30-4
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 30 Configuring Access Rules
Information About Access Rules
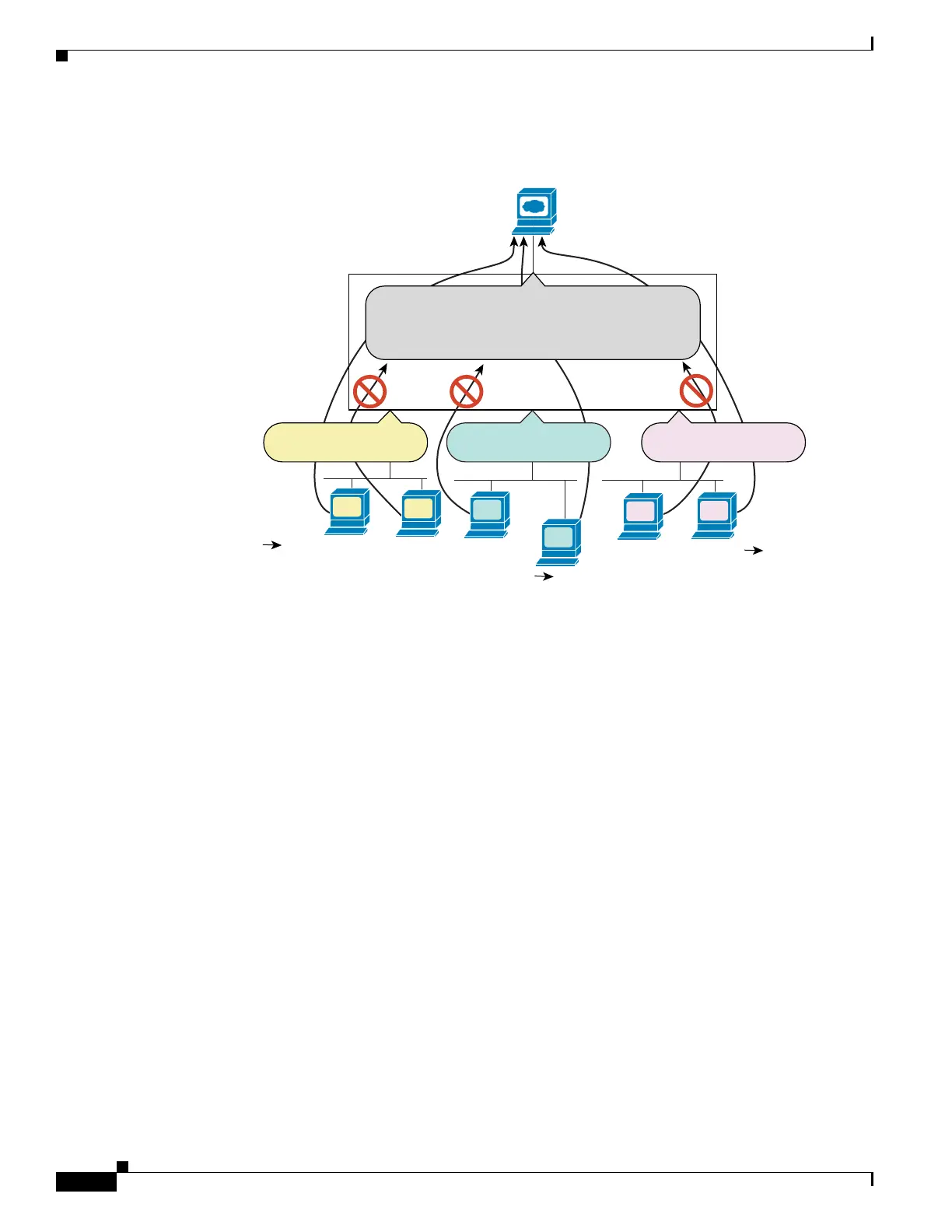
Figure 30-1 Outbound Access List
Using Global Access Rules
Global access rules allow you to apply a global rule to ingress traffic without the need to specify an
interface to which the rule must be applied. Using global access rules provides the following benefits:
• When migrating to the adaptive security appliance from a competitor appliance, you can maintain a
global access rule policy instead of needing to apply an interface-specific policy on each interface.
• Global access control policies are not replicated on each interface, so they save memory space.
• Global access rules provides flexibility in defining a security policy. You do not need to specify
which interface a packet comes in on, as long as it matches the source and destination IP addresses.
• Global access rules use the same mtrie and stride tree as interface-specific access rules, so
scalability and performance for global rules are the same as for interface-specific rules.
You can configure global access rules in conjunction with interface access rules, in which case, the
specific interface access rules are always processed before the general global access rules.
Information About Access Rules
This section describes information about access rules and includes the following topics:
• Access Rules for Returning Traffic, page 30-5
• Allowing Broadcast and Multicast Traffic through the Transparent Firewall Using Access Rules,
page 30-5
Web Server:
209.165.200.225
Inside
HR
Eng
Outside
Static NAT
209.165.201.410.1.1.14
Static NAT
209.165.201.610.1.2.67
Static NAT
209.165.201.810.1.3.34
ACL Outbound
Permit HTTP from 209.165.201.4, 209.165.201.6,
and 209.165.201.8 to 209.165.200.225
Deny all others
132210
ACL Inbound
Permit from any to any
ACL Inbound
Permit from any to any
ACL Inbound
Permit from any to any
Security
appliance

 Loading...
Loading...