26-7
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 26 Information About NAT
NAT Types
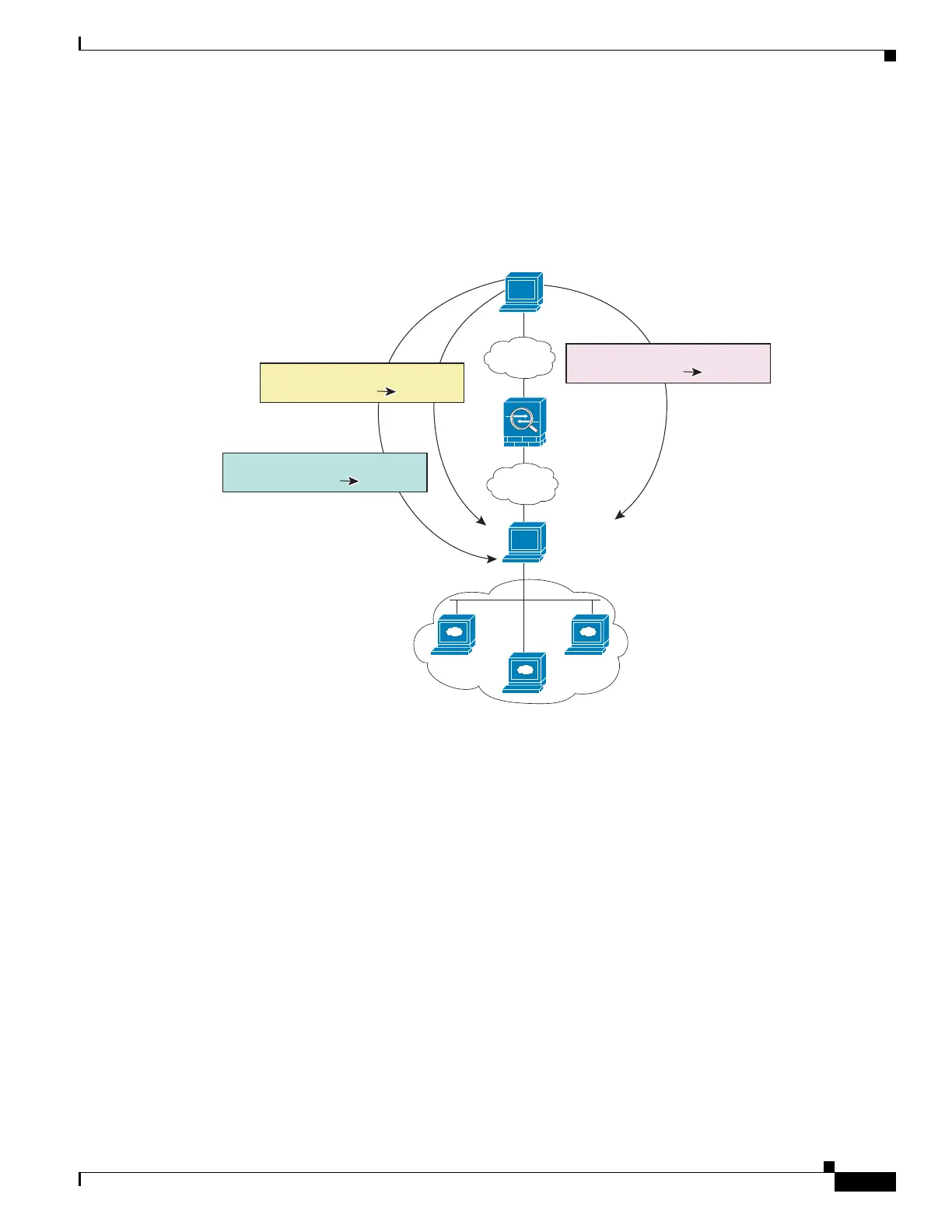
For example, you have a load balancer at 10.1.2.27; depending on the URL requested, it redirects traffic
to the correct web server. (See Figure 26-5. See the “Inside Load Balancer with Multiple Mapped
Addresses (Static NAT, One-to-Many)” section on page 27-25 for details on how to configure this
example.)
Figure 26-5 One-to-Many Static NAT
Information About Other Mapping Scenarios (Not Recommended)
The adaptive security appliance has the flexibility to allow any kind of static mapping scenario:
one-to-one, one-to-many, but also few-to-many, many-to-few, and many-to-one mappings. These other
mapping options, however, might result in unintended consequences. We recommend using only
one-to-one or one-to-many mappings.
Functionally, few-to-many is the same as one-to-many; but because the configuration is more
complicated, we recommend creating a one-to-many configuration for each real address that requires it.
For example, for a few-to-many scenario, the few real addresses are mapped to the many mapped
addresses in order (A to 1, B to 2, C to 3). When all real addresses are mapped, the next mapped address
is mapped to the first real address, and so on until all mapped addresses are mapped (A to 4, B to 5, C
to 6). This results in multiple mapped addresses for each real address. Just like a one-to-many
configuration, only the first mappings are bidirectional; subsequent mappings allow traffic to be initiated
to the real host, but all traffic from the real host uses only the first mapped address for the source.
Host
Outside
Inside
Load Balancer
10.1.2.27
Web Servers
Undo Translation
10.1.2.27209.165.201.3
Undo Translation
10.1.2.27209.165.201.4
Undo Translation
10.1.2.27209.165.201.5
248633

 Loading...
Loading...