5-17
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 5 Configuring the Transparent or Routed Firewall
Firewall Mode Examples
4. The adaptive security appliance then adds a session entry to the fast path and forwards the packet
from the DMZ interface.
5. When the DMZ web server responds to the request, the packet goes through the adaptive security
appliance and because the session is already established, the packet bypasses the many lookups
associated with a new connection. The adaptive security appliance performs NAT by translating the
local source address to 209.165.201.3.
6. The adaptive security appliance forwards the packet to the outside user.
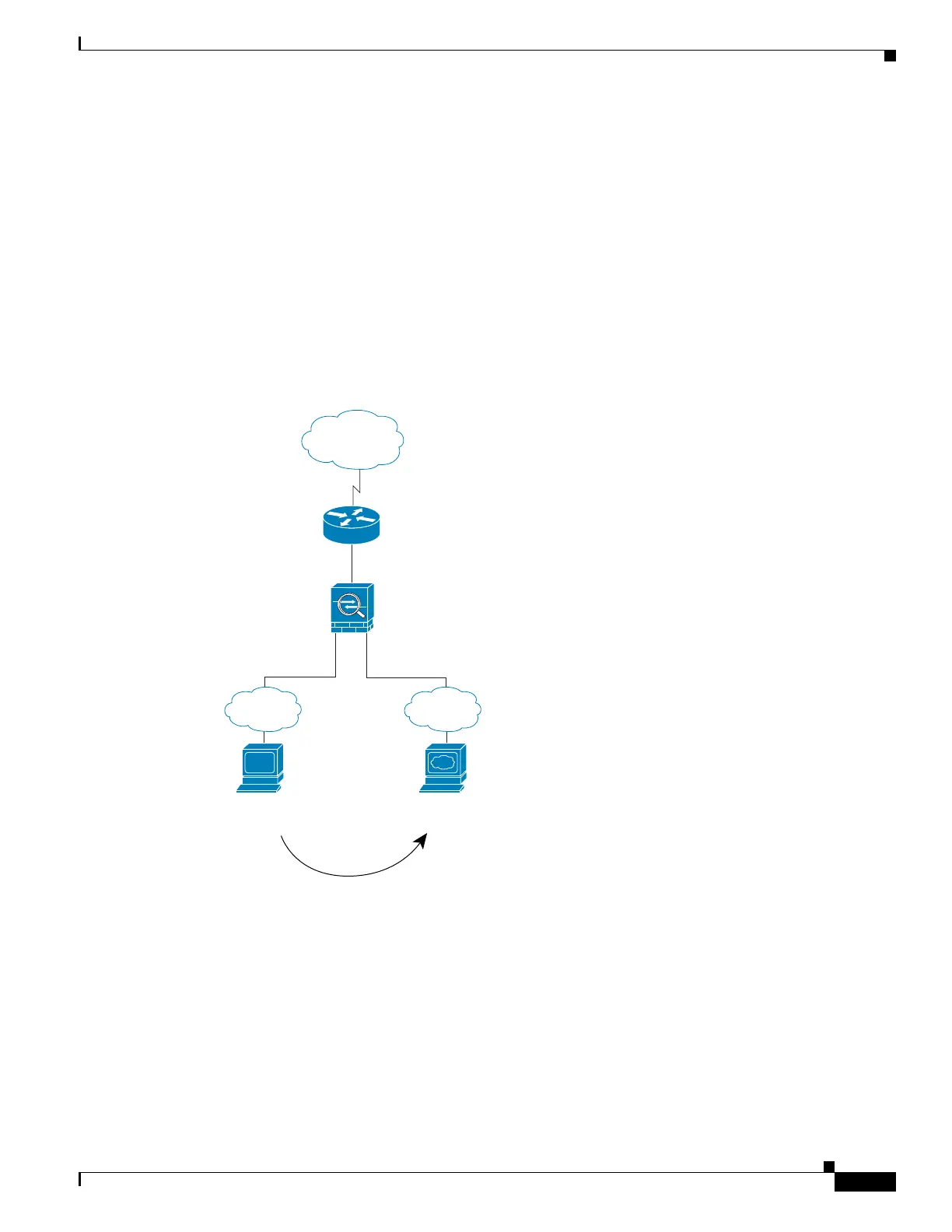
An Inside User Visits a Web Server on the DMZ
Figure 5-4 shows an inside user accessing the DMZ web server.
Figure 5-4 Inside to DMZ
The following steps describe how data moves through the adaptive security appliance (see Figure 5-4):
1. A user on the inside network requests a web page from the DMZ web server using the destination
address of 10.1.1.3.
2. The adaptive security appliance receives the packet and because it is a new session, the adaptive
security appliance verifies that the packet is allowed according to the terms of the security policy
(access lists, filters, AAA).
For multiple context mode, the adaptive security appliance first classifies the packet according to
either a unique interface or a unique destination address associated with a context; the destination
address is associated by matching an address translation in a context. In this case, the interface is
unique; the web server IP address does not have a current address translation.
Web Server
10.1.1.3
User
10.1.2.27
209.165.201.2
10.1.1.110.1.2.1
Inside DMZ
Outside
92403

 Loading...
Loading...