44-4
Software Configuration Guide—Release IOS XE 3.3.0SG and IOS 15.1(1)SG
OL-25340-01
Chapter 44 Configuring 802.1X Port-Based Authentication
About 802.1X Port-Based Authentication
Authentication Initiation and Message Exchange
The switch or the client can initiate authentication. If you enable authentication on a port by using the
authentication port-control auto interface configuration command (dot1x port-control auto
command in Cisco IOS Release 12.2(46)SG and earlier releases), the switch must initiate authentication
when it determines that the port link state has changed. It then sends an EAP-request/identity frame to
the client to request its identity (typically, the switch sends an initial identity/request frame followed by
one or more requests for authentication information). Upon receipt of the frame, the client responds with
an EAP-response/identity frame.
However, if during bootup, the client does not receive an EAP-request/identity frame from the switch,
the client can initiate authentication by sending an EAPOL-start frame, which prompts the switch to
request the client’s identity.
If 802.1X is not enabled or supported on the network access switch, any EAPOL frames from the client
are dropped. If the client does not receive an EAP-request/identity frame after three attempts to start
authentication, the client transmits frames as if the port is in the authorized state. A port in the authorized
state means that the client was successfully authenticated. When the client supplies its identity, the
switch begins its role as the intermediary, passing EAP frames between the client and the authentication
server until authentication succeeds or fails. If the authentication succeeds, the switch port becomes
authorized.
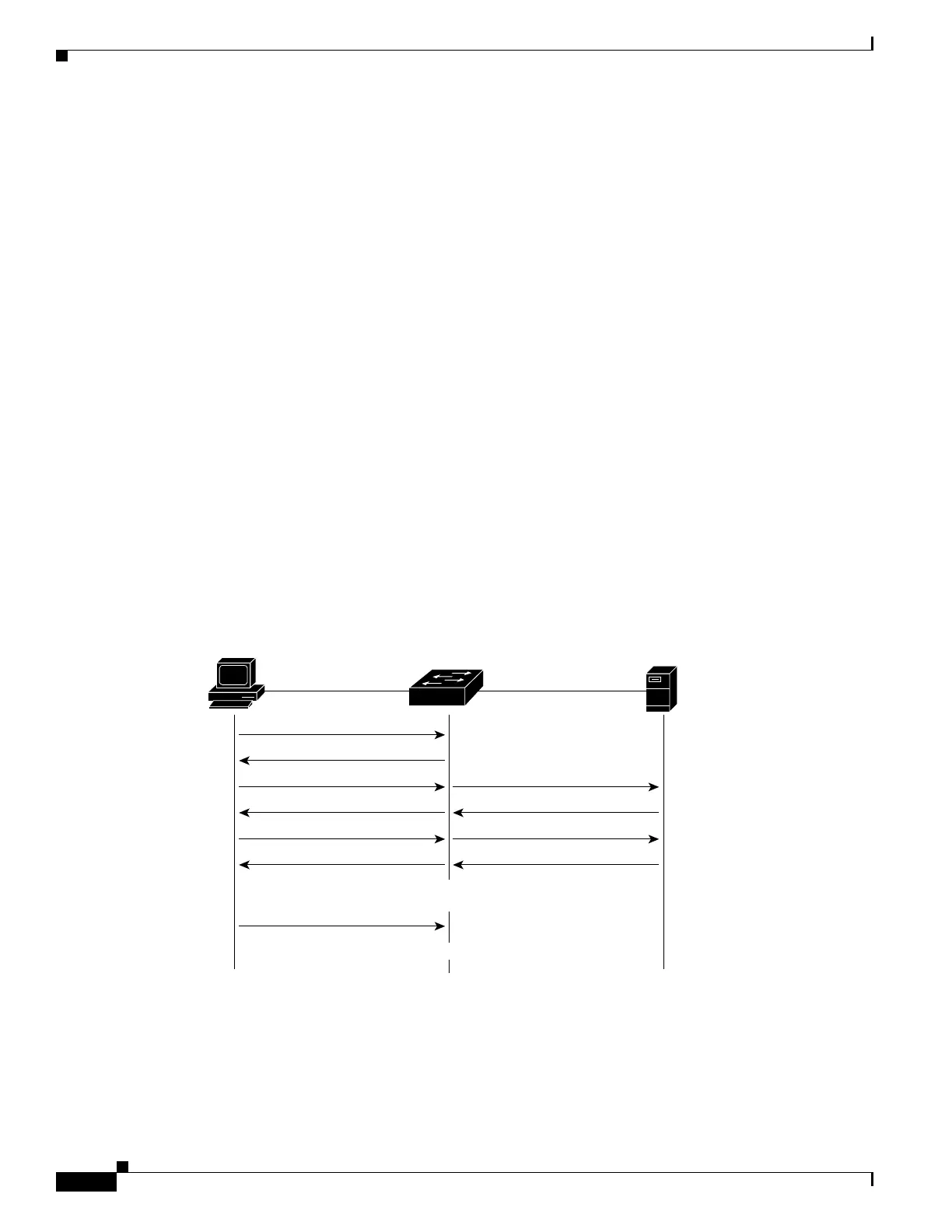
The specific exchange of EAP frames depends on the authentication method being used. Figure 44-2
shows a message exchange that is initiated by the client using the One-Time Password (OTP)
authentication method with an authentication server.
Figure 44-2 Message Exchange
Port Authorized
Port Unauthorized
Authenticator
EAPOL-Start
EAP-Request/Identity
EAP-Response/Identity
EAP-Request/OTP
EAP-Response/OTP
EAP-Success
RADIUS Access-Request
RADIUS Access-Challenge
RADIUS Access-Request
RADIUS Access-Accept
EAPOL-Logoff
94159
Supplicant Authentication
server
Client
Workstation
Catalyst 4500 Network
Access Switch
RADIUS

 Loading...
Loading...




















