64-48
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 64 General VPN Setup
Configuring SSL VPN Connections
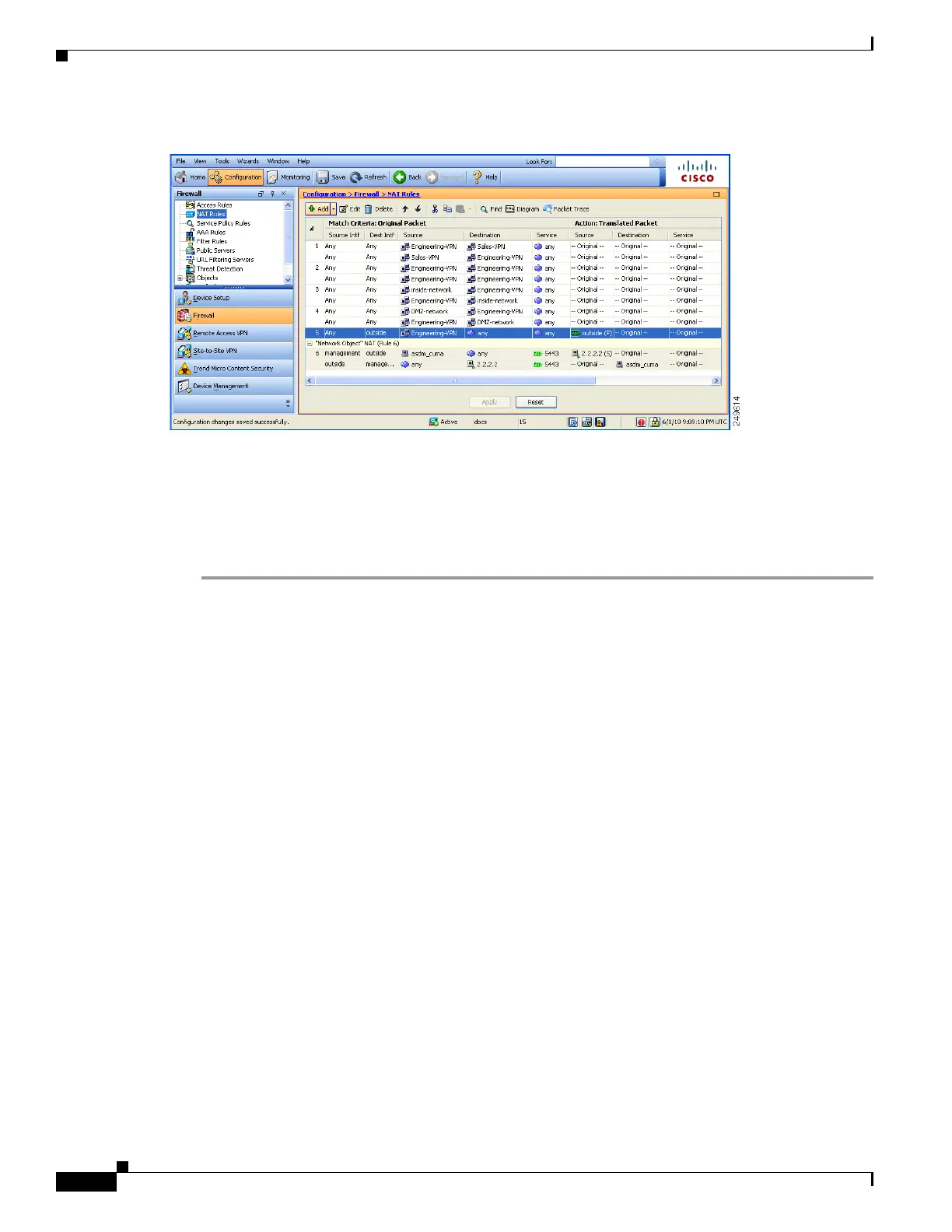
Figure 64-5 Unified NAT table
Step 8 After you have configured the Engineering VPN Address pool to reach itself, the Sales VPN address
pool, the inside network, the DMZ network, and the Internet; you must repeat this process for the Sales
VPN address pool. Use identity NAT to exempt the Sales VPN address pool traffic from undergoing
network address translation between itself, the inside network, the DMZ network, and the Internet.
Step 9 From the File menu on the ASA, select Save Running Configuration to Flash to implement your
identity NAT rules.
Configuring SSL VPN Connections
Use the AnyConnect Connection Profiles pane and its child dialog boxes to specify SSL VPN connection
attributes for client-based connections. These attributes apply to the Cisco AnyConnect VPN client and
to the legacy SSL VPN client.
The initial client deployment requires end-user administrative rights. The Cisco AnyConnect VPN client
supports the HTTPS/TCP (SSL) and Datagram Transport Layer Security (DTLS) tunneling options.
In the main pane, you can enable client access on the interfaces you select and you can select, add, edit,
and delete connections (tunnel groups). You can also specify whether you want to allow a user to select
a particular connection at login.
Fields
• Access Interfaces—Specify SSL VPN client access for each interface listed in the table:
–
Enable Cisco AnyConnect VPN Client or legacy SSL VPN Client access on the interfaces in the
table below—Check this check box to enable the AnyConnect VPN client or the legacy SSL
VPN client on the interfaces listed in the Access Interfaces table.
–
Interface—The interface to enable SSL VPN client connections.
–
Allow Access—Check Allow Access to enable access on the interfaces listed in this table.
–
Enable DTLS—Check Enable DTLS to enable Datagram Transport Layer Security (DTLS) on
an interface. DTLS avoids latency and bandwidth problems associated with some SSL
connections and improves the performance of real-time applications that are sensitive to packet
delays.

 Loading...
Loading...