47-32
Software Configuration Guide—Release IOS XE 3.3.0SG and IOS 15.1(1)SG
OL-25340-01
Chapter 47 Configuring Port Security
Configuring Port Security with Other Features/Environments
–
MAC1 <---> IP2, invalid
–
MAC2 <---> IP1, invalid
IP traffic with the correct source IP and MAC address binding will be permitted and port security
will dynamically learn its MAC address. IP traffic with source addresses that are not in the binding
will be treated as invalid packets and dropped by port security. To prevent a denial of service attack,
you must configure port security rate limiting for the invalid source MAC address.
802.1X Authentication
You might want to configure port security with 802.1X authentication to prevent MAC spoofing. 802.1X
is not supported on regular or private VLAN trunks. On access ports and PVLAN host or promiscuous
ports, both port security and 802.1X can be configured simultaneously. When both are configured, hosts
must be 802.1X authenticated before port security can secure the MAC address of the host. Both 802.1X
and port security must approve of the host or a security violation will be triggered. The type of security
violation will depend on which feature rejects the port: if the host is allowed by 802.1X (for example,
because the port is in multihost mode) but is disallowed by port security, the port-security violation
action will be triggered. If the host is allowed by port security but rejected by 802.1X (for example,
because the host is not authorized on a single-host mode port) then the 802.1X security violation action
will be triggered.
Note 802.1X, port-security and VVID can all be configured on the same port.
For more information on the interaction between 802.1X and port security, see “Using 802.1X with Port
Security” on page 19.
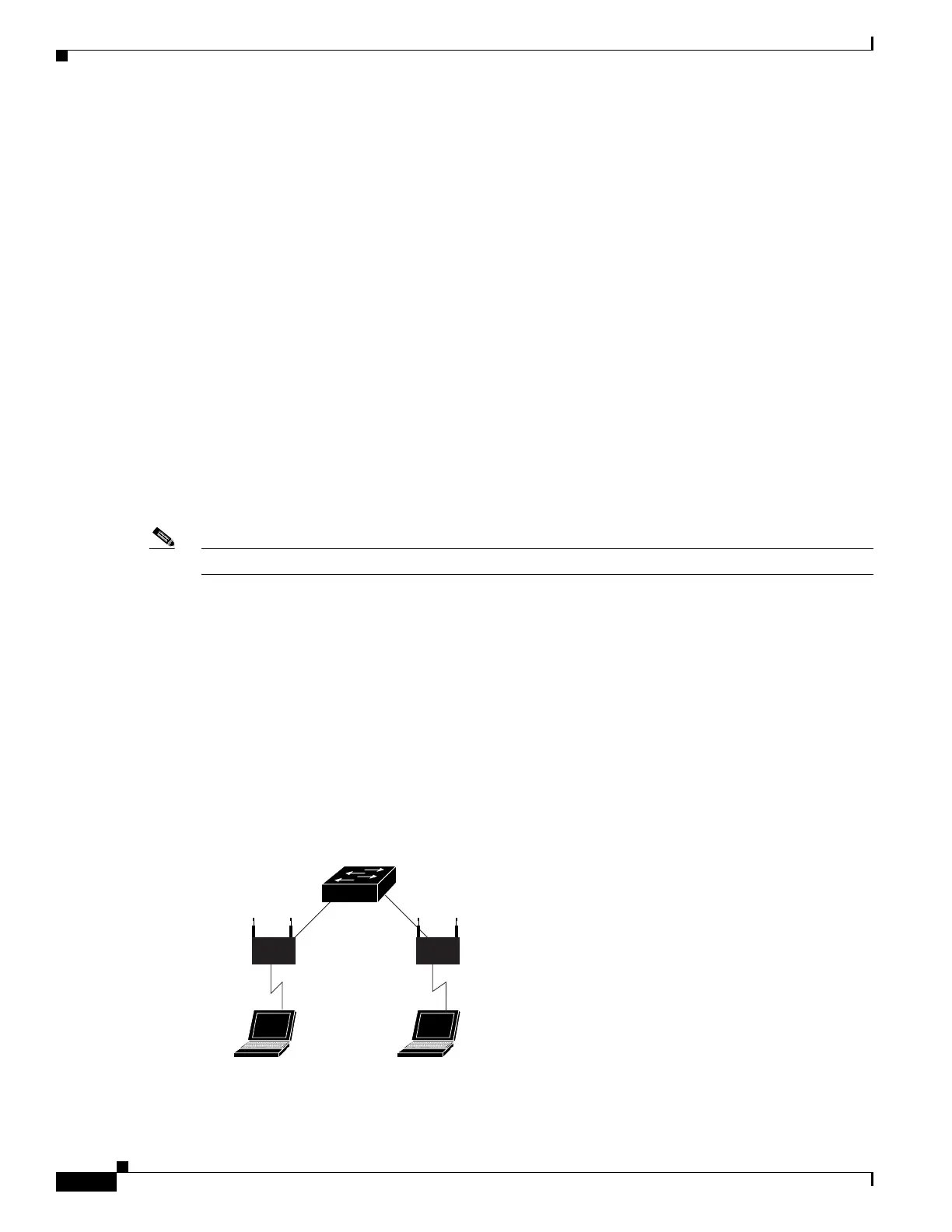
Configuring Port Security in a Wireless Environment
If access points are connected to a secure port, do not configure a static MAC address for your users. A
MAC address might move from one access point to another and might cause security violations if both
the access points are connected on the same switch.
Figure 47-3 illustrates a typical topology of port security in a wireless environment.
Figure 47-3 Port Security in a Wireless Environment
Wireless laptop
"roamed" out AP2
Wireless laptop
associated with AP1
140990
AP1 AP2
Switch

 Loading...
Loading...




















