1-7
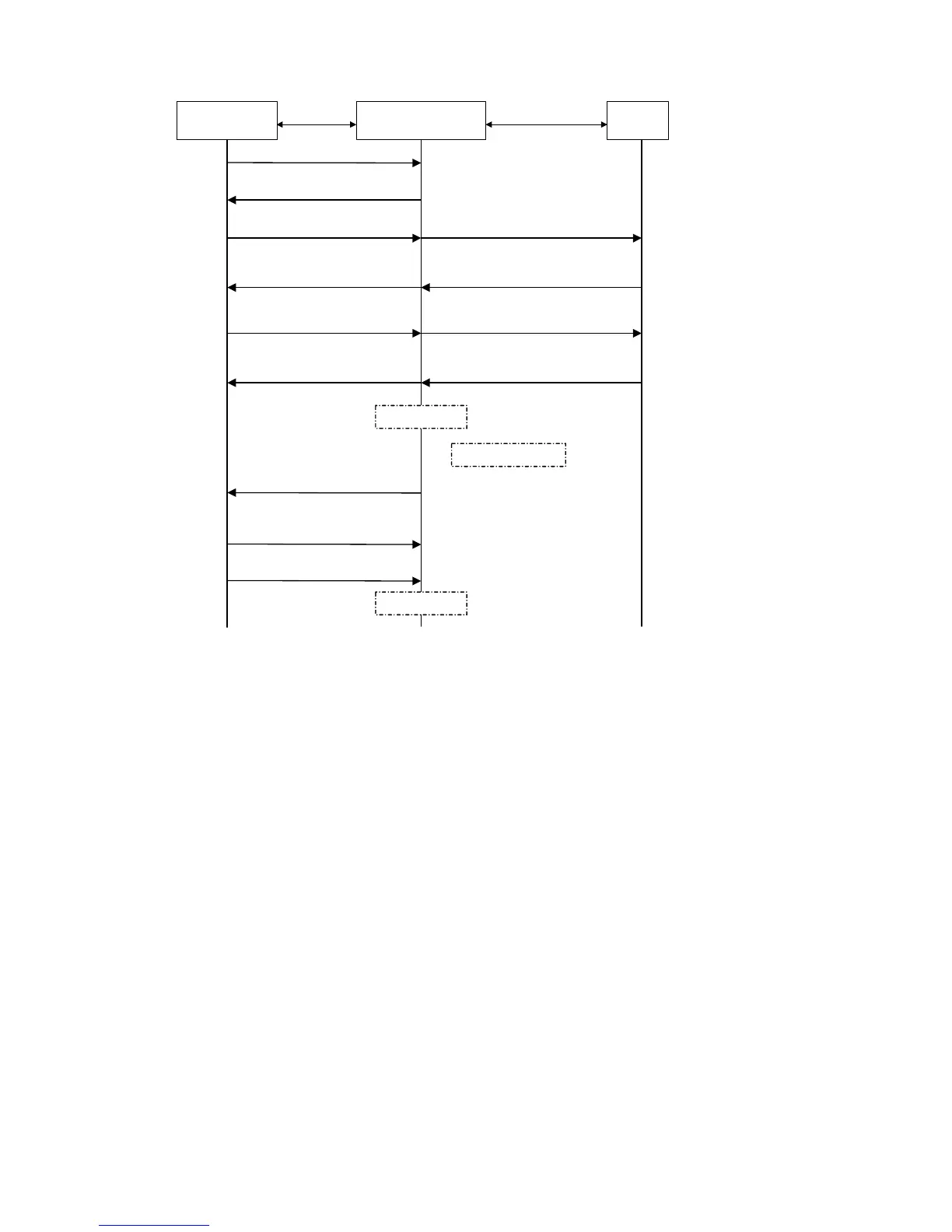
Figure 1-8 802.1x authentication procedure (in EAP relay mode)
Supplicant system
PAE
RADUIS
server
EAPOL EAPOR
EAPOL-Start
EAP- Request / Identity
EAP- Response / Identity
E AP- Request / M D5 challenge
EAP-Success
EAP- Response / MD5 challenge
RADIUS Access -Request
(EAP- Response / Identity)
RADIUS Access -Challenge
( EAP- Request / MD5 challenge)
RADIUS Access-Accept
(EAP-Success)
RADIUS Access - Request
(EAP- Response / MD5 challenge)
Port authorized
Handshake timer
Handshake request
[ EAP- Request / Identity ]
Handshake response
[ EAP-Response / Identity ]
EAPOL-Logoff
......
Port unauthorized
Authenticator system
PAE
The detailed procedure is as follows:
z A supplicant system launches an 802.1x client to initiate an access request by sending
an EAPoL-start packet to the switch, with its user name and password provided. The
802.1x client program then forwards the packet to the switch to start the authentication
process.
z Upon receiving the authentication request packet, the switch sends an
EAP-request/identity packet to ask the 802.1x client for the user name.
z The 802.1x client responds by sending an EAP-response/identity packet to the switch
with the user name contained in it. The switch then encapsulates the packet in a
RADIUS Access-Request packet and forwards it to the RADIUS server.
z Upon receiving the packet from the switch, the RADIUS server retrieves the user name
from the packet, finds the corresponding password by matching the user name in its
database, encrypts the password using a randomly-generated key, and sends the key
to the switch through an RADIUS access-challenge packet. The switch then sends the
key to the 802.1x client.
z Upon receiving the key (encapsulated in an EAP-request/MD5 challenge packet) from
the switch, the client program encrypts the password of the supplicant system with the
key and sends the encrypted password (contained in an EAP-response/MD5 challenge
packet) to the RADIUS server through the switch. (Normally, the encryption is
irreversible.)

 Loading...
Loading...











