Cybersecurity 9810 series - User manual
29 7EN05-0390-08
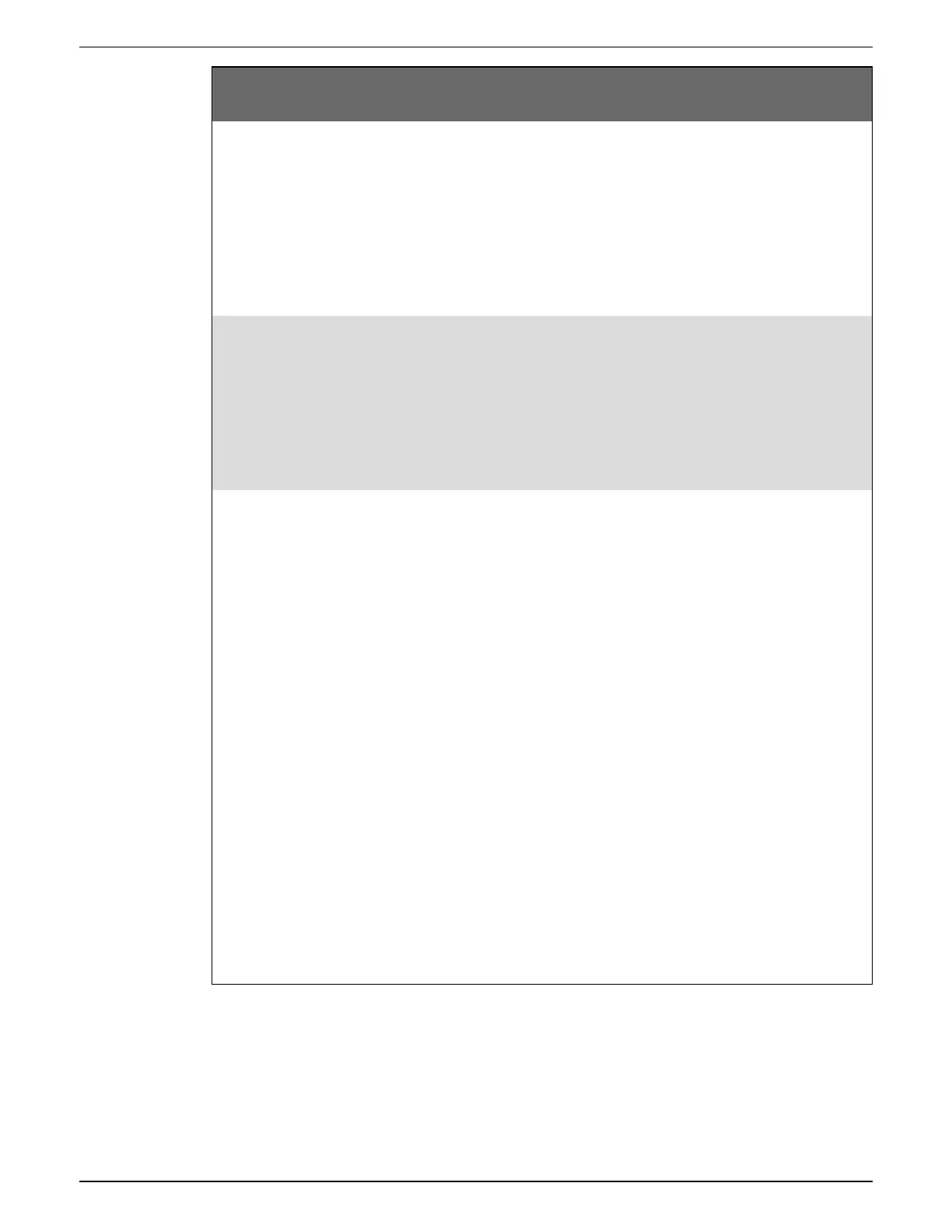
Security area Device security capabilities
Role in defense-in-
depth
Physical
•
Revenue-lock switch
•
Anti-tamper sealing points
•
LED lock status indicator on the
device
•
Revenue lock icon on the display.
These capabilities help
prevent unauthorized
access to revenue-
related parameters and
settings or leave clear
evidence that the device
has been physically
tampered with.
Information
confidentiality
•
SSH, SFTP, HTTPS support, Secure
ION, and Secure EtherGate
These secure protocols
employ cryptographic
algorithms, key sizes,
and mechanisms to help
prevent unauthorized
users from reading
information in transit.
Access
•
User authentication identifies and
authenticates software processes and
devices managing accounts.
•
Least privilege in multiple dimensions:
read, peak demand reset, time sync,
test mode, meter configuration, and
security and communications
configuration.
•
User account lockout limits the
number of unsuccessful login
attempts.
•
Use control restricts allowed actions
to the authorized use of the control
system.
•
Supervisors can override user
authorizations by deleting user
accounts.
•
Password strength feedback using
ION Setup.
These capabilities help
enforce authorizations
assigned to users,
segregation of duties,
and least privilege.

 Loading...
Loading...











