44-13
Software Configuration Guide—Release IOS XE 3.3.0SG and IOS 15.1(1)SG
OL-25340-01
Chapter 44 Configuring 802.1X Port-Based Authentication
About 802.1X Port-Based Authentication
Feature Interaction
This section lists feature interactions and restrictions when MAB is enabled. If a feature is not listed,
assume that it interacts seamlessly with MAB (such as Unidirectional Controlled Port).
• MAB can only be enabled if 802.1X is configured on a port. MAB functions as a fall back
mechanism for authorizing MACs. If you configure both MAB and 802.1X on a port, the port
attempts to authenticate using 802.1X. If the host fails to respond to EAPOL requests and MAB is
configured, the 802.1X port is opened up to listen to packets and to grab a MAC address, rather than
attempt to authenticate endlessly.
Based on the default 802.1X timer values, the transition between mechanisms takes approximately
90 seconds. You can shorten the time by reducing the value of the transmission period time, which
affects the frequency of EAPOL transmission. A smaller timer value results in sending EAPOLs
during a shorter time interval. With MAB enabled, after 802.1X performs one full set of EAPOLs,
the learned MAC address is forwarded to the authentication server for processing.
The MAB module performs authorization for the first MAC address detected on the wire. The port
is considered authorized once a valid MAC address is received that RADIUS approves of.
802.1X authentication can re-start if an EAPOL packet is received on a port that was initially
authorized as a result of MAB.
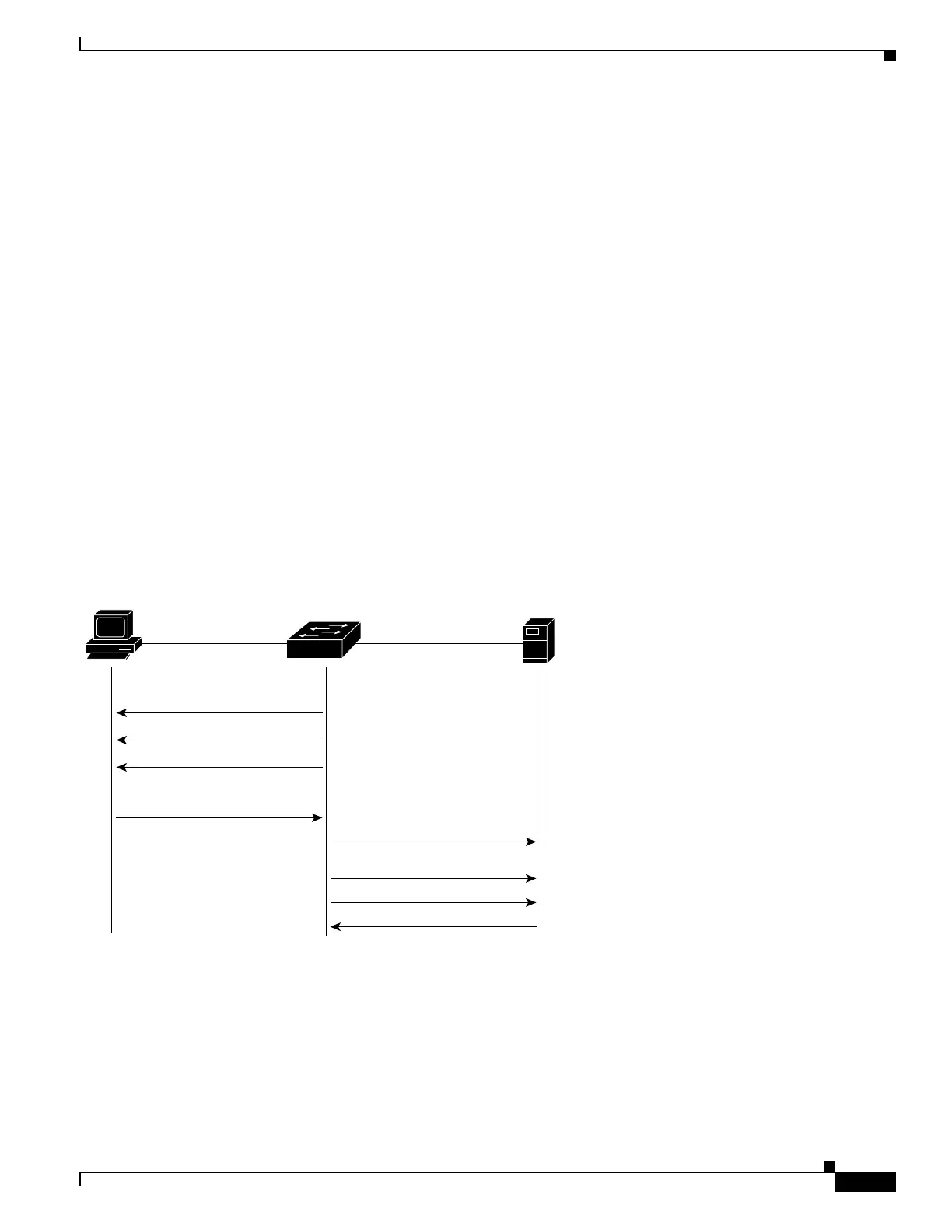
Figure 44-6 shows the message exchange during MAB.
Figure 44-6 Message Exchange during MAC Authentication Bypass
•
The authentication-failed VLAN is used only with dot1x-authentication-failed users. MAB is not
attempted with dot1x-authentication-failed users. If 802.1X authentication fails, a port moves to the
authentication-failed VLAN (if configured) whether MAB is configured or not.
EAPOL-Request/Identity
EAPOL-Request/Identity
EAPOL-Request/Identity
RADIUS Access-Request
(Device MAC)
RADIUS Access-Request
RADIUS Access-Request
RADIUS Accept
Packet
(Device MAC)
181377
Port
Authorized
Client
Workstation
Catalyst 4500
Network Access Switch
RADIUS

 Loading...
Loading...




















