787
Configuring IPv6 ACLs
Verifying IPv6 ACLs
Applying an IPv6 ACL to an Interface
BEFORE YOU BEGIN
Review the Guidelines and Limitations, page 782 for this feature.
DETAILED STEPS
EXAMPLE
This example shows how to apply the access list CISCO to outbound traffic on a Layer 3 interface:
Switch(config)# interface gigabitethernet 0/3
Switch(config-if)# no switchport
Switch(config-if)# ipv6 address 2001::/64 eui-64
Switch(config-if)# ipv6 traffic-filter CISCO out
Verifying IPv6 ACLs
You can display information about all configured access lists, all IPv6 access lists, or a specific access list by using one
or more of the following privileged EXEC commands.
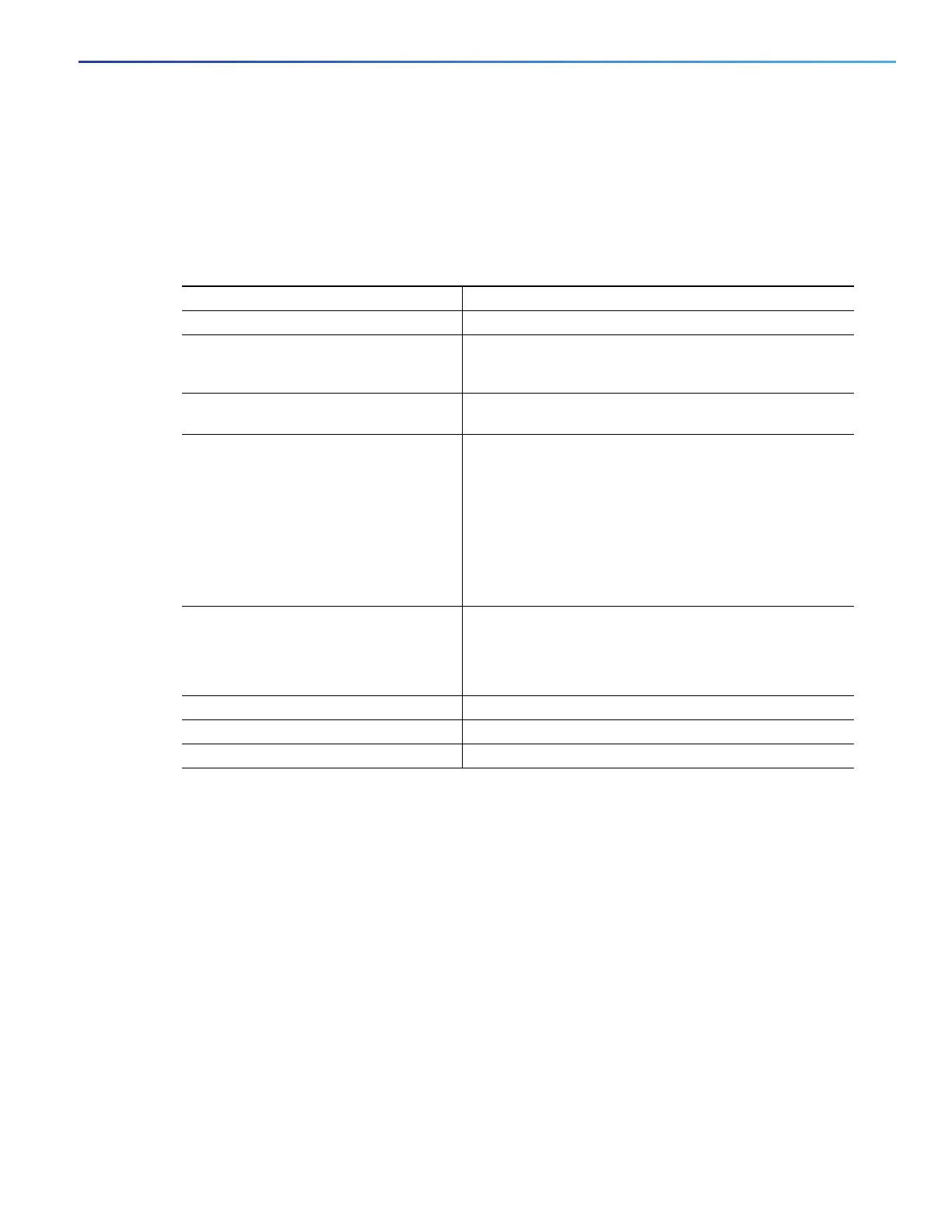
Command Purpose
1. configure terminal Enter global configuration mode.
2. interface interface-id Identify a Layer 2 interface (for port ACLs) or Layer 3
interface (for router ACLs) on which to apply an access list,
and enter interface configuration mode.
3. no switchport If applying a router ACL, change the interface from Layer 2
mode (the default) to Layer 3 mode.
4. ipv6 address ipv6-address Configure an IPv6 address on a Layer 3 interface (for router
ACLs).
Note: This command is not required on Layer 2 interfaces
or if the interface is already configured with an explicit IPv6
address.
Use the no ipv6 traffic-filter access-list-name interface
configuration command to remove an access list from an
interface.
5. ipv6 traffic-filter access-list-name {in |
out}
Apply the access list to incoming or outgoing traffic on the
interface.
Note: The out keyword is not supported for Layer 2
interfaces (port ACLs).
6. end Return to privileged EXEC mode.
7. show running-config Verify the access list configuration.
8. copy running-config startup-config (Optional) Save your entries in the configuration file.
 Loading...
Loading...