191
Configuring IEEE 802.1x Port-Based Authentication
Information About Configuring IEEE 802.1x Port-Based Authentication
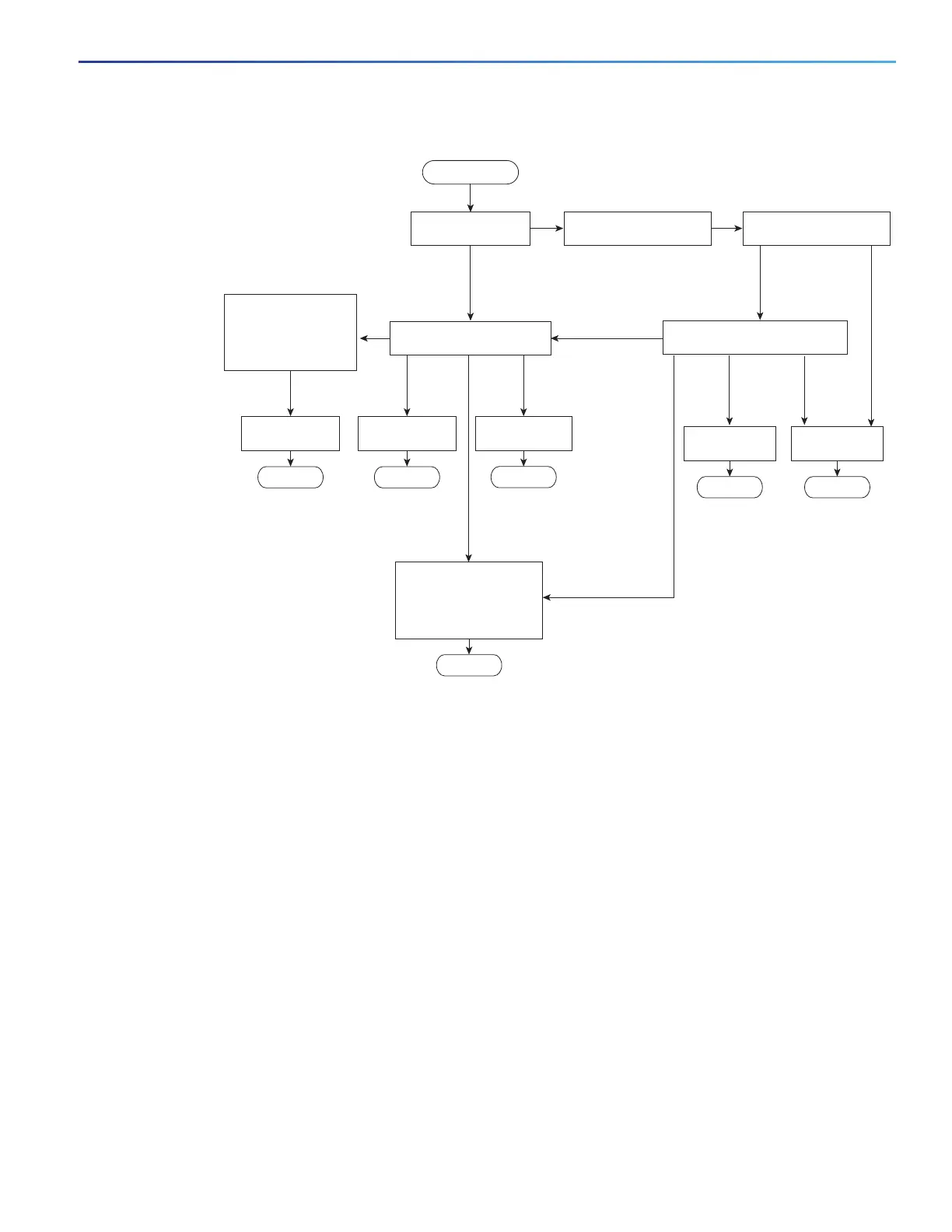
Figure 19 Authentication Flowchart
The switch reauthenticates a client when one of these situations occurs:
Periodic reauthentication is enabled, and the reauthentication timer expires.
You can configure the reauthentication timer to use a switch-specific value or to be based on values from the RADIUS
server.
After 802.1x authentication using a RADIUS server is configured, the switch uses timers based on the
Session-Timeout RADIUS attribute (Attribute[27]) and the Termination-Action RADIUS attribute (Attribute [29]).
The Session-Timeout RADIUS attribute (Attribute[27]) specifies the time after which reauthentication occurs.
The Termination-Action RADIUS attribute (Attribute [29]) specifies the action to take during reauthentication. The
actions are Initialize and ReAuthenticate. When the Initialize action is set (the attribute value is DEFAULT), the 802.1x
session ends, and connectivity is lost during reauthentication. When the ReAuthenticate action is set (the attribute
value is RADIUS-Request), the session is not affected during reauthentication.
You manually reauthenticate the client by entering the dot1x re-authenticate interface interface-id privileged EXEC
command.
If multidomain authentication (MDA) is enabled on a port, this flow can be used with some exceptions that are applicable
to voice authorization. For more information on MDA, see Multidomain Authentication, page 197.
281594
Client
identity is
invalid
All authentication
servers are down.
All authentication
servers are down.
Client
identity is
valid
The switch gets an
EAPOL message,
and the EAPOL
message
exchange begins.
1 = This occurs if the switch does not
detect EAPOL packets from the client.
Client MAC
address
identity
is invalid.
Client MAC
address
identity
is valid.
YesYes No
IEEE 802.1x authentication
process times out.
Start IEEE 802.1x port-based
authentication.
Use inaccessible
authentication bypass
(critical authentication)
to assign the critical
port to a VLAN.
1
Use MAC authentication
bypass.
Assign the port to
a VLAN.
Assign the port to
a restricted VLAN.
Done
Assign the port to
a guest VLAN.
Done
Done
Done
Assign the port to
a VLAN.
Done
1
Assign the port to
a guest VLAN.
Done
Is the client IEEE
802.1x capable?
Start
Is MAC authentication
bypass enabled?
1
User does not have a
certificate but the system
previously logged on to
the network using
a computer certificate.
No

 Loading...
Loading...