Access Control Lists (ACLs) for the Series 3400cl and Series 6400cl Switches
Configuring and Assigning an ACL
■ Optional ACL log command (available for “Deny” ACLs only)
ip access-list < type > “< id-string >”< permit | deny > ip
< source-ip-address > < source-acl-mask >
< destination-ip-address > < destination-acl-mask > [ log ]
< permit | deny > tcp
< source-ip-address > < source-acl-mask > [< operator > < port-id >]
< destination-ip-address > < destination-acl-mask > [< operator > < port-id >] [ log ]
< permit | deny > udp
< source-ip-address > < source-acl-mask > [< operator > < port-id >]
< destination-ip-address > < destination-acl-mask > [< operator > < port-id >] [ log ]
.
exit
Note: The optional log
function appears only
with “deny” aces.
. .
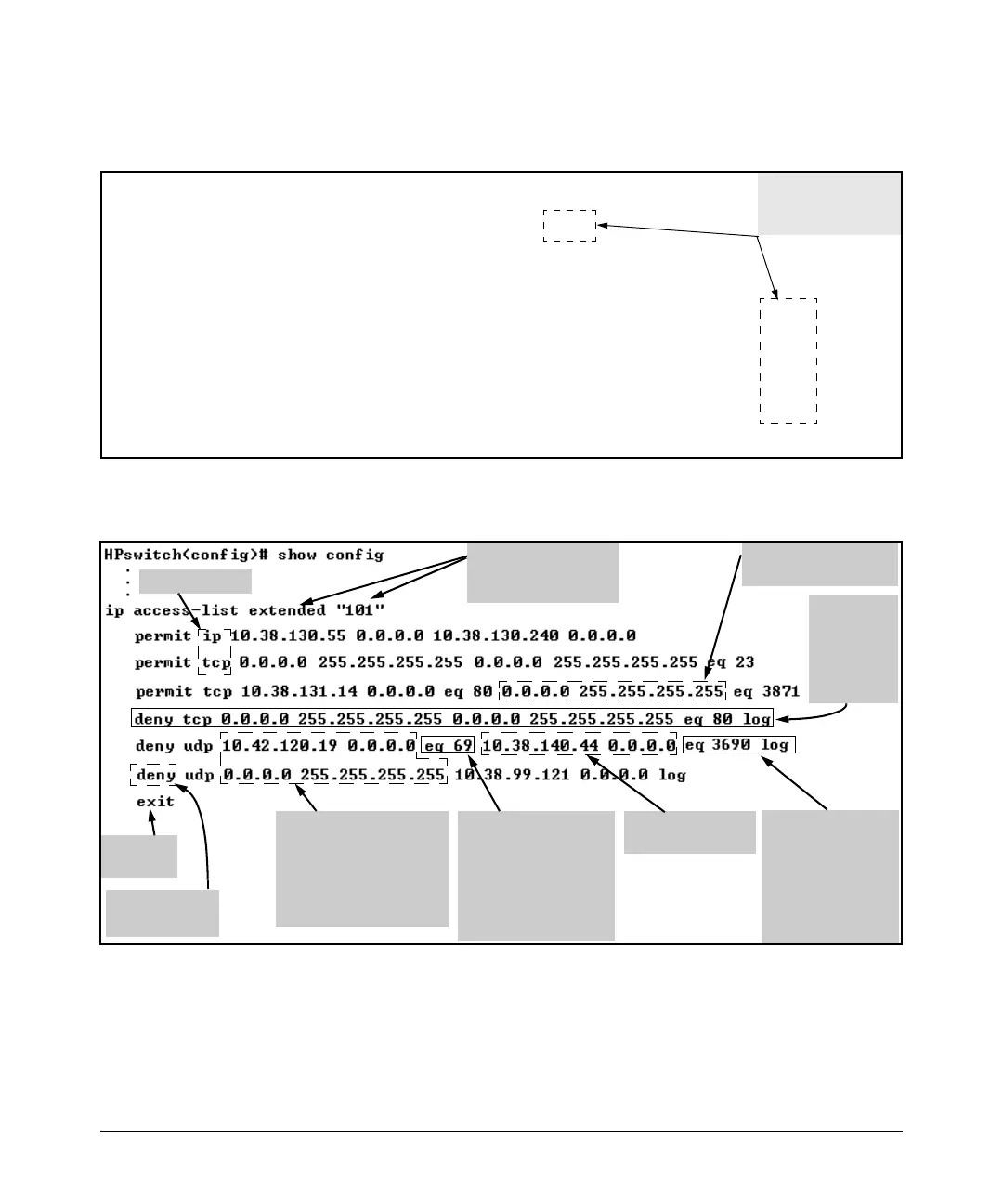
Figure 10-11. General Structure for an Extended ACL
For example, figure 10-12 shows how to interpret the entries in an extended
ACL.
Optional Source UDP or
TCP Operator and Port
Number
In this case, the ACL
specifies UDP port 69
packets coming from the
source IP address.
Protocol Types
End-of-List
Marker
Source IP Addresses and
Masks.
Upper entry denies certain
UDP packets from a single
host. Lower entry denies all
UDP packets from all hosts.
Optional Destination
UDP or TCP Operator
and Port Numbers
In this case, the ACL
specifies UDP port
number 3690.
Destination IP
Address and Mask
ACE Action
(permit or deny)
ACL List Heading with
List Type and ID String
(Name or Number)
Specifies all destination
IP addresses.
Denies TCP
Port 80
traffic to any
destination
from any
source.
Figure 10-12. Example of a Displayed Extended ACL Configuration
10-38

 Loading...
Loading...











