Firewall functions: IPTABLES
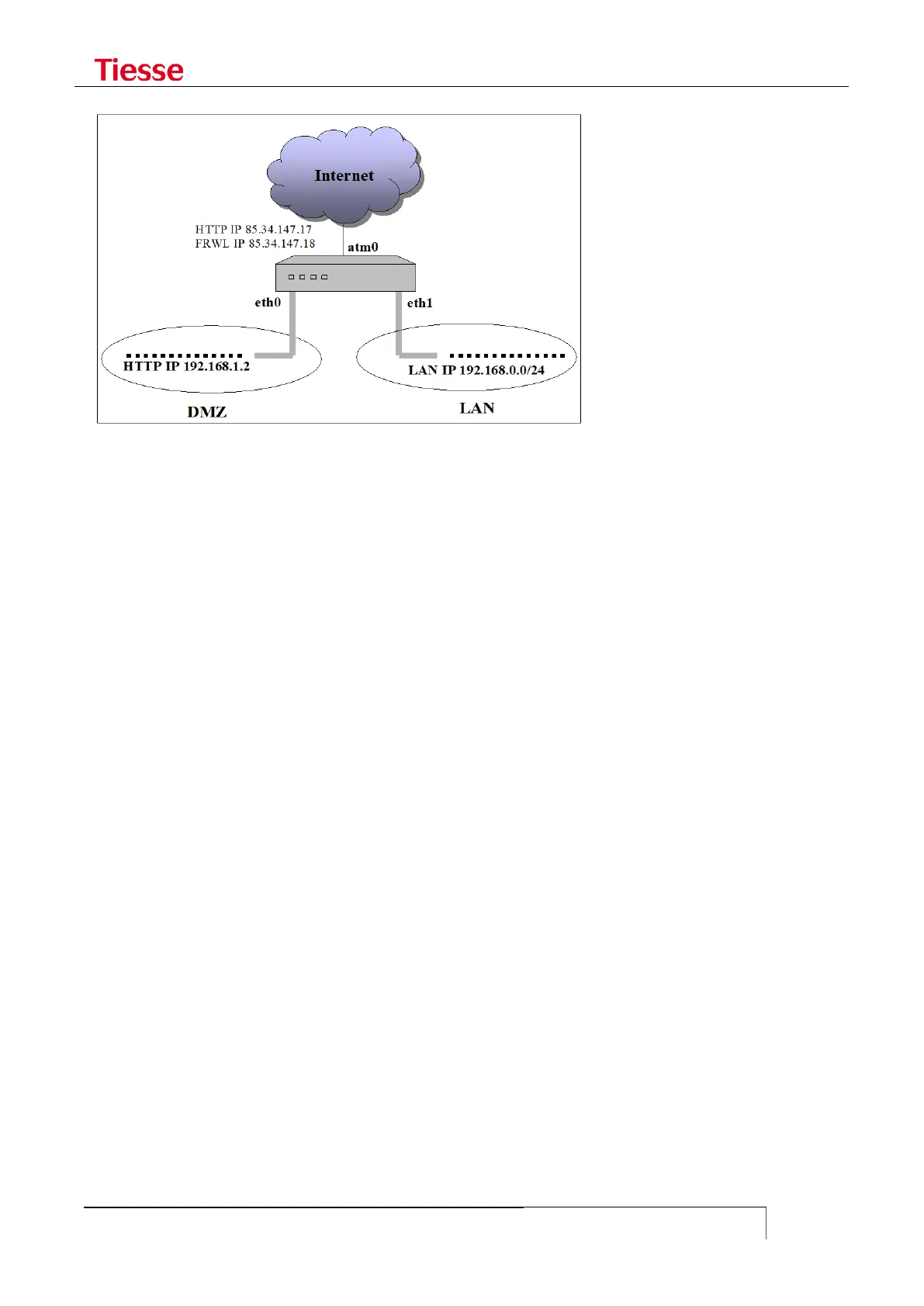
where the router, to which public addresses 85.34.147.17 and 85.34.147.18 are assigned, is
connected:
to the public network through the atm0 interface
to the internal LAN with address 192.168.0.0/24 through the eth1 interface
to the DMZ LAN with address 192.168.1.0/24 through the eth0 interface
Within DMZ there is an HTTP server with address 192.168.1.2.
Users access the HTTP server through the public address 85.34.147.17.
# The default policy is to cancel packets
iptables –P INPUT DROP
iptables –P OUTPUT DROP
iptables –P FORWARD DROP
# Do not accept packets related to new sessions without SYN
iptables -A FORWARD -p tcp ! --syn -m state --state NEW -j DROP
iptables -A INPUT -p tcp ! --syn -m state --state NEW -j DROP
# Allow everything from LAN to outside
iptables -A FORWARD -i eth1 -o atm0 -j ACCEPT
# Allow everything from DMZ to outside
iptables -A FORWARD -i eth0 -o atm0 -j ACCEPT
# Allow everything from router to outside
iptables -A OUTPUT -o atm0 -j ACCEPT
# Allow everything between DMZ and LAN
iptables -A FORWARD -i eth0 -o eth1 -j ACCEPT
iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT
 Loading...
Loading...