In case social media authentication is used, the user needs to allow some traffic between the AP and social
medial platforms (Facebook API as example) to send authentication credentials and receive reply, this
traffic can be allowed using the Authentication rules which are explained below.
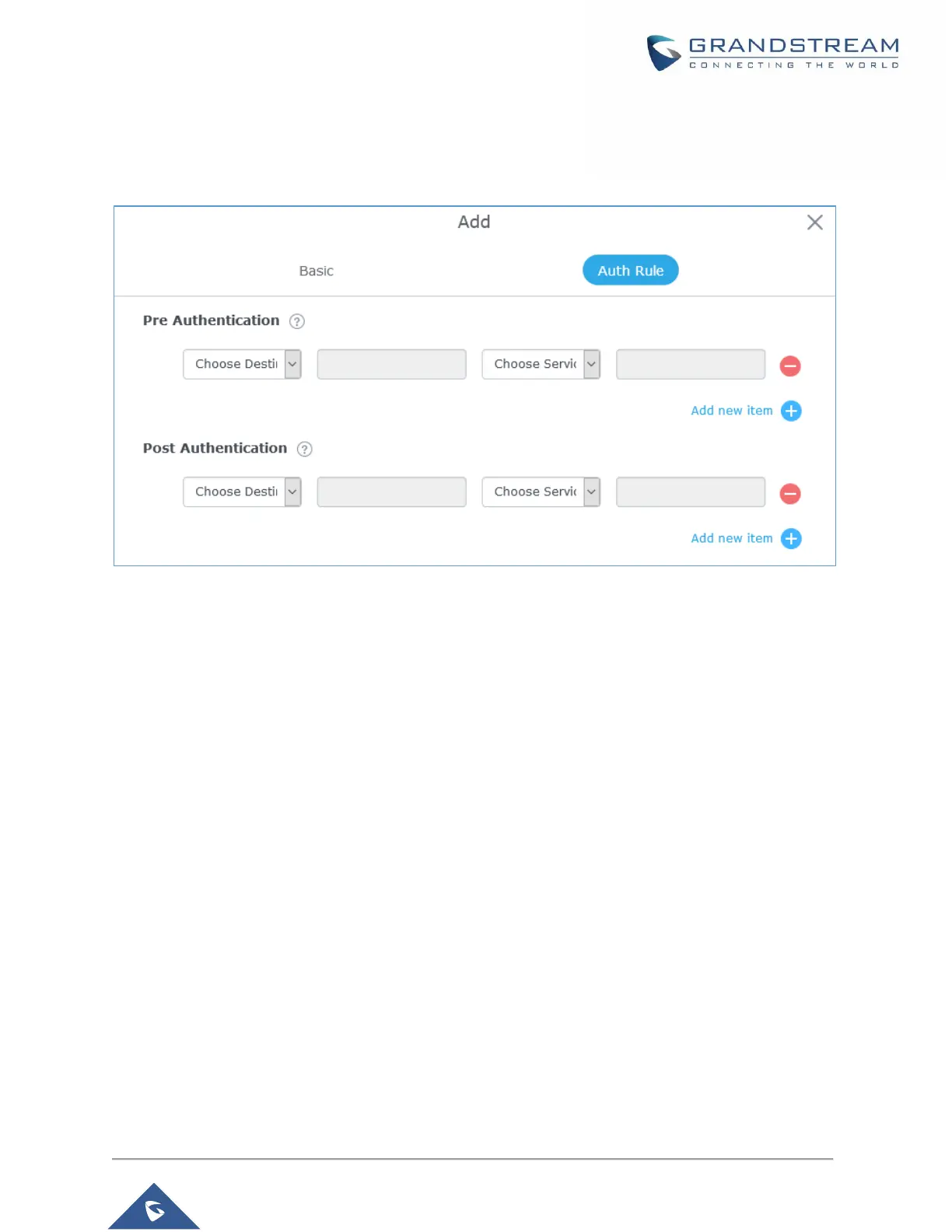
Figure 73: Authentication rules
Pre-Authentication Rules
Using this option, users can set rules to match traffic that will be allowed for connected Wi-Fi users before
authentication process. This can be needed for example to setup Facebook authentication where some
traffic should be allowed to Facebook server(s) to process the user’s authentication. Or simply to be used
to allow some type of traffic for unauthenticated users.
Post-Authentication Rules
On the other hand, post authentication rules are used to match traffic that will be banned for Wi-Fi clients
after authentication. As an example, if you want to disallow connected Wi-Fi clients to issue Telnet or SSH
traffic after authentication then you can set post authentication rules to match that traffic and once a
connected client passes the authentication process they will be banned from issuing telnet and SSH
connections.
Splash Page
Files configuration page allows users to view and upload HTML pages and related files (images…).

 Loading...
Loading...