64-36
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 64 General VPN Setup
ACL Manager
–
Manage—Displays the ACL Manager dialog box, in which you can configure Access Control
Lists (ACLs).
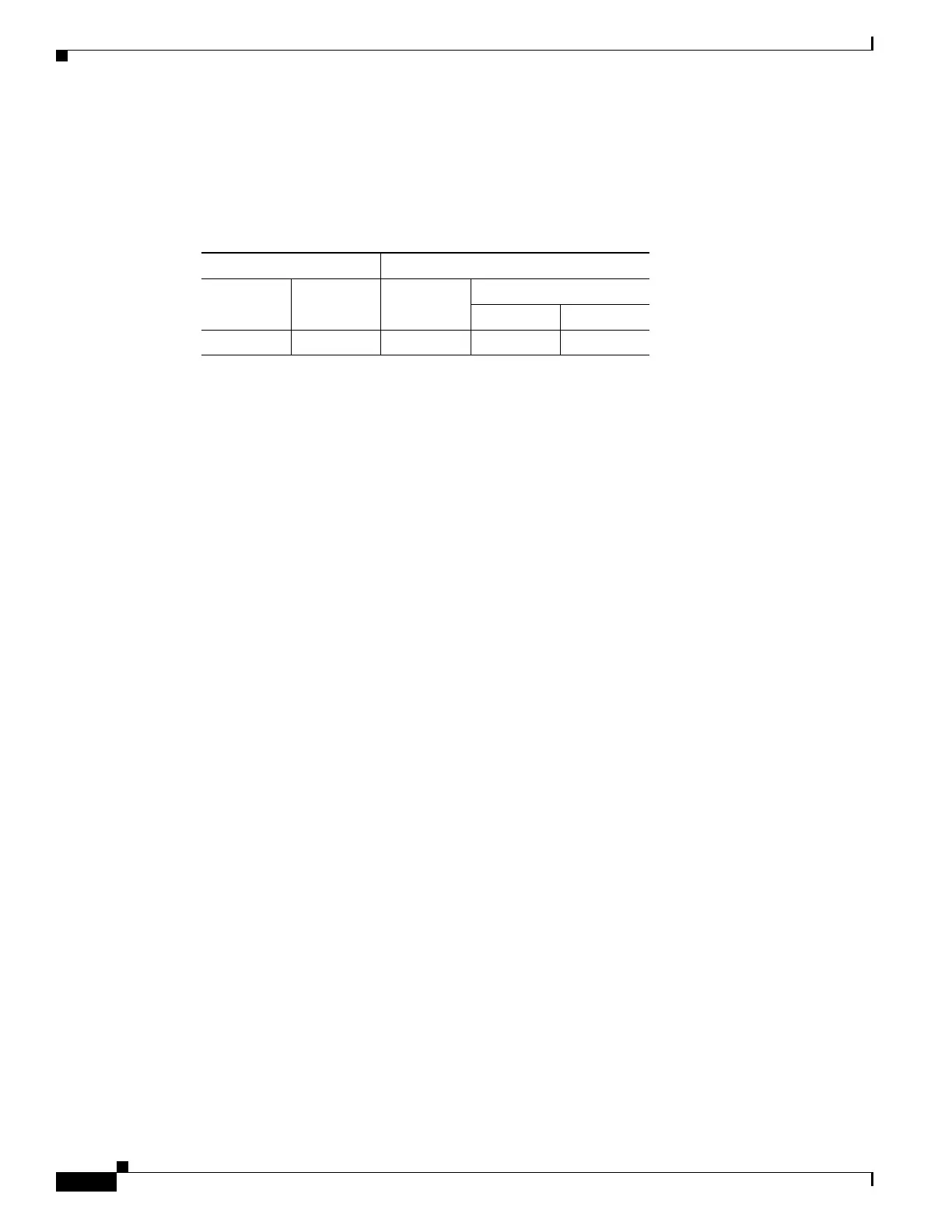
Modes
The following table shows the modes in which this feature is available:
Add/Edit Internal Group Policy > Hardware Client
The Add or Edit Group Policy > Hardware Client dialog box lets you configure settings for the VPN
3002 hardware client for the group policy being added or modified. The Hardware Client dialog box
parameters do not pertain to the ASA 5505 in client mode.
Fields
• Inherit—(Multiple instances) Indicates that the corresponding setting takes its value from the
default group policy, rather than from the explicit specifications that follow. This is the default
setting for all attributes in this dialog box.
• Require Interactive Client Authentication—Enables or disables the requirement for interactive
client authentication. This parameter is disabled by default. Interactive hardware client
authentication provides additional security by requiring the VPN 3002 to authenticate with a
username and password that you enter manually each time the VPN 3002 initiates a tunnel. With
this feature enabled, the VPN 3002 does not have a saved username and password. When you enter
the username and password, the VPN 3002 sends these credentials to the adaptive security appliance
to which it connects. The adaptive security appliance facilitates authentication, on either the internal
or an external authentication server. If the username and password are valid, the tunnel is
established.
When you enable interactive hardware client authentication for a group, the adaptive security
appliance pushes that policy to the VPN 3002s in the group. If you have previously set a username
and password on the VPN 3002, the software deletes them from the configuration file. When you
try to connect, the software prompts you for a username and password.
If, on the adaptive security appliance, you subsequently disable interactive hardware authentication
for the group, it is enabled locally on the VPN 3002s, and the software continues to prompt for a
username and password. This lets the VPN 3002 connect, even though it lacks a saved username and
password, and the adaptive security appliance has disabled interactive hardware client
authentication. If you subsequently configure a username and password, the feature is disabled, and
the prompt no longer appears. The VPN 3002 connects to the adaptive security appliance using the
saved username and password.
• Require Individual User Authentication—Enables or disables the requirement for individual user
authentication for users behind ASA 5505 in client mode or the VPN 3002 hardware client in the
group. To display a banner to hardware clients in a group, individual user authentication must be
enabled. This parameter is disabled by default.
Firewall Mode Security Context
Routed Transparent Single
Multiple
Context System
• — • ——

 Loading...
Loading...