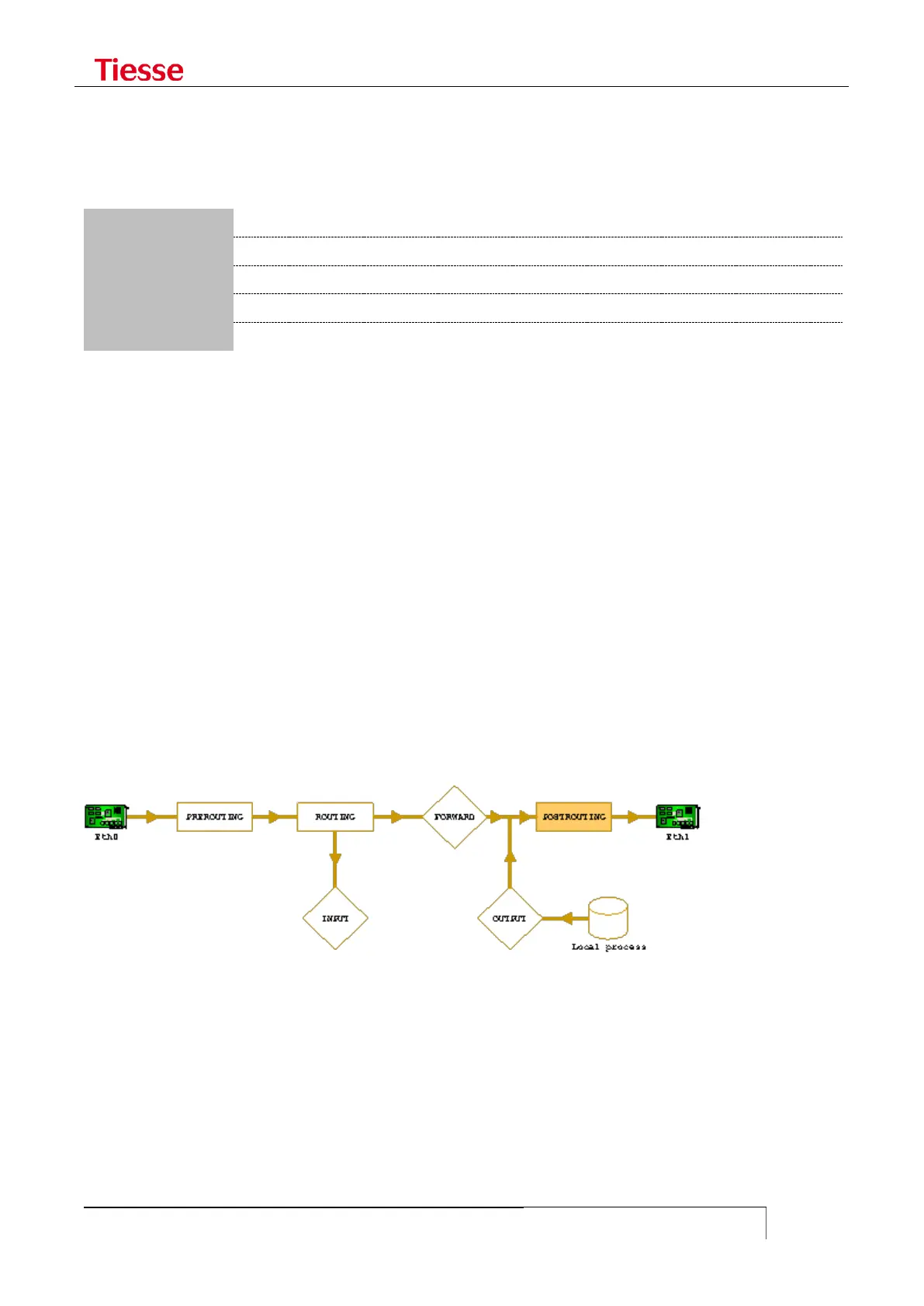
The typical path of an IP packet is shown in the following figure:
The packet enters via the network interface (eth0 in the example) and before the routing process it
is subjected to the rules in the PREROUTING chain. During this step Destination NAT (DNAT) rules are
applied if the matches in the chain are matched in the incoming packet.
If the packet, according to the routing table, is addressed to the output interface (eth1 in the figure)
rules in the FORWARD chain are applied. If the packet is addressed to the router, rules in the INPUT
chain are applied
If a packet has been generated by local router process, the rules in the OUTPUT chain are applied.
 Loading...
Loading...