SmartDefense Categories
416 Check Point UTM-1 Edge User Guide
Table 90: Header Rejection Fields
In this field… Do this…
Action Specify what action to take when an HTTP header-based exploit is
detected, by selecting one of the following:
• Block. Block the attack.
• None. No action. This is the default.
Track Specify whether to log HTTP header-based exploits, by selecting one of
the following:
• Log. Log the attack.
• None. Do not log the attack. This is the default.
HTTP header values
list
Select the HTTP header values to detect.
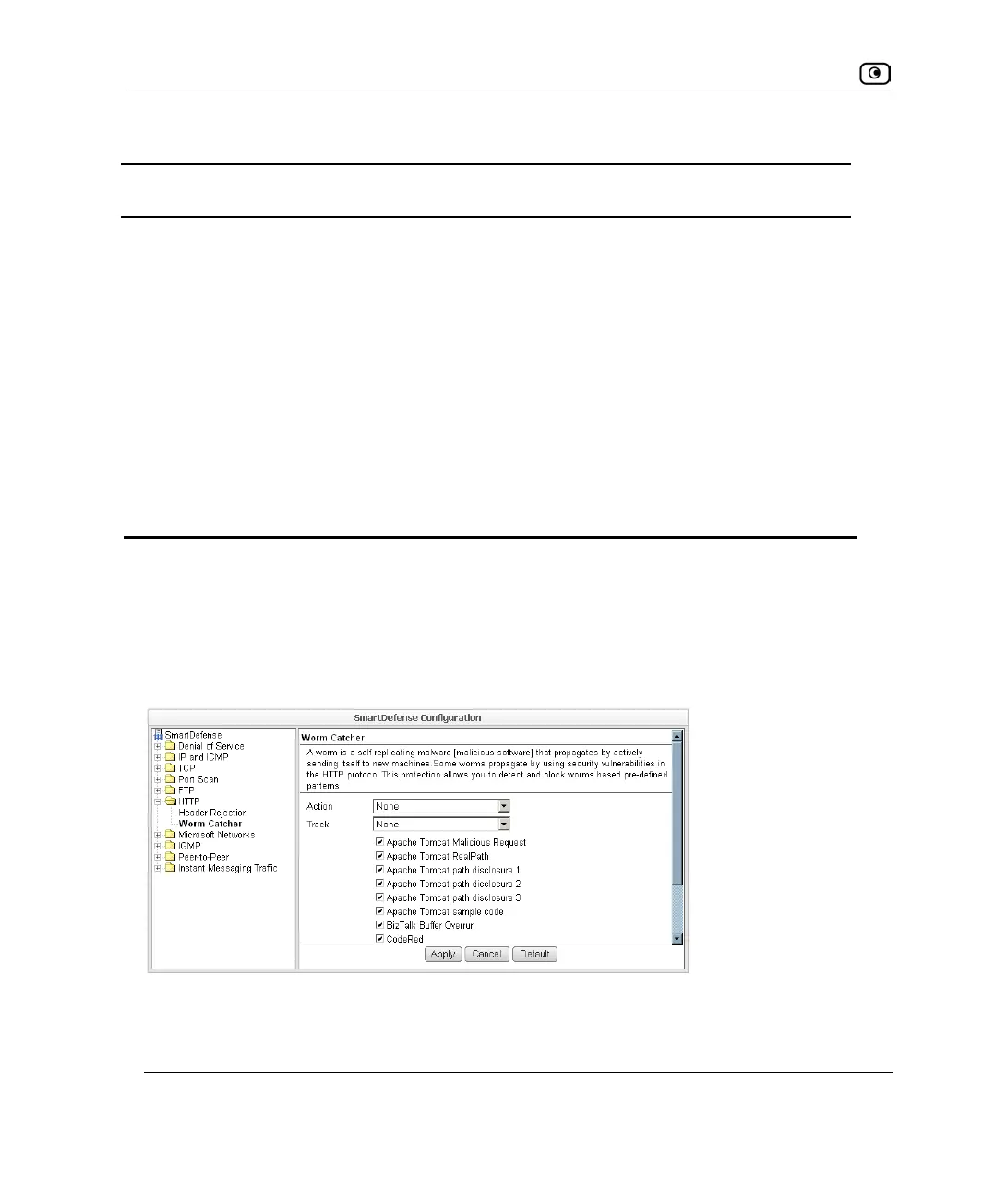
Worm Catcher
A worm is a self-replicating malware (malicious software) that propagates by actively
sending itself to new machines. Some worms propagate by using security vulnerabilities in
the HTTP protocol.
You can specify how HTTP-based worm attacks should be handled.
 Loading...
Loading...











