SmartDefense Categories
386 Check Point UTM-1 Edge User Guide
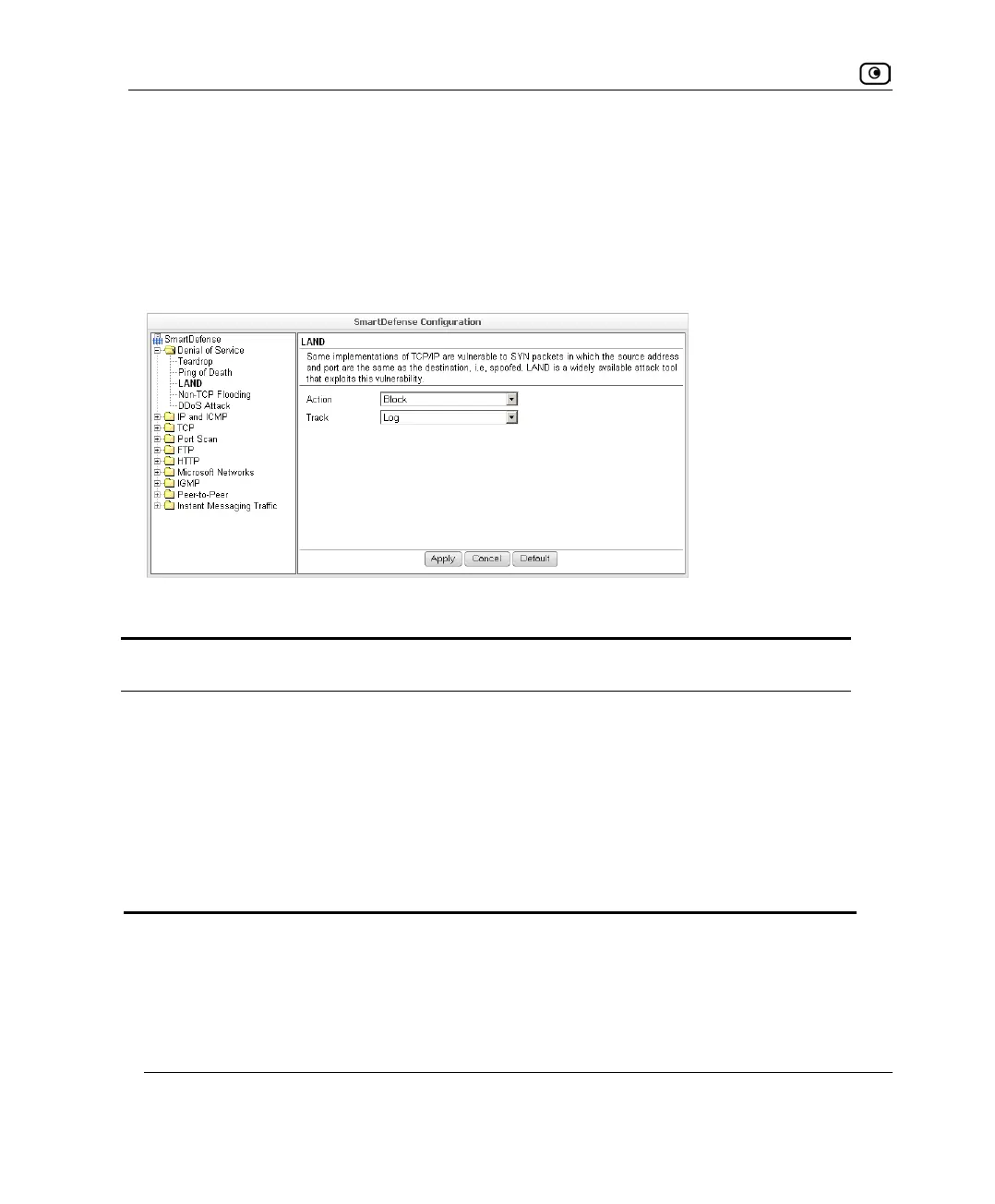
LAND
In a LAND attack, the attacker sends a SYN packet, in which the source address and port
are the same as the destination (the victim computer). The victim computer then tries to
reply to itself and either reboots or crashes.
You can configure how LAND attacks should be handled.
Table 70: LAND Fields
In this field… Do this…
Action Specify what action to take when a LAND attack occurs, by selecting one of
the following:
• Block. Block the attack. This is the default.
• None. No action.
Track Specify whether to log LAND attacks, by selecting one of the following:
• Log. Log the attack. This is the default.
• None. Do not log the attack.
 Loading...
Loading...











