SmartDefense Categories
Chapter 13: Using SmartDefense 419
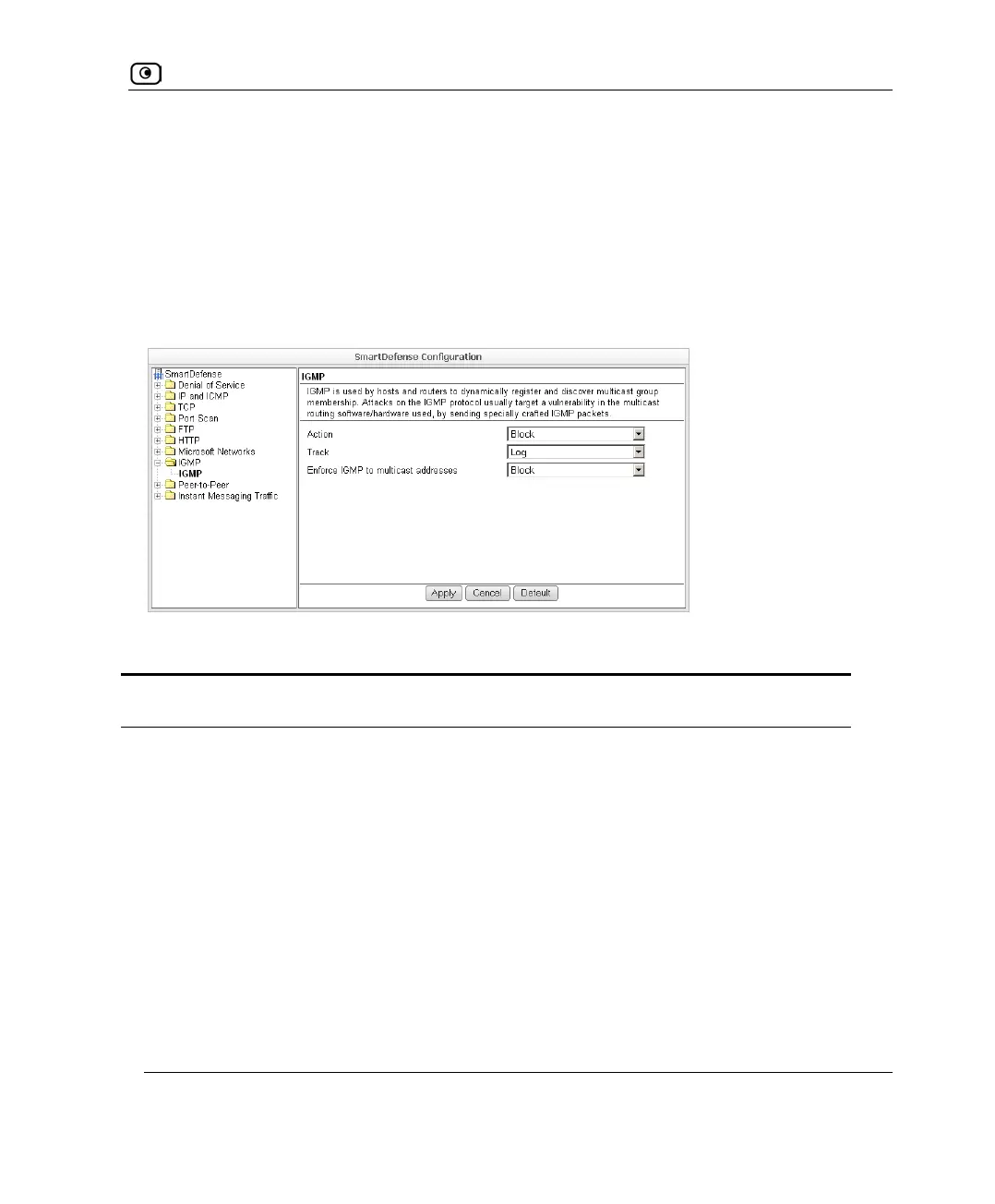
IGMP
This category includes the IGMP protocol.
IGMP is used by hosts and routers to dynamically register and discover multicast group
membership. Attacks on the IGMP protocol usually target a vulnerability in the multicast
routing software/hardware used, by sending specially crafted IGMP packets.
You can configure how IGMP attacks should be handled.
Table 93: IGMP Fields
In this field… Do this…
Action Specify what action to take when an IGMP attack occurs, by selecting
one of the following:
• Block. Block the attack. This is the default.
• None. No action.
Track Specify whether to log IGMP attacks, by selecting one of the following:
• Log. Log the attack. This is the default.
• None. Do not log the attack.
 Loading...
Loading...











