189
Cisco Systems, Inc. www.cisco.com
Configuring IEEE 802.1x Port-Based
Authentication
Restrictions for Configuring IEEE 802.1x Port-Based
Authentication
To use this feature, the switch must be running the LAN Base image.
Information About Configuring IEEE 802.1x Port-Based
Authentication
IEEE 802.1x Port-Based Authentication
The standard defines a client-server-based access control and authentication protocol to prevent unauthorized clients
from connecting to a LAN through publicly accessible ports. The authentication server authenticates each client
connected to a switch port before making available any switch or LAN services.
Until the client is authenticated, IEEE 802.1x access control allows only Extensible Authentication Protocol over LAN
(EAPOL), Cisco Discovery Protocol (CDP), and Spanning Tree Protocol (STP) traffic through the port to which the client
is connected. After authentication, normal traffic passes through the port.
Device Roles
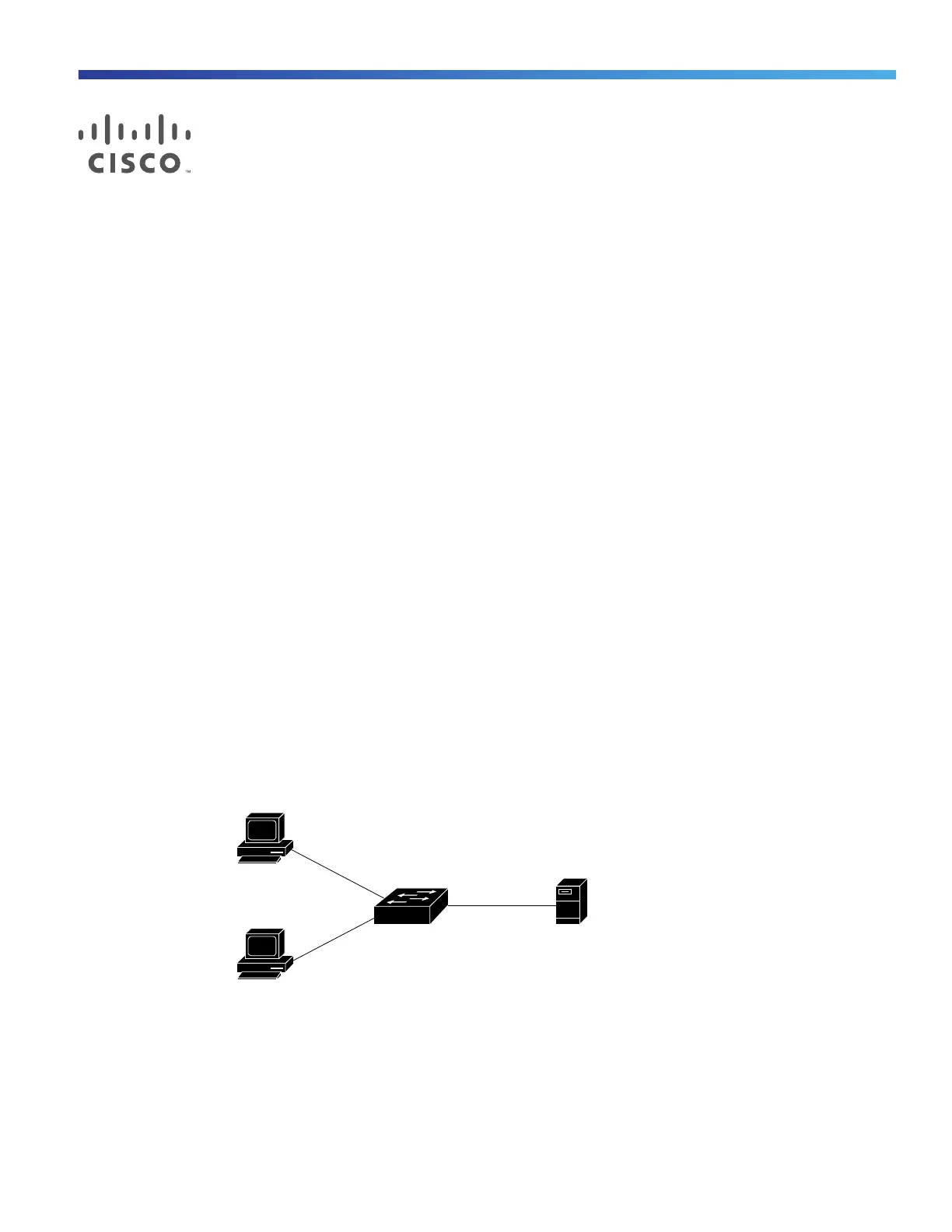
Figure 18 802.1x Device Roles
Client—The device (workstation) that requests access to the LAN and switch services and responds to requests from
the switch. The workstation must be running 802.1x-compliant client software such as that offered in the Microsoft
Windows XP operating system. (The client is the supplicant in the 802.1x standard.)
101229
Workstations
(clients)
Authentication
server
(RADIUS)

 Loading...
Loading...