26-8
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 26 Information About NAT
NAT Types
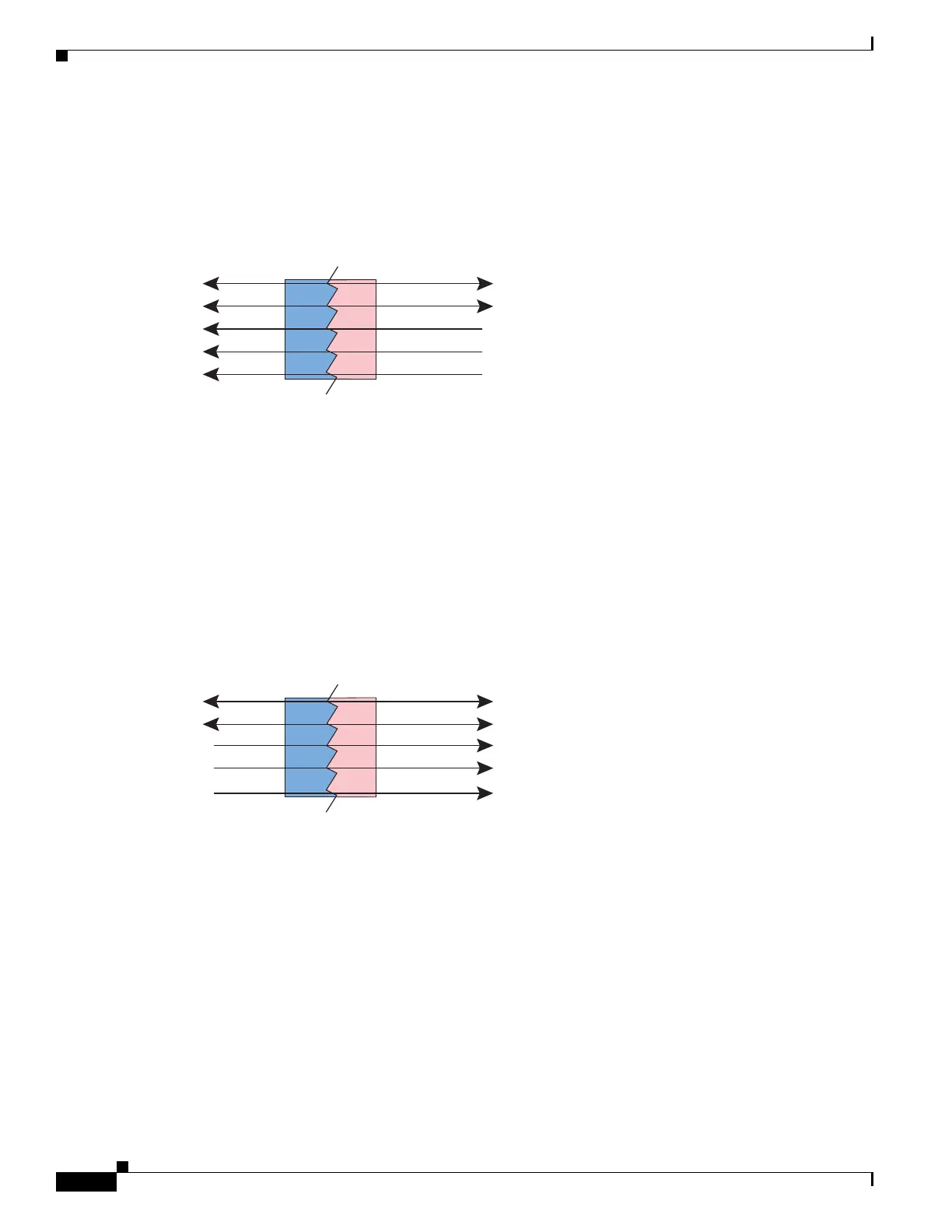
Figure 26-6 shows a typical few-to-many static NAT scenario. The first translation for each real address
is always active so both translated and remote hosts can initiate connections, but the subsequent
mappings are unidirectional to the real hosts.
Figure 26-6 Few-to-Many Static NAT
For a many-to-few or many-to-one configuration, where you have more real addresses than mapped
addresses, you run out of mapped addresses before you run out of real addresses. Only the initial
mappings result in bidirectional initiation. The remaining real addresses can initiate traffic, but traffic
cannot be initiated to them (returning traffic for a connection is directed to the correct real address
because of the unique 5-tuple (source IP, destination IP, source port, destination port, protocol) for the
connection).
Figure 26-7 shows a typical many-to-few static NAT scenario. The first translation for each mapped
address is always active so both translated and remote hosts can initiate connections, but the subsequent
mappings are unidirectional from the real hosts.
Figure 26-7 Many-to-Few Static NAT
Instead of using a static rule this way, we suggest that you create a one-to-one rule for the traffic that
needs bidirectional initiation, and then create a dynamic rule for the rest of your addresses.
Dynamic NAT
This section describes dynamic NAT and includes the following topics:
• Information About Dynamic NAT, page 26-9
• Dynamic NAT Disadvantages and Advantages, page 26-10
10.1.2.27 209.165.201.3
Inside Outside
10.1.2.28 209.165.201.4
10.1.2.27 209.165.201.5
10.1.2.28 209.165.201.6
10.1.2.27 209.165.201.7
Security
Appliance
248769
10.1.2.27 209.165.201.3
Inside Outside
10.1.2.28 209.165.201.4
10.1.2.29
209.165.201.3
10.1.2.30
209.165.201.4
10.1.2.31
209.165.201.3
Security
Appliance
248770

 Loading...
Loading...