Viewing VPN Tunnels
538 Check Point UTM-1 Edge User Guide
Table 111: VPN Tunnels Page Fields
This field… Displays…
Type The currently active security protocol (IPSEC).
Source
The IP address or address range of the entity from which the tunnel
originates.
The entity's type is indicated by an icon. See VPN Tunnel Icons on page
539.
Destination The IP address or address range of the entity to which the tunnel is
connected.
The entity's type is indicated by an icon. See VPN Tunnel Icons on page
539.
Security The type of encryption used to secure the connection, and the type of
Message Authentication Code (MAC) used to verify the integrity of the
message. This information is presented in the following format: Encryption
type/Authentication type.
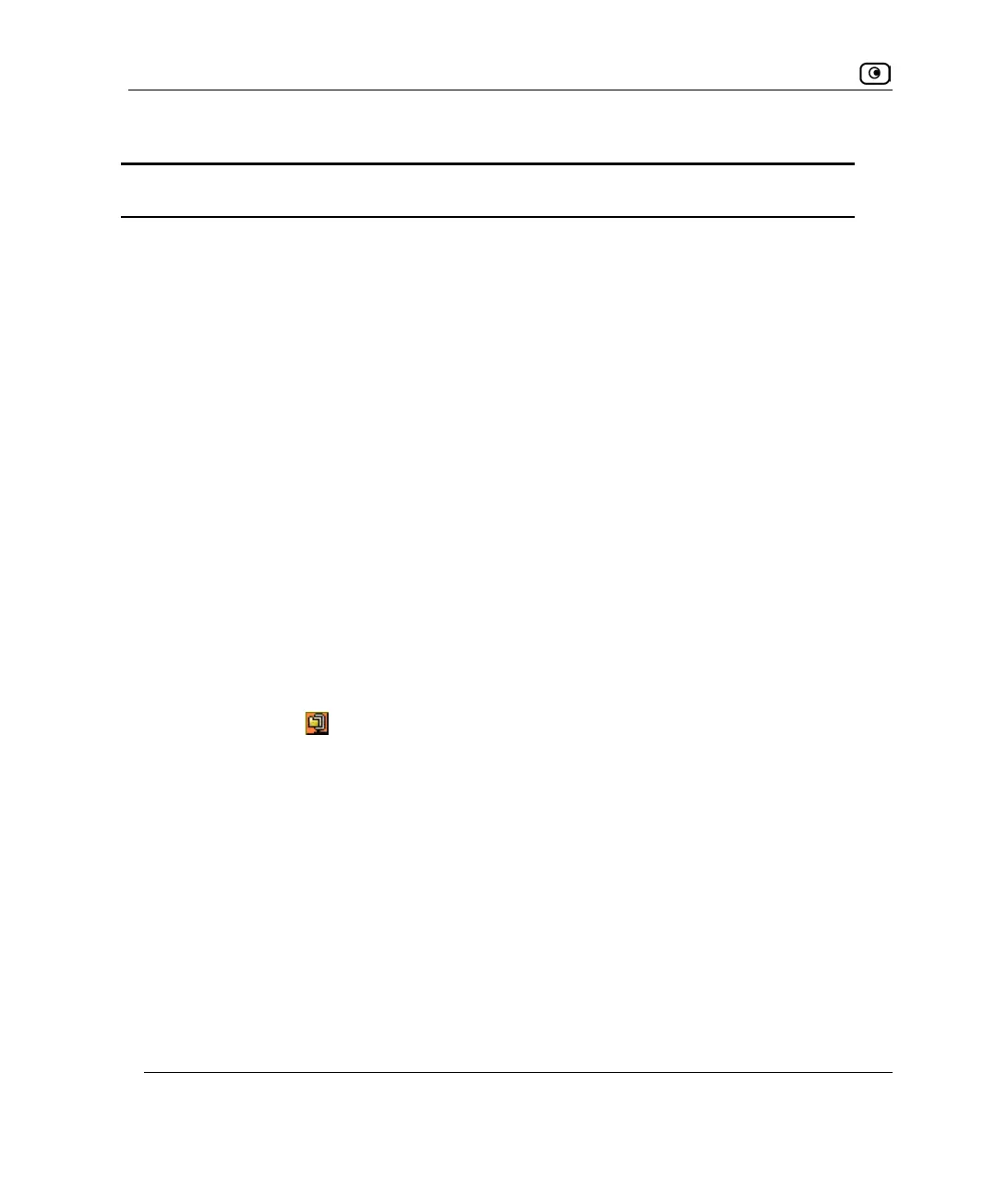
In addition, if IPSec compression is enabled for the tunnel, this field displays
the
icon.
Note: All VPN settings are automatically negotiated between the two sites.
The encryption and authentication schemes used for the connection are the
strongest of those used at the two sites.
Your UTM-1 appliance supports AES, 3DES, and DES encryption schemes,
and MD5 and SHA authentication schemes.
 Loading...
Loading...











