5-7
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 5 Configuring the Transparent or Routed Firewall
Configuring the Firewall Mode
Setting the Firewall Mode
This section describes how to change the firewall mode using the CLI. You cannot change the mode in
ASDM.
Note We recommend that you set the firewall mode before you perform any other configuration because
changing the firewall mode clears the running configuration.
Prerequisites
When you change modes, the adaptive security appliance clears the running configuration (see the
“Guidelines and Limitations” section on page 5-5 for more information).
• If you already have a populated configuration, be sure to back up your configuration before changing
the mode; you can use this backup for reference when creating your new configuration.
• Use the CLI at the console port to change the mode. If you use any other type of session, including
the ASDM Command Line Interface tool or SSH, you will be disconnected when the configuration
is cleared, and you will have to reconnect to the adaptive security appliance using the console port
in any case.
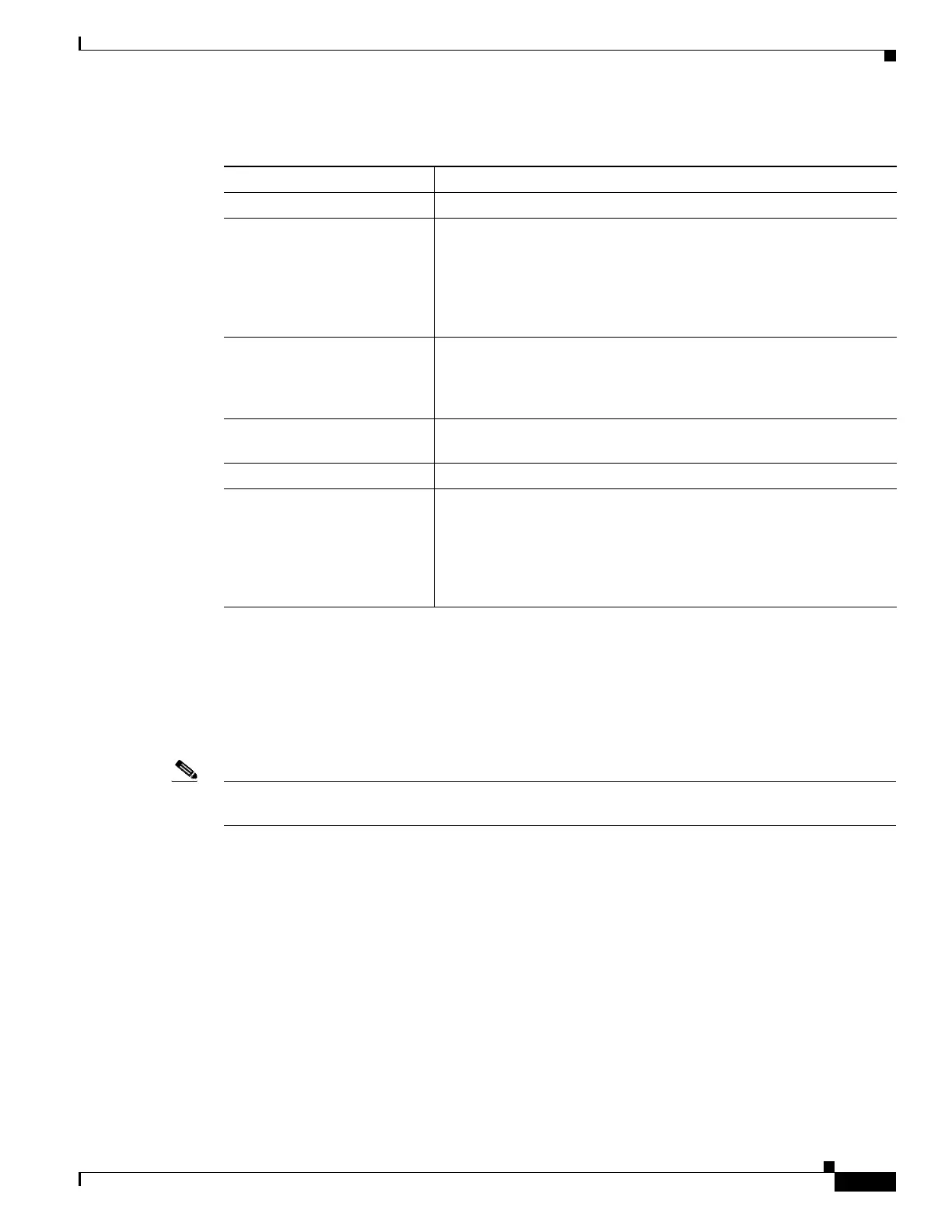
Table 5-1 Unsupported Features in Transparent Mode
Feature Description
Dynamic DNS —
DHCP relay The transparent firewall can act as a DHCP server, but it does not
support the DHCP relay commands. DHCP relay is not required
because you can allow DHCP traffic to pass through using two
extended access lists: one that allows DCHP requests from the inside
interface to the outside, and one that allows the replies from the server
in the other direction.
Dynamic routing protocols You can, however, add static routes for traffic originating on the
adaptive security appliance. You can also allow dynamic routing
protocols through the adaptive security appliance using an extended
access list.
Multicast IP routing You can allow multicast traffic through the adaptive security appliance
by allowing it in an extended access list.
QoS —
VPN termination for through
traffic
The transparent firewall supports site-to-site VPN tunnels for
management connections only. It does not terminate VPN connections
for traffic through the adaptive security appliance. You can pass VPN
traffic through the security appliance using an extended access list, but
it does not terminate non-management connections. SSL VPN is also
not supported.

 Loading...
Loading...